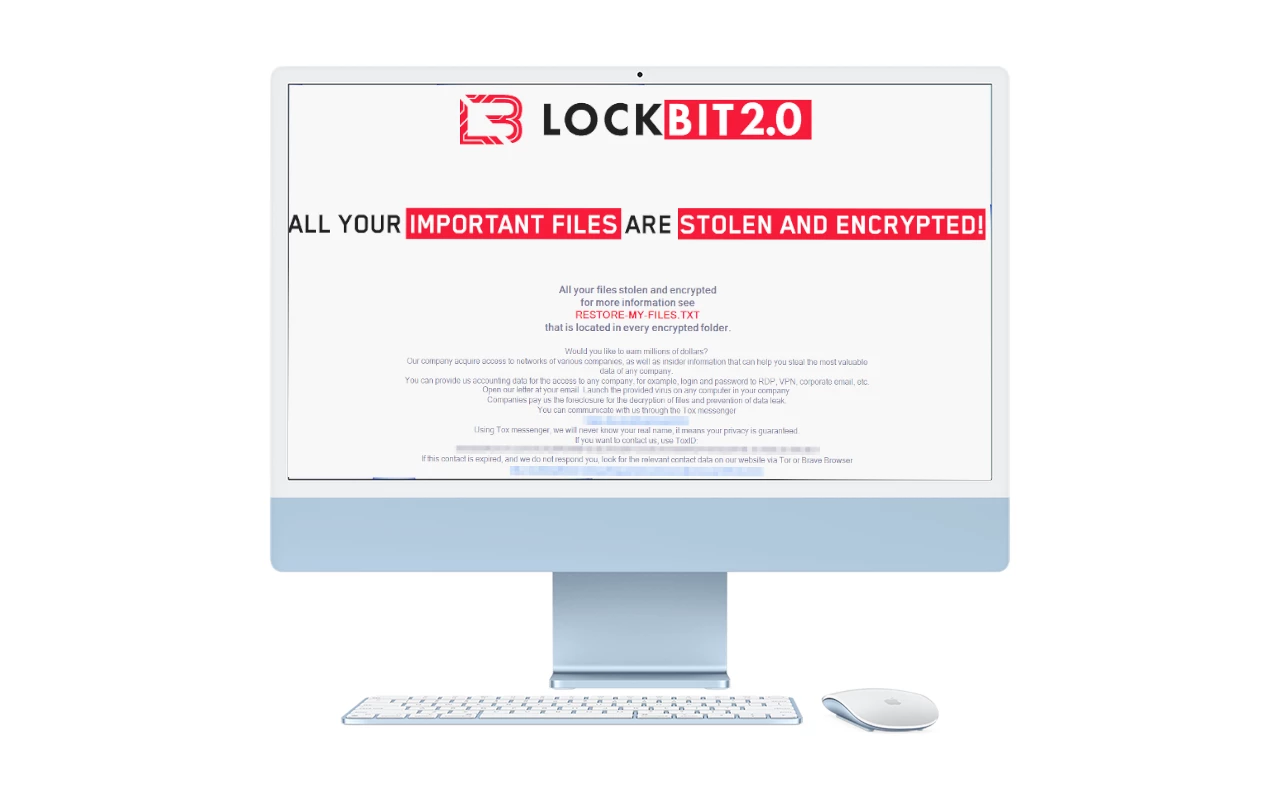
LockBit, an infamous ransomware gang that became a major threat actor over the last two years, released the variant of its ransomware for macOS. Previously, this system was considered safe from ransomware, as no known samples were targeting it specifically. Currently, LockBit’s product is considered the first ransomware that breaks that rule. What is the… Continue reading LockBit Releases World’s First macOS Ransomware
Tag: Cybersecurity
Domino Backdoor is Lead by FIN7 and Conti Actors
A new Domino Backdoor popped out at the beginning of 2023. Since February, a new malware family coined Domino is used for attack on corporations, having Project Nemesis stealer as a final payload. Analysts say that the new backdoor is controlled and developed by ex-TrickBot/Conti actors and hackers related to the FIN7 group. Who are… Continue reading Domino Backdoor is Lead by FIN7 and Conti Actors
PDF Virus
Among numerous other files, PDFs are considered one of the most convenient to use for read-only documents. They prevent editing the content, yet retain the ability to carry interactive content. But is it totally safe? Can a PDF have a virus? Let’s find out. Background of PDF Virus First things first, so let’s see the… Continue reading PDF Virus
Genesis Market Seized by FBI
Genesis Market, a Darknet marketplace for stolen information, was reportedly seized by the FBI on Tuesday, April 4, 2023. The operation was likely preceded by the detainment of the market’s significant actors. The overall operation is called “Cookie Monster”. What is Genesis Market? Genesis is a Darknet marketplace that has been active since 2018. Aside… Continue reading Genesis Market Seized by FBI
Ransomware Actors Target IBM’s Aspera Faspex
File transfer utility Aspera Faspex, developed by IBM, became a riding mare of cybercriminals. A vulnerability discovered in the past year is exploited to deploy various ransomware samples. Key threat actors using that breach are IceFire, Shadowserver and Buhti. The issue allows arbitrary code execution, and touches all app versions before Faspex 4.4.2 PL2. What… Continue reading Ransomware Actors Target IBM’s Aspera Faspex
3CX Phone System is Struck With Chain Supply Attack
3CX Phone System, a desktop app for business phone communication, fell victim to a supply chain attack. Recent updates deliver a forged version of the application that makes it possible to install stealer malware. The actual payload is getting delivered in a 3-stage manner, which makes it harder to track. What is the 3CX Phone… Continue reading 3CX Phone System is Struck With Chain Supply Attack
BreachForums is down. Things got worse?
Recently, one of BreachForums administrators nicknamed PomPomPurin was arrested by the FBI. That event took place on March 17, 2023, and since then, another administrator of that forum assured that BreachForums activity will not be interrupted or influenced. However, since 19:00 GMT of March 19, the page is not available. What is BreachForums and who… Continue reading BreachForums is down. Things got worse?
5 Tips to Improve Your Privacy on the Web
Nowadays, online privacy is a crucial concern that we should all be aware of, especially when it comes to using a web browser. It contains all the information about our daily online activities – and each of us has plenty of it. In this article, we’ll give you some practical advice on how to safeguard… Continue reading 5 Tips to Improve Your Privacy on the Web
New Microsoft SmartScreen Bypass Technique Causes Concerns
Microsoft SmartScreen proved to be an effective way of approving the legitimacy of the application – by checking one’s certificate. With time, Microsoft did a lot of work making it more efficient and sustainable to hacking – but that never made even a single mechanism secure from zero-day breaches. A new vulnerability that allows bypassing… Continue reading New Microsoft SmartScreen Bypass Technique Causes Concerns
Incoming Silicon Valley Bank Related Scams
Mind-bending globe-scale events always attract a lot of attention. Newsmakers, politicians and simple rubbernecks pay a lot of attention to such a loud events, and a recent Silicon Valley Bank meltdown is a perfect example. Scammers are no exception, as they should be peaky and roguish to success with their outlaw activities. But how can… Continue reading Incoming Silicon Valley Bank Related Scams