Tips & Tricks
How Can Companies Be Secure Against Cyberattacks?
Organizations face an alarming reality in the digital world: data breaches and cyberattacks are becoming more frequent. Cybercriminals find more…
Malware Propagation On Darknet Forums
The forums on the dark web are well-known for being a hub of cybercriminal activity, including an auction system. Here,…
Credentials Theft is On The Rise
Email spam has become the prevalent form of phishing and malware spreading for a long time. Among them, credentials theft…
How to Protect Your Digital Footprint
The modern business world has been greatly advanced by the internet. Its convenience and numerous benefits have made people from…
RDP Honeypot Was Attacked 3.5 Million Times
With increased remote work, IT teams use remote access tools to manage company devices and ensure smooth operations. Remote desktop…
6 Popular Types of Hackers: Protection Tips in 2022
The internet has given us many wonderful things: smart homes, NFTs, cryptocurrency, and more. Without our connection to the internet, the world would be a much different place today. Unfortunately,…
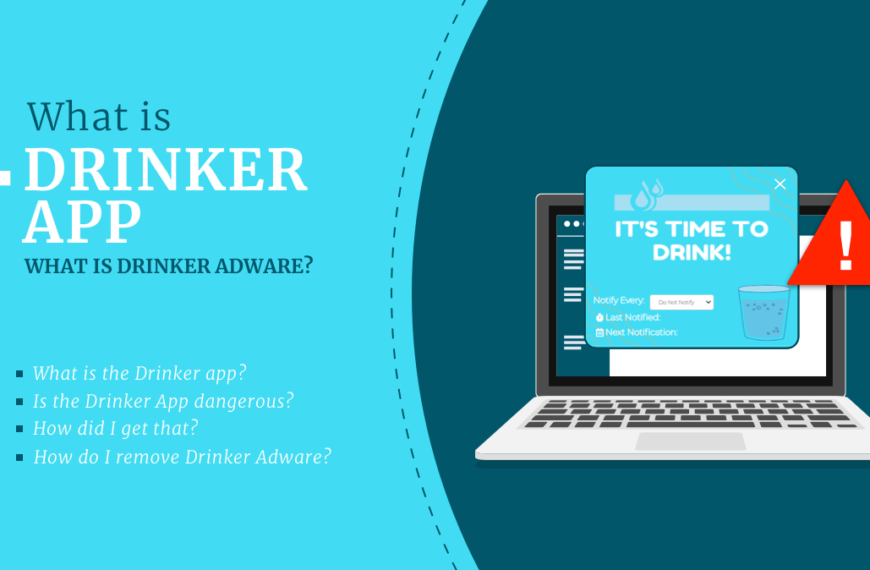
Drinker App – what is Drinker Adware?
The Drinker app is another example of a malicious program that disguises itself as a useful utility for your PC. Another two – Healthy and Strength – popped up almost…
10 Reasons to Choose GridinSoft Trojan Killer
We used to think of anti-malware software as a program that features all kinds of supplementary services. VPN plan, disk encryption tool, guest mode and parental control – all of…
Healthy App (HealthySoftware) – What is Healthy?
Healthy App seems to be the companion of the other unwanted app – Strength Adware. The dubious application gets into users’ PCs to show them tons of advertisements. Let’s check…
Strength Adware – What Is Strength App?
