Many of us have probably noticed various security-related markings around browsers’ address bars, but our understanding of what it all meant remained vague. These things are a closed padlock icon, green and yellow highlighting of the link, and, if something is wrong, we see an open padlock icon, crossed HTTPS at the beginning of the web address, and red highlighting. All the mentioned signs are related to SSL certificates. What they are and why modern websites need them are the topics of this post.
What is SSL certificate, How Does it Work
SSL stands for Secure Sockets Layer. It is a cryptographic protocol for secure connections. The 3.0 version of SSL is called Transport Layer Security, but everybody still uses the old name of the protocol. When we say SSL, we mean TLS. The protocol has been created to maintain secure data transfer. The combination of asymmetric and symmetric encryption methods makes an SSL-protected connection impossible to hack in a reasonable time. So, how does an SSL certificate work?
Why do we need SSL certificates?
SSL encryption is required to rule out the interception of data by hackers. Such an attack is called man-in-the-middle4. If malefactors succeed in it, they can steal sensitive data that we share with websites. However, thanks to SSL, if even hackers get the transferred data along the way, they will have to decode it, which will take them eons. However, that is not enough because hackers and scammers can spoof the known websites or lure users into their own pages, fooling them by presenting fake public keys (needed for SSL authentication procedure.) To tackle this, a digitally signed certificate issued to a website ensures the safety of the domain itself.
What is a Certificate Authority?
SSL certificate is the trust-based allowance to participate in modern-world secure communications. It is issued to trusted websites by trusted authorities called Certificate Authorities. The more expensive the certificate is, the more trust it presents and the longer the preliminary checks take. There are many CAs in the world, and they issue millions of certificates per year. The digital signature of the authority secures the SSL certificates it issues.
How do SSL certificates work?
The server fitted with a certificate has a datafile the browser requests as you try to access the website. The certificate contains the following information: the domain name it was created for, the person, organization, or device it was issued to, the name of the Certificate Authority, its digital signature, list of associated subdomains, issue and expiry date of the certificate, the public encryption key. There is some more to it, but the listed items are the most important.
“Handshake” procedure
The procedure of data exchange between the client (browser) and the server equipped with an SSL certificate is called a “handshake.” It takes less than a second to perform this operation, but its importance is hard to overestimate. It all happens in several steps beginning with a browser sending its request to the server. The server sends a copy of its certificate to the client; if the certificate is satisfactory, the browser sends a respective response establishing a secure encrypted connection thereafter. The point is that the authentication procedure uses asymmetric encryption in order to start symmetric encryption only valid for the current session.
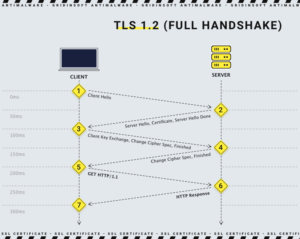
Not to leave your curiosity unsatisfied, we shall briefly mention some asymmetric cryptography features. In usual (symmetric) cryptography, both parties have the same secret key. If malefactors get this key, they can easily read any intercepted message. Asymmetric encryption works otherwise. It operates with a public key, used to encrypt messages, and a private key (never shared) used for message decoding5. To simplify, we can say that the browser and the server exchange padlocks that need no key to lock, but they don’t share keys. Even if hackers somehow get the encrypted message (padlock), it will take quadrillions of years for them to decipher it. On the last step of the handshake authentication, the server and client exchange a secret key generated solely for the current session. That allows them to switch to symmetric encryption, which is much faster.
Types of Certificates
The SSL certificates can provide different trust levels, and their price differs with respect to that (60$ per year on average, but hundreds of dollars for the most expensive options.) The main types of the certificates are the following:
Extended Validation (EV)
These certificates are the most expensive. They provide the highest level of trust, and they are a must-have for websites that collect users’ data and receive or direct online payments. EV certificate requires the longest and the most thorough verification procedure before it is issued. When the site has an EV SSL certificate, its address bar contains HTTPS, but also the name of the business and the country are shown. The padlock icon is there as well, of course.
