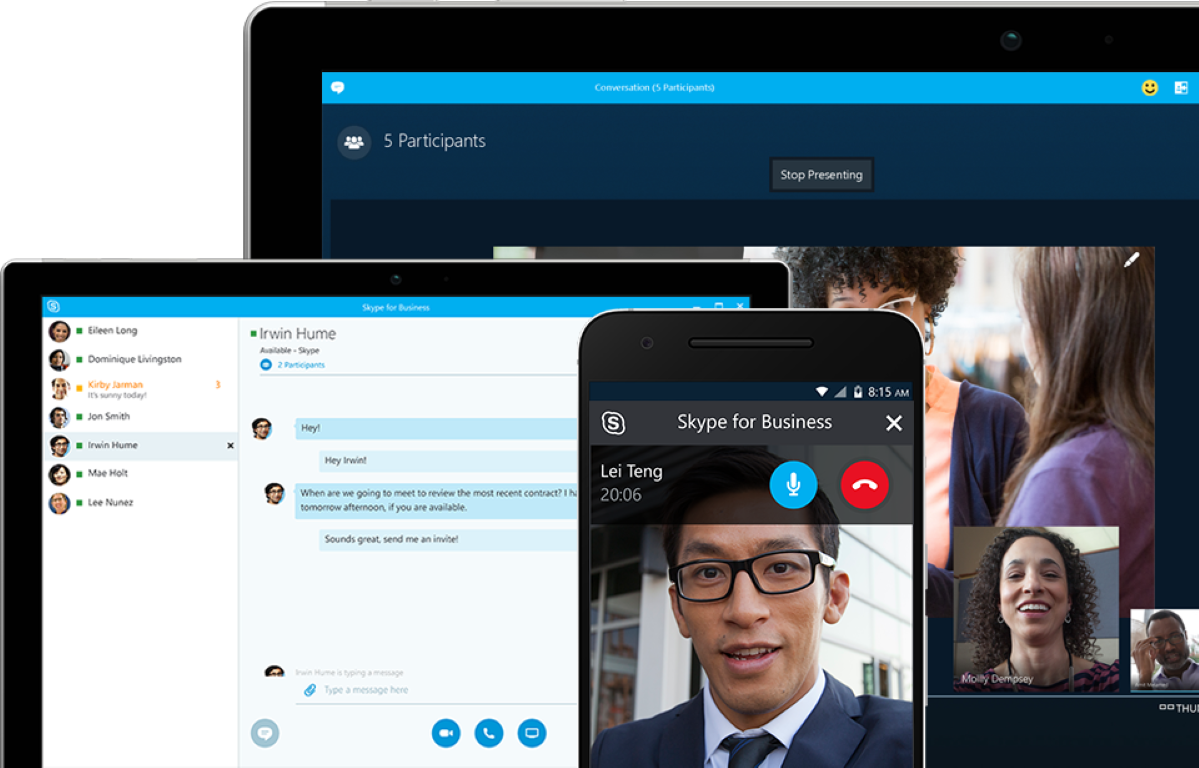
VirusTotal analysts presented a report on the methods that malware operators use to bypass protection and increase the effectiveness of social engineering. The study showed that attackers are increasingly imitating legitimate applications such as Skype, Adobe Reader and VLC Player to gain the trust of victims. Let me remind you that we also wrote that… Continue reading Most Often, Malware to Bypass Protection Impersonates Skype, Adobe Acrobat and VLC
Tag: Microsoft
Microsoft Links Raspberry Robin Worm to Evil Corp
Microsoft analysts have noticed that the access broker, which the company tracks as DEV-0206, is using the Raspberry Robin Windows worm to deploy the malware loader on networks where traces of malicious activity by Evil Corp are also detected. Let me remind you that we also wrote that The Austrian Company DSIRF Was Linked to… Continue reading Microsoft Links Raspberry Robin Worm to Evil Corp
The Austrian Company DSIRF Was Linked to the Knotweed Hack Group and the Subzero Malware
Microsoft has been told that the Knotweed hack group is linked to the Austrian spyware vendor DSIRF, which also often acts as a cyber mercenary. Researchers have determined that Knotweed is attacking European and Central American organizations using the Subzero malware toolkit. Let me remind you that we also wrote that Experts linked BlackCat (ALPHV)… Continue reading The Austrian Company DSIRF Was Linked to the Knotweed Hack Group and the Subzero Malware
Microsoft Releases PoC Exploit to Escape MacOS Sandbox
Microsoft has detailed a recently patched vulnerability affecting Apple operating systems and published a PoC exploit to escape the macOS sandbox. If successfully exploited, this bug allows to leavei the sandbox, elevate privileges on the device and deploy malware. Let me remind you that they also wrote that Vulnerability in macOS Leads to Data Leakage,… Continue reading Microsoft Releases PoC Exploit to Escape MacOS Sandbox
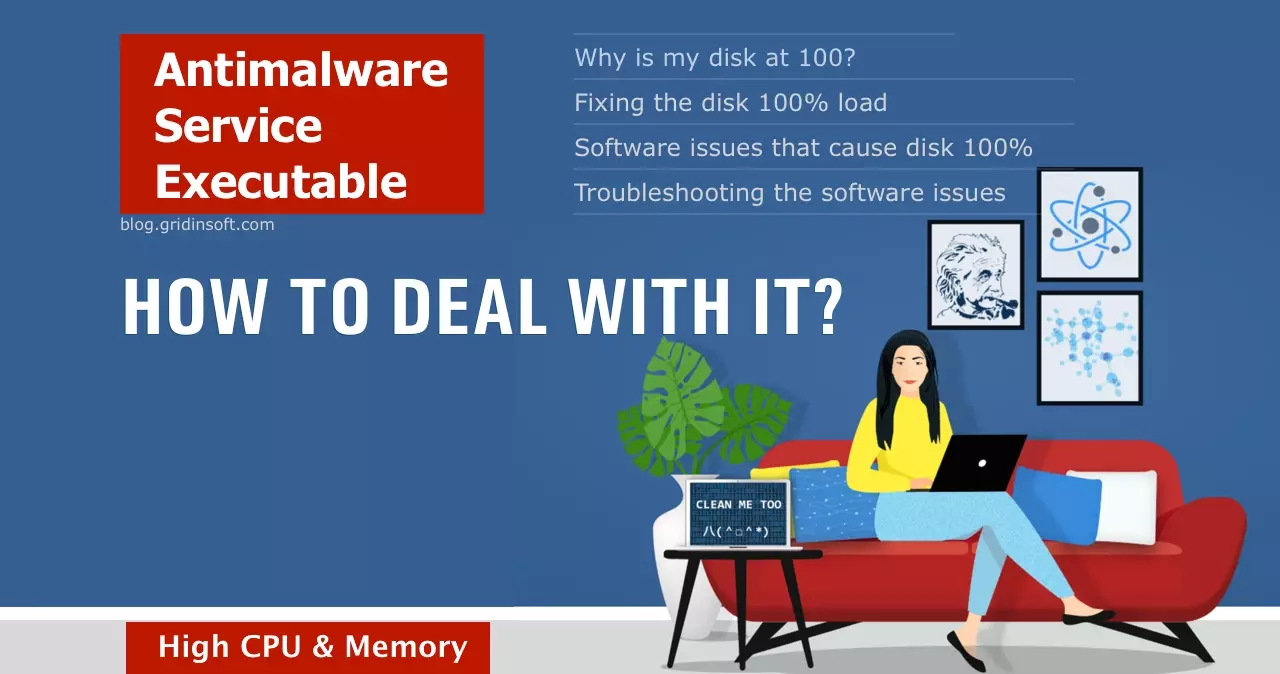
Antimalware Service Executable
Windows Defender is a decent antivirus solution that comes in a package with Windows 10 and Windows 11. There were many controversies about its efficiency and quality, which are still heard now. In this article, we’ll be dealing with one of the most rebuked traits of Windows Defender – its tremendous resource consumption. Namely, we… Continue reading Antimalware Service Executable
Phishers Can Bypass Multi-Factor Authentication with Microsoft Edge WebView2
