A newly discovered Java-based stealer named Rude has emerged, encapsulated within a Java Archive (JAR) file. It employs a range of sophisticated functionalities and focuses on stealing sensitive data from gaming platforms such as Steam, Discord, and other browsers.
Rude Stealer Overview
In early November 2023, researchers identified a malicious JAR file labeled “Stealer.jar” on VirusTotal. Further analysis revealed that this file is an information stealer named Rude. Unlike a more common form of executable files, this malware is Java-based and designed to target the Windows Operating System. JAR files can be stealthier and evade detection from conventional security software.
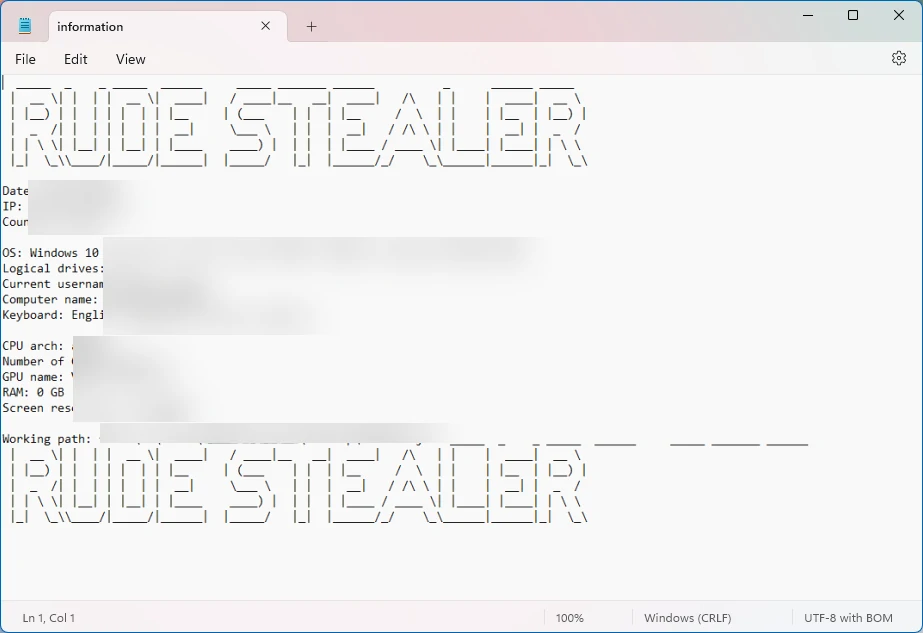
The primary target of Rude Stealer is tokens and IDs from popular applications like Discord and Steam. Additionally, it collects a plethora of sensitive information. Among them are passwords, cookies, browsing history, and auto-fill data from various browsers. Remarkably, this malware ignores cryptocurrency wallets, which have become a typical point of interest since 2020. The stealer is also equipped with the ability to capture screenshots, adding an extra layer to its information-gathering capabilities.
Initial Infection and Technical Analysis
While the initial infection vector remains unknown, it’s clear that Rude Stealer requires manual activation by TAs through command-line arguments. By specifying their Telegram channel chat ID and Bot Token, TAs initiate the stealer to commence its data theft activities. A detailed technical analysis reveals the workings of Rude Stealer, with specific class files dedicated to various operations.
Stealing Steam User Data
First of all, Rude Stealer meticulously scans the victim’s system for the Steam application directory, copies relevant files, and extracts SteamIDs. These IDs are then used to generate URLs leading to the Steam community profiles of the victims. Building on the acquired Steam user data, the stealer delves into the installed games, retrieving game names and logging this information in a designated text file.
