Last fall, researchers from Pen Test Partners reported on the insecurity of extremely unusual gadgets – Cellmate men’s chastity belts, manufactured by the Chinese company Qiui.
Then analysts wrote that devices have a lot of security problems, and hackers can also block and open them remotely, and there is simply no manual control for “emergency” opening or a physical key for Cellmate. That is, blocked users could find themselves in an extremely unpleasant situation.
Cellmate’s main problem was its API, which is used to communicate between a gadget and a respective mobile application. The API turned out to be open to anyone and is not password protected, and because of this, anyone can take control of any user’s device. This could not only allow hackers to remotely control the Cellmate, but it also helped to gain access to the victim’s information, including location data and passwords.
Unfortunately, the Cellmate developers were not able to immediately eliminate all the problems found by the researchers, but they released a video in which they demonstrated that it is still possible emergency opening of the chastity belt using a regular screwdriver.
Note that currently all vulnerabilities seem to be fixed and the latest version of the application can be considered safe.
However, the Bleeping Computer now reports, citing VXUnderground, that the application has clearly not been updated by all, and intimidating predictions of experts are coming true.
As it turned out, shortly after the disclosure of information about the Cellmate problems, hackers began to attack users of the Qiui Cellmate application and block their devices. To unblock the victims, they demanded 0.02 bitcoin (about $270 at the exchange rate at the time of the attacks, about $720 today).
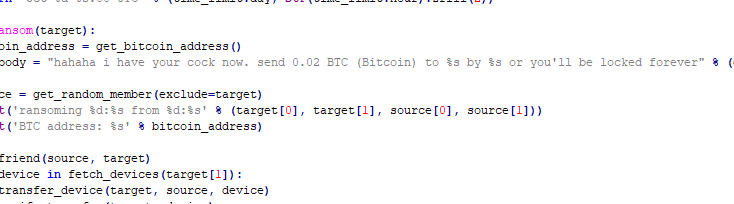
VXUnderground researchers have already published the source code of the ChastityLock ransomware, having received it from unnamed third parties, who in turn received it from hackers. According to the recent analysis, the malware contains code that communicates with the endpoints of the Qiui API to retrieve information about users, send messages to victim applications, and add friends.
Journalists write that the attackers not only demanded ransom from users of unsafe sex toys, but also mocked their victims. For example, after blocking, attackers wrote to the victims that they had used magic to take control of their gadget. However, according to the newspaper, in the end, no one paid the ransom to the hackers.