Strength Adware, a new advertising malware, began appearing on users’ devices. It is still not clear how it manages to get into the system, but its effects are not pleasant.…
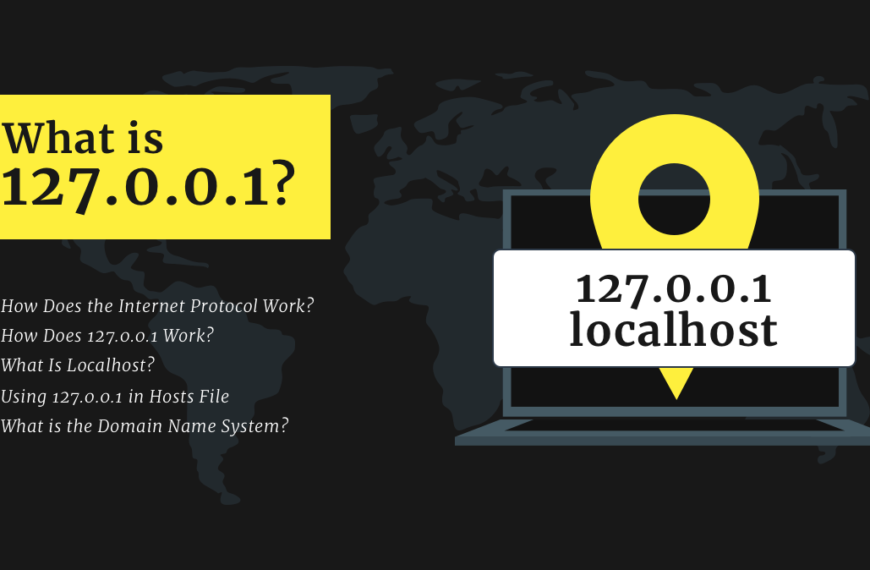
What is 127.0.0.1?
127.0.0.1. You could see it here and there. It appears in memes, on t-shirts as well as in tech documentation. However, what is it, and why is it so famous?…
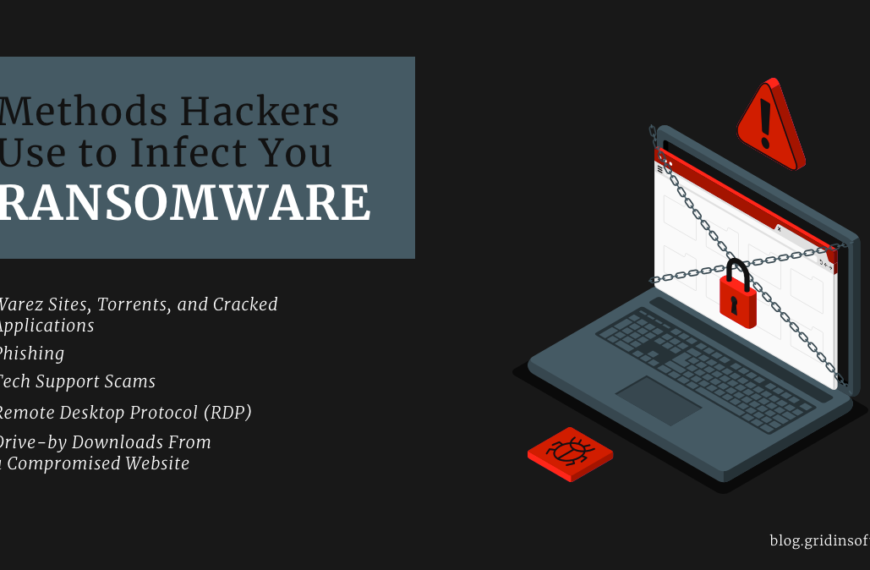
Methods Hackers Use to Infect You Ransomware
Ransomware hits the headlines almost daily. And most incidents target large corporations with enough capital to justify the attack. But sometimes ordinary people get infected as well. Some attackers choose…
Can Someone Track My Device When Location Settings Off?
Any smartphone already has built-in location tracking services. At the beginning location tracking was created for navigation, but it was later used for other purposes. This feature is very convenient…
How To Know If Your Phone is Hacked?
If your phone stopped working correctly and started showing obvious performance errors, then something is wrong. If you notice that your smartphone has begun to turn itself off or on,…
Spam Phone Calls Revenge: Prevent Spam Risk Phone Calls
Statistics show that an average of 1,900 spam calls are made every second. Given recent statistics about it, it is clear that it is another problem in the head of…
How to Stop Spam Texts: Tips to Deal With Fake Text Message
The spam texts can include spam emails and spam calls. These are all unwanted and often annoying text messages whose sender you don’t know. The purpose of such spam is…
“Your Account Has Been Locked”: Top 5 Signs of a Phishing Scam
The topic of our article will be how to understand that you have become a victim of a phishing attack. Below, you will learn what is discussed in our main…