Extracting Discord Tokens And Browser Data
Next, the stealer locates Discord-related directories, copies pertinent files, and extracts Discord tokens using regex patterns. It saves these tokens in a separate text file. Besides Discord, this stealer collects sensitive information from the following browsers: Brave, Edge, Chrome, Firefox, Opera, OperaGX, Vivaldi, and Yandex. The extracted information from different web browser databases is saved in log files. It includes:
- Autofill
- Credit card data
- Cookies
- History
- Passwords
Capturing System Information
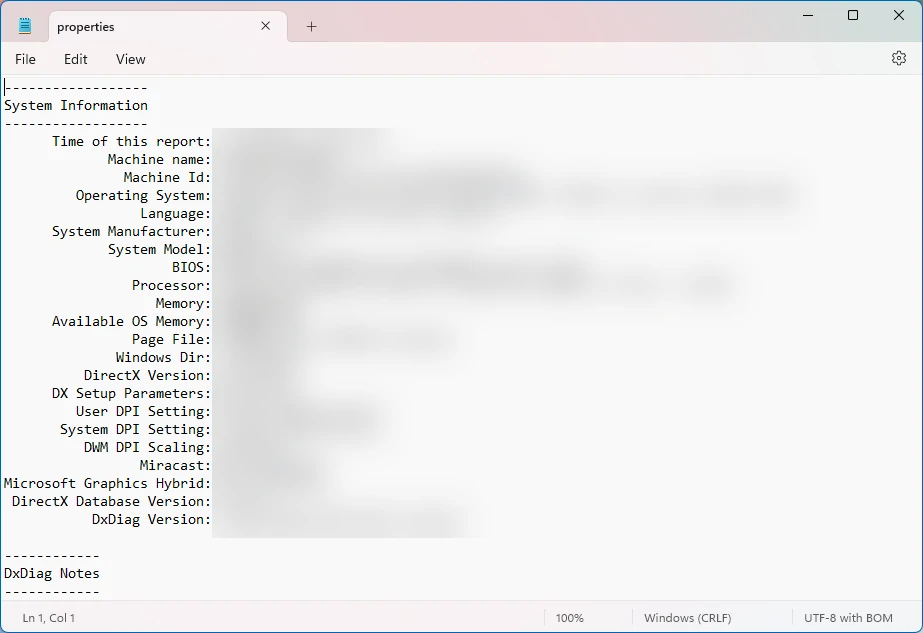
During the next step, the Rude Stealer gathers a list of active processes on the compromised system. The details it records include process names and IDs. Apart from gaming platforms, Rude Stealer also retrieves a wide range of system-related information. Nothing unusual here – it gathers IP address, country, CPU architecture, and RAM amount. All of this data is saved in a text file. Additionally, this stealer can capture screenshots using the Java Robot class, which are then saved in the user profile directory.
Data Transmission and Cleanup
Once all the necessary information is collected, Rude Stealer compiles it into a ZIP archive and assigns the archive’s label with the computer’s name. The archive is subsequently sent to the TAs’ Telegram channel through the Telegram bot API. The stealer finishes its operation by performing a so-called meltdown, removing files and directories linked to its presence.
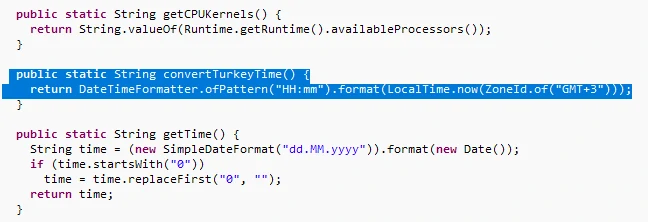
Based on the evidence found during the analysis, researchers inferred that Rude Stealer is probably being operated by a TA associated with or operating from Turkey. This assumption is supported by the fact that the stealer gathers the time of the compromised system and converts it to Turkey’s time zone.
Recommendations
Despite being a simple Java-based stealer, Rude Stealer is still a significant threat to individuals and organizations. Its use of Dxdiag to gain sensitive information is particularly troubling.
- Disable the automatic password-saving in the browser. This is an essential step because stealers often target web browser data. Instead, you can use a password manager to manage and store your passwords securely.
- Establish stringent access controls for system tools. Since Rude Stealer can abuse dxdiag to execute its malicious code, implement stricter access controls for these tools. You can do this by restricting which users can run these tools or using application allowlisting.
- Block the creation of text files in sensitive user profile folders. Rude Stealer often creates text files in sensitive user profile folders to store stolen data. To prevent this, enforce strict rules that block the creation of text files in these folders, particularly in paths like “C:\Users\[username]”. You can use file system permissions or security software to achieve this.
- Use an anti-malware solution. Maintaining up-to-date anti-malware and internet security software is crucial for protecting against malware. These tools can detect and block malicious code from executing on your devices.





