Security researchers have discovered a new malware that targets Microsoft SQL servers. The backdoor is dubbed Maggie, has already infected hundreds of machines around the world. The greatest distribution of malware is observed in South Korea, India, Vietnam, China, Russia, Thailand, Germany and the USA.
Let me remind you that we also wrote that Fargo Ransomware aims at vulnerable Microsoft SQL servers, and also that Epsilon Red ransomware threatens Microsoft Exchange servers.
DCSO CyTec experts report that the malware is disguised as an Extended Stored Procedure DLL (sqlmaggieAntiVirus_64.dll) digitally signed by DEEPSoft Co. Ltd, which appears to be based in South Korea.
Maggie is controlled using SQL queries that tell it to execute certain commands or interact with files. The malware is also capable of brute forcing administrator credentials to penetrate other Microsoft SQL servers.
Extended Stored Procedure files extend the functionality of SQL queries by using an API that accepts remote user arguments and responds with unstructured data. As a result, the list of commands supported by the backdoor looks quite impressive.
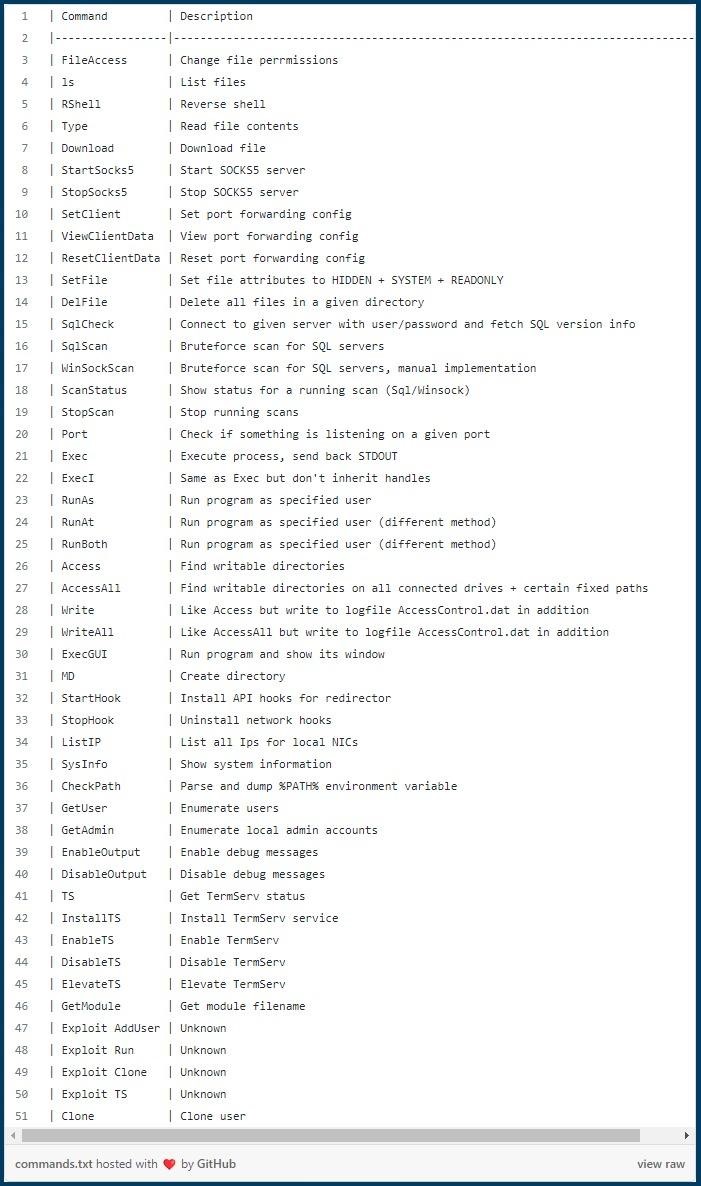
So, Maggie can request system information, run programs, interact with files and folders, enable remote desktop services (TermService), start a SOCKS5 proxy server, and set up port forwarding.
The researchers note that the command list also contains four “Exploit” commands, which means that attackers may rely on exploiting known vulnerabilities to perform certain actions, such as adding a new user. Unfortunately, we were unable to study these exploits, as they seem to depend on an additional DLL and are not shipped with Maggie.
The SqlScan and WinSockScan commands are responsible for brute-forcing administrator passwords, which are executed after defining a file with a list of passwords and the number of threads. If successful, a new hard-coded user appears on the server.
The researchers’ report also notes that the malware has a simple TCP redirect feature that helps attackers connect to any IP address available to the infected MS-SQL server.
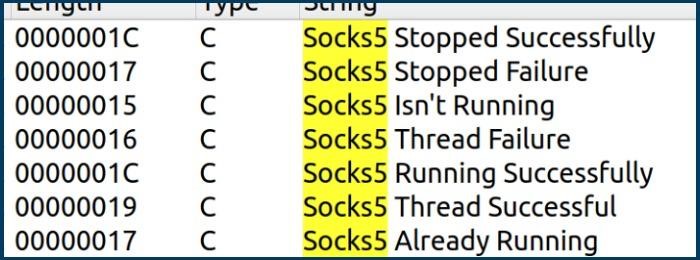
In addition, the backdoor has SOCKS5 proxy functionality that can be used to route all network packets through the proxy, making the threat even more invisible if needed.
Currently, it remains unclear how exactly hackers use Maggie after infection, how the malware is introduced to servers at all, and who is behind these attacks.




