The Security Blog From Gridinsoft
Fortinet Fixes RCE Flaws in FortiOS and FortiProxy
Fortinet, a well-known vendor of corporate-grade security solutions, issued an urgent patch that fixes critical vulnerabilities in two products. FortiOS…
Clop Attacks on MOVEit Transfer Affected British Airways, BBC and More
According to security researchers, the Clop ransomware group has been looking for a way to exploit a vulnerability in MOVEit…
Android Malware Mimics VPN, Netflix and Over 60k of Other Apps
Android is an open operating system. This is an advantage and a disadvantage. Cybersecurity technology experts recently discovered a widespread…
Beware of Vacation-Related Scams: 4 Most Prevalent Types
Email scam actors constantly try to pick a better disguise for their fraudulent messages. Summer, the time when people commonly…
BlackCat Ransomware New Update Boosts Exfiltration Speed
BlackCat ransomware continues to make a fuss globally for the second year now, targeting various sectors. Most of the time,…
WEF warned of impending cyber pandemic
The WEF experts warned about the impending cyber pandemic and…
Hackers infected the Android emulator NoxPlayer with malware
UPDATE: BigNox contacted us and said that they “contacted cybersecurity…
FonixCrypter ransomware stopped working and published a key to decrypt data
The authors of the FonixCrypter ransomware announced that they had…
LogoKit phishing kit allows creating phishing pages in real time
RiskIQ researchers said that the new LogoKit phishing kit was…
DreamBus botnet attacks corporate applications on Linux servers
Zscaler analysts reported about the new DreamBus botnet that attacks…
Authorities of South Africa create their own browser to continue to use Flash
ZDNet reports that the South Africa Revenue service has created…
End of support for Adobe Flash caused interruptions in the Chinese railway system
As you know, back in 2017, Apple, Facebook, Google, Microsoft,…
New worm for Android spreads rapidly via WhatsApp
ESET security researcher Lukas Stefanko reported a new malware: he…
Researcher Found Three Bugs Allowing Hacking Amazon Kindle
Researcher Yogev Bar-On from Israeli consulting firm Realmode Labs talked…
Chinese hack group Chimera steals data from air passengers
According to reports of cybersecurity researchers, the Chinese hack group…
Raindrop is another malware detected during the SolarWinds hack
Symantec specialists detected Raindrop malware, which was used during the…
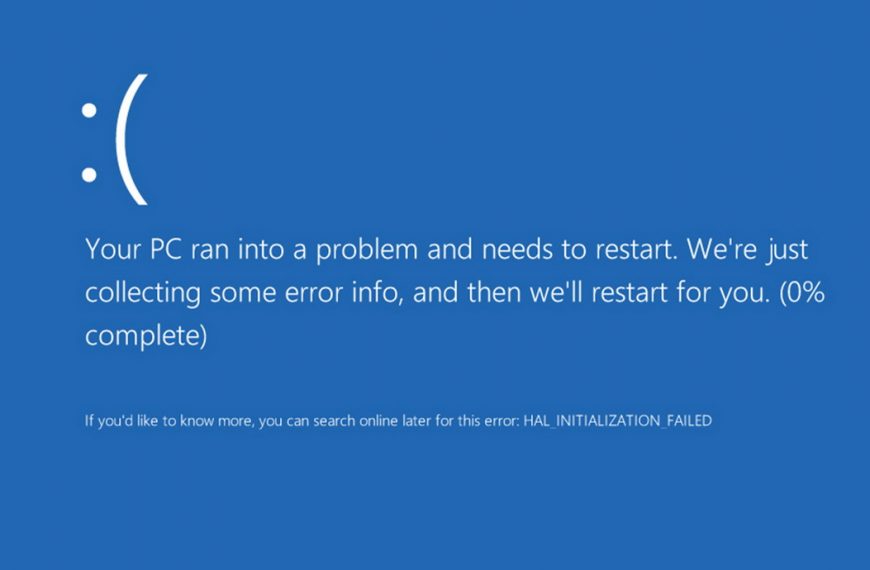
Windows 10 bug causes BSOD when opening a specific path
A bug in Windows 10 causes the OS to crash…