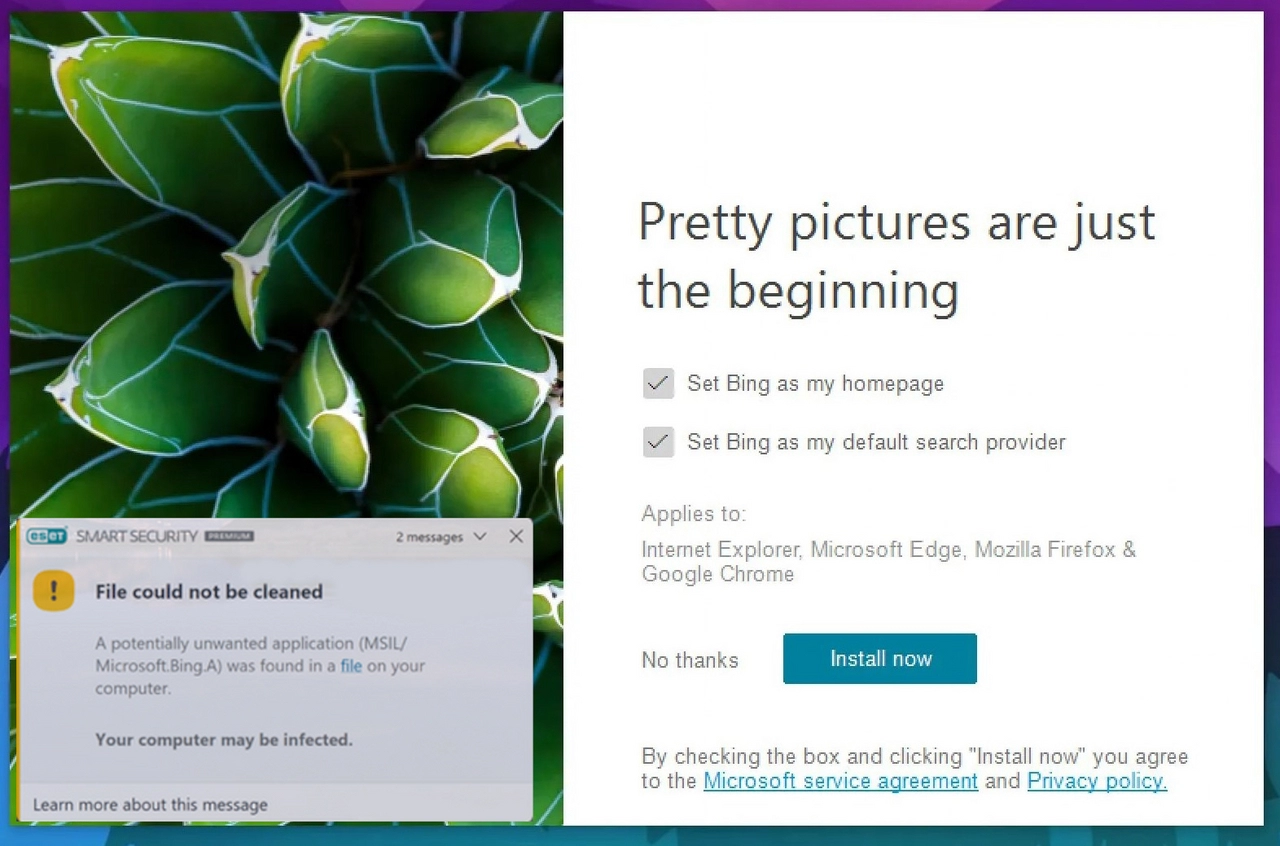
A lot of users on different forums complain about MSIL/Microsoft.Bing.A detection in ESET antivirus. This detection points to BingWallpaper.exe file – the benevolent file that belongs to Windows and is issued by Microsoft. But how could that happen – a 100% legit element marked as malicious? Let’s have a look at that story. What is… Continue reading MSIL/Microsoft.Bing.A Detection (BingWallpaper.exe)
Tag: Microsoft
Emotet Botnet Resumed Activity after Five Months of Inactivity
The Emotet botnet resumed activity and began sending out malicious spam again after a five-month break, during which the malware practically “lay low.” So far, Emotet is not delivering additional payloads to the infected devices of victims, so it is not yet possible to say exactly what this malicious campaign will lead to. Let me… Continue reading Emotet Botnet Resumed Activity after Five Months of Inactivity
Raspberry Robin Worm Operators Now Trade Access
Microsoft researchers reported that the operators of the hack group, which they track under the ID DEV-0950, used the Clop ransomware to encrypt the network of a victim previously infected with the Raspberry Robin worm. Let me remind you that the first Raspberry Robin malware was found by analysts from Red Canary. In the spring… Continue reading Raspberry Robin Worm Operators Now Trade Access
Microsoft Links Hacker Group Vice Society to Several Ransomware Campaigns
Microsoft experts have published a report on the hacker group Vice Society (aka DEV-0832), which uses ransomware to attack the educational sector in the US and other countries around the world. According to experts, the attackers are switching between using BlackCat, QuantumLocker, Zeppelin ransomware and another variant of Zeppelin, which is used under the “brand”… Continue reading Microsoft Links Hacker Group Vice Society to Several Ransomware Campaigns
Weak Block Cipher in Microsoft Office 365 Leads to Message Content Disclosure
WithSecure (formerly F-Secure Business) researchers claim that the content of encrypted messages sent through Microsoft Office 365 can be partially or completely disclosed due to the use of a weak block cipher. Although the experts received a bug bounty for their discovery, no fix for this problem is expected, and Microsoft has stated that they… Continue reading Weak Block Cipher in Microsoft Office 365 Leads to Message Content Disclosure