Organization Validated (OV)
This certificate is the second most expensive one. Its features are mostly the same as EV’s, but OV focuses on providing the needed encryption without such an accent on prestige and presentability.
Domain Validated (DV)
DV is the cheapest certificate type. It is enough for the website owner to answer a telephone call or an email to complete the validation procedure. However, DV is only enough for websites that neither collect any information nor involve payments. The encryption provided here is the weakest. The address bar only receives a padlock and HTTPS marking.
Wildcard
This type of certificate is used when the website owner wants to secure one domain and an unlimited number of subdomains. For example, the domain can be website.com and its subdomains help.website.com, blog.website.com, or shop.website.com. One Wildcard certificate will cover all of them.
Multi-Domain Certificate (MDC)
This certificate allows its users to secure different domains and subdomains. It’s like a Wildcard one, but the list of protected websites is not limited to subdomains of one domain! The client can secure a list of virtually random sites and subdomains.
Unified Communications Certificate (UCC)
UCC is a very trusted certificate, giving a green highlighting of the address bar for its owners’ websites. It has a multi-domain feature and strong encryption. UCC is very respected, sharing one level of trust with the EV certificates.
Certificate Expiration
SSL certificates are designed to expire. That is so because the certificate is not the encryption service it provides alone, but the correspondence of lots of data about the company with facts about it. This correspondence is what allows these authorities to issue and maintain the certificates. Since everything can change quickly in the business world, and websites may change owners, properties, and even what they do, SSL certificates require regular renewal. The validity period for a certificate is around two years, but the requirements get more severe every year. The voices are heard already to make certificates last not more than a year.
Related threats and how to avoid
Earlier, HTTPS was a trustworthy sign of any website’s security status. Phishing attacks used to be easily exposed based on the absence of the SSL certificate on scam-related websites.
For some time now, scammers have taken phishing to a new level. Now they manage to use certified sites 6 in their schemes. Therefore, to see HTTPS marking and calm down is yesterday’s approach. To avoid becoming a victim of phishing, you need to check any sites for spoofing.
- Follow Internet security rules. Never open suspicious email attachments. The same goes for links. If you receive a notification that you doubt the authenticity of, contact the service that the sender claims to be via another communication channel. Try calling them, for example.
- Use reason and intuition. If soon it will be impossible to trust certificates, be reasonable. Do not be fooled by advertising, where they promise you something very good, very cheap, and even fast. Be vigilant if allegedly you were sent a package, although you did not expect it. And, of course, it is unlikely that your second cousin is the Prince of Brunei in exile, who bequeathed all his fortune to you.
- Double-check for spoofed website links and email addresses. They might look very similar to the authentic ones differing by one letter, but the goal of the malefactors is to take you by stealth when you’re not on guard.
- To protect yourself from malware in case the phishing attack still happens, install a reliable antivirus program. GridinSoft Anti-Malware is one of the most effective and versatile solutions on the market. It warns about dangerous websites in case you are trying to access them and immediately clears malware, if a successful phishing attack involves infecting its victim’s machine.
- One of the well-known MitM examples is Kazakhstan's attempt to launch an SSL certificate that would allow government-level spying. Google, Mozilla, and Microsoft rejected the certificate.
- Such cryptographic wonder is possible by virtue of the features of one-way mathematical functions. Those are hard to reverse, which means costly in terms of computing. Also, the trapdoor functions are important. These are one-way functions allowing inversion if an additional "trapdoor" value is given. The private key plays the role of this "trapdoor" in asymmetric encryption.
- The statistics on the matter were alarming back in 2020 already.
- One of the well-known MitM examples is Kazakhstan’s attempt to launch an SSL certificate that would allow government-level spying. Google, Mozilla, and Microsoft rejected the certificate.
- Such cryptographic wonder is possible by virtue of the features of one-way mathematical functions. Those are hard to reverse, which means costly in terms of computing. Also, the trapdoor functions are important. These are one-way functions allowing inversion if an additional “trapdoor” value is given. The private key plays the role of this “trapdoor” in asymmetric encryption.
- The statistics on the matter were alarming back in 2020 already.




