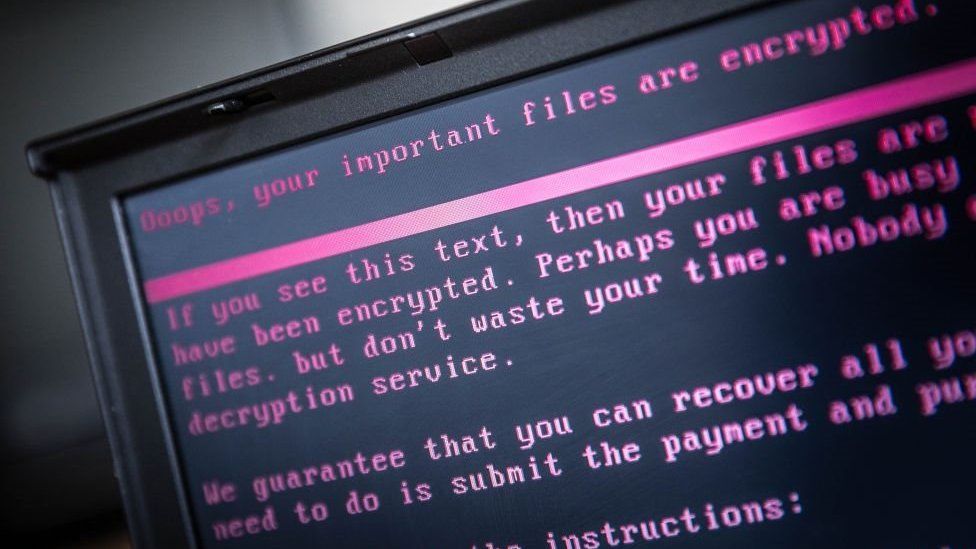
Copyright Claims Used as Bait by LockBit 2.0 Affiliates in Korea
A new type of email-bait has been invented by the affiliates of…
NCC Group’s May 2022 Threat Report Reflects Conti’s End
NCC Group's monthly report on cyber threats features some curious news, namely…
Chinese Hackers Use Ransomware As a Cover for Espionage
Secureworks experts have found that Chinese hackers from two groups that specialize…
Ryuk – Devastatingly Effective Targeted Ransomware
Ransomware is a malicious program which an attacker injects into your device…
QNAP Warns Clients About DeadBolt Ransomware Attacks
DeadBolt Ransomware: Another Instance of Ransomware Evolution On June 17, QNAP, the…
Companies Manage to Bargain With Ransomware Racketeers
Revelations of the Ransom-Negotiator In May, the racketeer-bargaining specialist (the negotiator) at…
BlackCat ransomware gang publishes leaked data on the clear web site
BlackCat/ALPHV group recently announced on its victim shaming and extortion website that…
War in Ukraine triggered a Stream of amateurish ransomware
Russia has provoked hackers around the world to focus their attacks on…
BlackCat Ransomware Attacks Italian University
An Italian university was hit by BlackCat this week. The hackers demand…
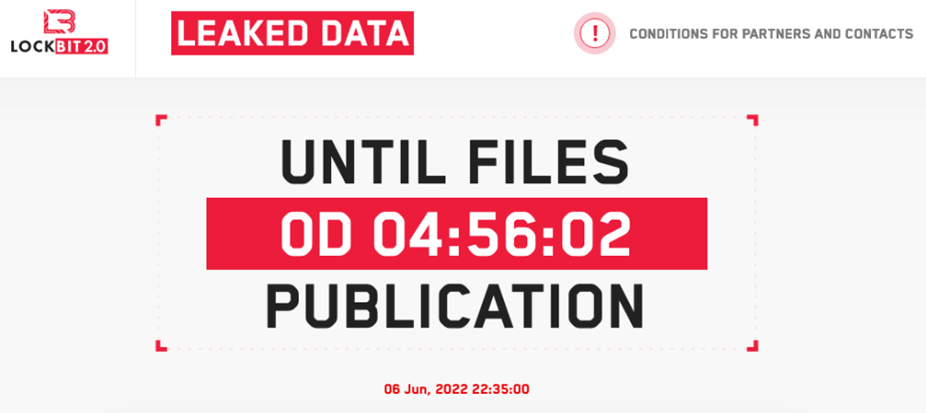
LockBit 2.0 Promises to Leak Mandiant Data
LockBit 2.0 announcement: real thing or vengeful trolling? On June 6, on…
New Cuba Ransomware Variant Involves Double-Extortion Scheme
What's new in April Variant of Cuba Ransomware The Cuba ransomware family…
Evil Corp Switched to Using LockBit Malware to Avoid Sanctions
The Evil Corp group switched to using the LockBit ransomware to avoid…