Another 0-Day Bug Was Found in Microsoft Exchange, and LockBit Ransomware Operators Are Exploiting It
Although Microsoft still hasn’t fixed the ProxyNotShell vulnerabilities found in Exchange last month, the company is now investigating a report of a new 0-day bug that is being used to compromise Exchange servers. Hackers are exploiting this bug to deploy the LockBit ransomware. Let me remind you that we also wrote that ProxyToken Vulnerability Allows… Continue reading Another 0-Day Bug Was Found in Microsoft Exchange, and LockBit Ransomware Operators Are Exploiting It
Hundreds of Microsoft SQL Servers Infected with Maggie Backdoor
Security researchers have discovered a new malware that targets Microsoft SQL servers. The backdoor is dubbed Maggie, has already infected hundreds of machines around the world. The greatest distribution of malware is observed in South Korea, India, Vietnam, China, Russia, Thailand, Germany and the USA. Let me remind you that we also wrote that Fargo… Continue reading Hundreds of Microsoft SQL Servers Infected with Maggie Backdoor
Gamaredon Hack Group Uses New Malware to Attack Ukrainian Organizations
Cisco Talos analysts write that the Russian-speaking hack group Gamaredon (aka Primitive Bear, Shuckworm, IronTiden and Callisto) is attacking Ukrainian organizations with the help of a new infostealer. The targets of this campaign are employees of the Ukrainian state, defense and law enforcement agencies. Let me remind you that we also wrote that Hacker groups… Continue reading Gamaredon Hack Group Uses New Malware to Attack Ukrainian Organizations
Developer of CodeRAT Trojan Releases Source Code
The source code for the CodeRAT remote access trojan has been published on GitHub. This happened after the security researchers identified the malware developer and called him to account because of the attacks in which this “tool” was used. SafeBreach experts say that the attacks using CodeRAT were built as follows: the campaign was aimed… Continue reading Developer of CodeRAT Trojan Releases Source Code
Janet Jackson Song Killed Hard Drives on Old Laptops
Microsoft specialist Raymond Chen shared an interesting story from the Windows XP era on the blog: the music video for Janet Jackson’s “Rhythm Nation” negatively affects some 5400 rpm hard drives, causing their malfunction. Let me remind you that we also talked about a curios fact when it turned out that: Cellmate men’s chastity belts… Continue reading Janet Jackson Song Killed Hard Drives on Old Laptops