Tips & Tricks
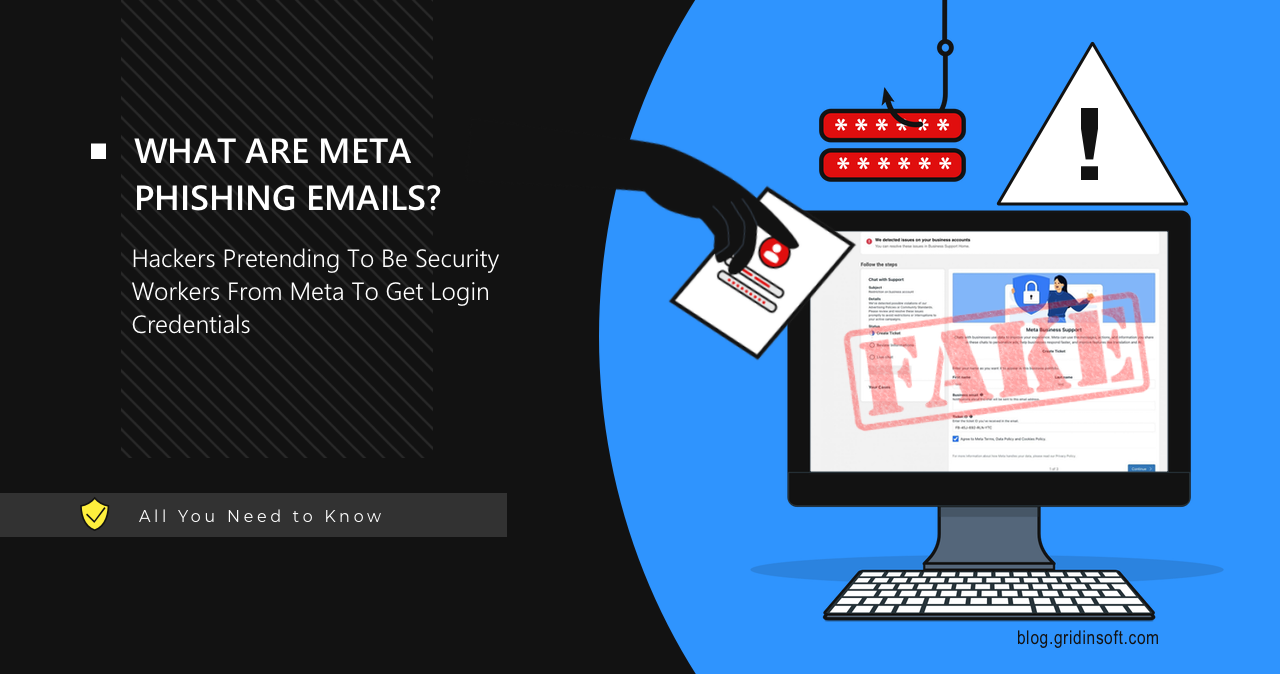
Meta Security Email Phishing Scams Explained
Attackers are targeting users of Meta services with phishing attacks. Classic fraud schemes are gaining momentum once again, with users…
Opera GX
Opera GX is a special version of the Opera browser with extra features tailored for gamers. However, malicious, weaponized versions…
Aruba.it Email Scam
The Aruba.it email scam is a phishing campaign using fake emails that appear to be from Aruba S.p.A., a well-known…
Verify you are Human Scam
While browsing the Web, you can occasionally get to a page that says “Verify you are human”, and offers doing…
Arma dei Carabinieri Virus
The *Arma dei Carabinieri* message is a banner that may appear on your PC, attempting to mimic notifications from Italy’s…
Chromstera Browser
Chromstera Browser a rogue browser that mimics Google Chrome, and…
Reset Browser Chrome, Opera, Edge, Firefox and Safari to Default
Browser performance issues, unwanted redirects, and strange behavior are common…
Universal Browser
Universal Browser is a name of a browser that users…
Wave Browser
Wave Browser is an unwanted browser application that tries to…
eBay Scams
Among the vast amount of online shopping platforms, eBay stands…
PUA:Win32/Conduit
PUA:Win32/Conduit is a potentially unwanted application that performs suspicious activity…
Adaware Web Companion
Web Companion is an unwanted program works as a web…
PUA:Win32/MyWebSearch
PUA:Win32/MyWebSearch is a Microsoft Defender detection that refers to an…
Walliant App
The Walliant application is a Potentially Unwanted Application (PUA). It…
Dragon Angel Malicious Browser Extension
Dragon Angel is a browser extension that functions as a…
Re-Captha-Version Pop-Up Virus
Recent user complaints show a new wave of malicious Re-Captha-Version…
Taskbarify Unwanted Application
Taskbarify is unwanted software (like a Movidown)that claims it is…