An information security expert known as mr.d0x has developed a new attack technique that abuses Microsoft Edge WebView2 applications to steal authentication cookies. In theory, this allows bypassing multi-factor authentication when logging into stolen accounts. Read also: 10 Ways To Recognize and Avoid Phishing Scams. The new attack technique is called WebView2-Cookie-Stealer and consists of… Continue reading Phishers Can Bypass Multi-Factor Authentication with Microsoft Edge WebView2
Microsoft Accuses Russia of Cyberattacks against Ukraine’s Allies
In the latest report on global information security, Microsoft accuses Russia of massive cyberattacks in connection with the war in Ukraine. It states that Russian hackers have carried out numerous cyber-espionage operations against Ukraine’s allied countries since the start of Russia’s full-scale invasion of Ukraine. Let me remind you that we reported that Hacker groups… Continue reading Microsoft Accuses Russia of Cyberattacks against Ukraine’s Allies
Microsoft Has Already Patched a Vulnerability in Windows RDP Twice
This week, CyberArk researchers shared technical information about a named pipe RDP (Remote Desktop Protocol) vulnerability in Windows, for which Microsoft had to release two patches. The RCE vulnerability CVE-2022-21893 was fixed on January 2022 Patch Tuesday, but the attack vector was not fixed. In April 2022, Microsoft already fixed the new bug CVE-2022-24533. Let… Continue reading Microsoft Has Already Patched a Vulnerability in Windows RDP Twice
Internet Explorer shutdown. The Epithaf
On June 15, Microsoft will finally end support for Internet Explorer on various versions of Windows, almost 27 years after its launch on August 24, 1995. The desktop version of IE will be disabled and replaced with the new Microsoft Edge, with users automatically redirected to Edge when they launch Internet Explorer 11. Internet Explorer… Continue reading Internet Explorer shutdown. The Epithaf
Microsoft Fixed Follina Vulnerability and 55 Other Bugs
As part of the June Patch Tuesday, Microsoft finally fixed the Follina Critical Vulnerability associated with Windows MSDT, and fixed 55 more bugs in its products. As a reminder, Follina (CVE-2022-30190) is a remote code execution issue in the Microsoft Windows Support Diagnostic Tool (MSDT) and affects all versions of Windows that receive security updates… Continue reading Microsoft Fixed Follina Vulnerability and 55 Other Bugs