Symbiote Backdoor: a Stealthy and Highly Evasive Linux Malware
Researchers at Blackberry and Intezer have revealed a malignant program dubbed Symbiote used to inject rootkits and backdoors into compromised Linux servers. This software has been targeting financial institutions throughout South America. To install the pest into the system, the malefactors need root access, which they can obtain via either exploiting unmended vulnerabilities or account data leakages. After the initial hacking, the malware gains a foothold in the system to conduct further attacks, cover the presence of other malicious programs, and intercept confidential data.
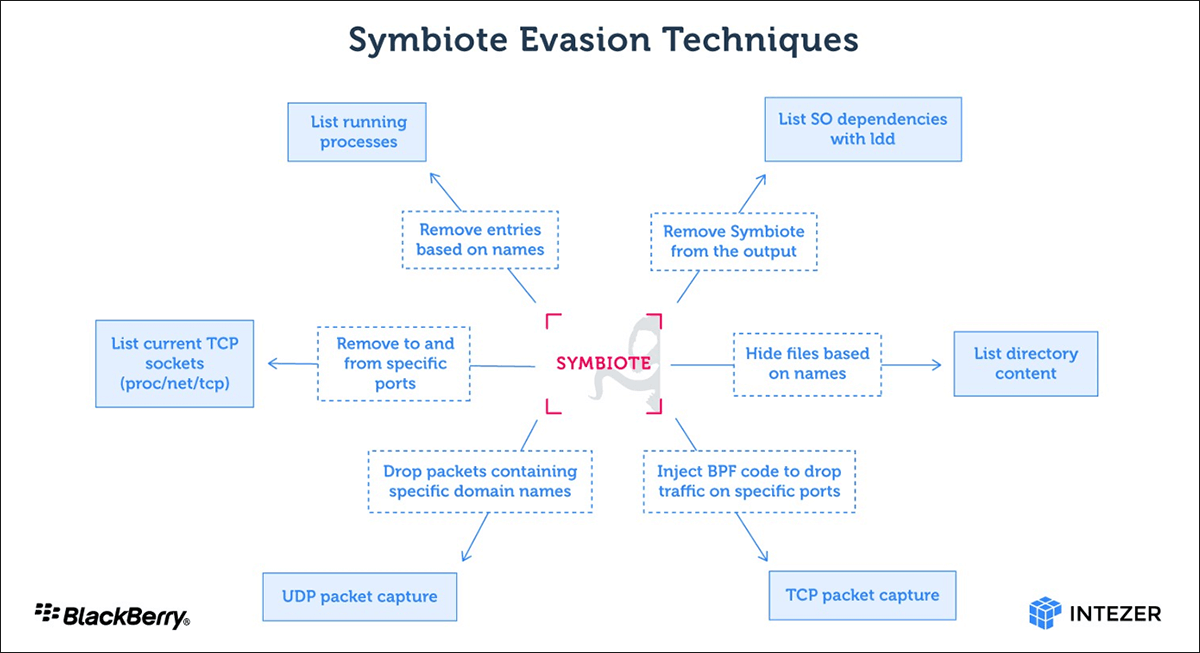
Symbiote’s specificity is that it spreads through a separating library, which loads during the launch of all processes via the ld_preload trick and substitutes some requests of the standard library. Processing of the replaced callings covers the backdoor-related activity. For example, it excludes particular elements from the processes list, blocks access to certain files in /proc, hides files in folders, excludes the malicious separating library from the lld output (the interception of the execve function and the analysis of the calls with the LD_TRACE_LOADED_OBJECT environment variable set to 1,) doesn’t show network sockets connected with the malicious activity. To defend against the traffic inspection, the functions of the libpcap library get reassigned, /proc/net/tcp reading gets filtered, and the substitution of additional bytecode into BPF-program loaded into the kernel. These techniques allow concealing the backdoor from the sniffers launched in the same system later on.
Symbiote can also manage to hide from the file system activity analyzers by stealing confidential data not on the file-opening level but via interception of these files read in legitimate applications (for instance, the replacement of library functions allows to intercept the input of the password by a user and the data with the access key uploaded from the file.) For remote access, Symbiote intercepts some Linux Pluggable Authentication Module calls. This allows connection to the system via a secure shell with certain attacking credentials. Privilege escalation is also provided for. Hackers can gain root privileges via modifying the environment variable HTTP_SETTHIS.




