PUA:Win32/Caypnamer.A!ml is a detection used by Microsoft’s Defender that identifies files or processes exhibiting suspicious characteristics. It is typically associated with Potentially Unwanted Applications (PUAs). Although PUAs are not considered malware as they do not directly cause harm to the system, their presence may pose a potential security risk.
Frequently, this detection appears after the use of cracked software, keygen tools, trainers, cheat engines, and software programs that change the behavior of other applications. Using such tools is often illegal and can lead to serious legal consequences, aside from being dangerous from cybersecurity perspective.
PUA:Win32/Caypnamer.A!ml Overview
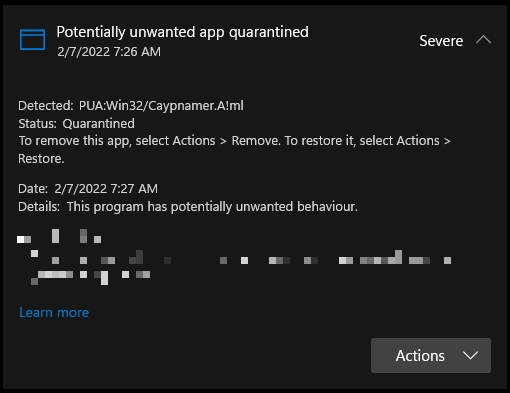
PUA:Win32/Caypnamer.A!ml is a detection name Microsoft Defender uses to identify a potentially unwanted application (PUA). The name “Caypnamer” does not have a specific definition, so I made my own assumptions about its meaning during the research.
Most of the time, this detection appears to cracked software, keygen tools, trainers, or cheat engines. These are often obtained from unreliable sources or through illicit means. Users unknowingly download and execute these programs, introducing malicious code into their systems. While it is illegal to use such tools, it also carries the risk of infecting your device with malware.
The main thing in common amongst all the mentioned software is the ability to interfere with the processes’ memory. Some of them inject the code into a running program to change the internal values (cheat engines, trainers), some do this to make the program skip certain procedures, most commonly license checks. In my opinion, this is the main thing that defines Caypnamer over other PUA names.
Is PUA:Win32/Caypnamer.A!ml a False Positive?
Sometimes, the detection of PUA:Win32/Caypnamer.A!ml can be a false positive. This is because it is a detection of Microsoft Defender, specifically, the AI detection system. The “!ml” particle at the end stands for machine learning. This detection is usually triggered when the app can interfere with a program’s files and memory.
Technical Analysis
Let’s examine PUA:Win32/Caypnamer.A!ml step by step to understand how it works. While being just risky rather than outright malicious, it makes quite a few actions that should not be here. I’ve made the analysis based on the sample of a trainer for one of the popular games.
Virtualization/Sandbox Evasion
After the launch, Caypnamer performs several checks that detect if it’s running within a virtual machine or sandbox environment. It accesses the following registry key:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager
This awareness aims to evade analysis attempts conducted within such controlled environments. It is not clear why the trainer will need to know about whether it is running on the VM/sandbox.
Discovery
Further actions of the Caypnamer is are barely safe either. It conducts reconnaissance on the infected system to gather information about its configuration and environment. Some of the Caypnamer samples are capable of antivirus detection evasion, and such data is what gives the thing a clue on how to do this.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\NetworkList
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList
It reads software policies to understand the security measures and identify potential vulnerabilities. Additionally, it may query system time settings and time zone information to tailor its behavior or evade detection based on time-based triggers.
How To Remove a Caypnamer.A!ml?
If you are unsure of the validity of the detection, you can use a third-party anti-malware tool. I recommend GridinSoft Anti-Malware. This program will help you determine if there are any dangerous programs on your system.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.