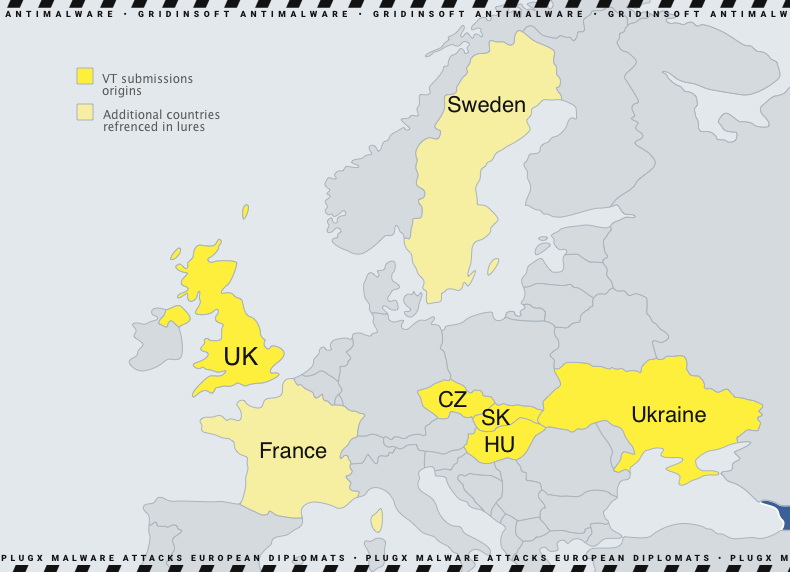
Over the past few months, researchers have been monitoring the activity of a Chinese threat actor using PlugX malware to target foreign and domestic policy entities and embassies in Europe. This is a more significant trend among Chinese-based groups increasingly focusing on European entities, particularly their foreign policy. The countries most targeted in this campaign are Central and Eastern European countries such as Slovakia, the Czech Republic, and Hungary. Key target of these attacks is likely obtaining sensitive information about their foreign policies. The UK is the only country that is away from Europe’s center or east, targeted so far.
HTML smuggling as a method to bypass network detection.
The PlugX activity targets foreign policy entities in Europe, mainly Eastern Europe, by using HTML Smuggling. HTML Smuggling is a method used by hackers to conceal harmful payloads within HTML documents. The SmugX email campaign uses HTML Smuggling to download a JavaScript or a ZIP file. This creates a long infection chain that ultimately results in the victim being infected with PlugX.
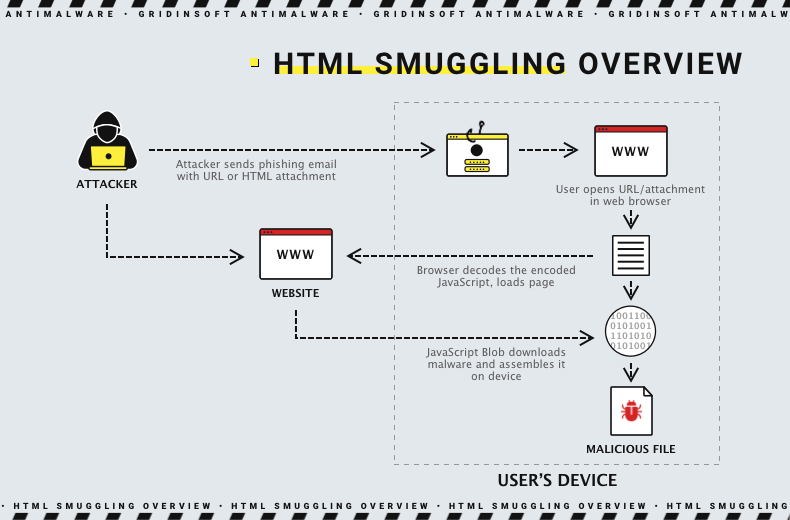
Adversaries have used HTML smuggling for a while. Still, it has become more common since Microsoft blocked other popular methods of sneaking malware onto systems, like default-blocking macros in Word documents.
Lure for European politicians
The Attackers primarily focused on European domestic and foreign policy and were mainly used by Eastern and Central European governmental organizations.
Most of the documents found had content related to diplomacy, with some specifically concerning China and human rights. Furthermore, the names of the files imply that the targets were likely government officials and diplomats.

Attack on the European government
The attackers implemented HTML smuggling to enable downloading a JavaScript or ZIP file onto a compromised system. In the case of a ZIP archive, it includes a harmful LNK file that triggers PowerShell. On the other hand, if a JavaScript file is utilized, it will download and activate an MSI file from the attackers’ server.
After infecting a system, the DLL decrypts the PlugX malware. This malware can conduct several harmful activities, such as capturing screenshots, logging keystrokes, executing commands, and extracting files. A legitimate executable is hijacked and downloaded during the infection process to ensure that the malware remains on the system. The malware then duplicates the fair program and DLL, storing them in a hidden directory. The malware adds the legitimate program to the Run registry key to maintain persistence.
Is it possible to evade PlugX infection?
Potential targets of such attacks must prioritize defense. In a significant cyber attack, resetting the organization’s cyber security approach and posture is recommended. Every organization must reflect on its actions and decisions following a considerable spell. Though, it should be a lesson not only for governmental services but also for companies.
- Regularly update the systems. It is essential to regularly update your operating systems, software, and applications with the latest security patches and updates to fix known vulnerabilities.
- To enhance your security measures, it is necessary to revamp the cybersecurity training provided to government officials.
- A unique role for such organizations is the Zero Trust principles, so you can completely change the state of affairs in security.
- Implementing strict access controls such as strong passwords, multi-factor authentication (MFA), and role-based access control is essential to prevent unauthorized access to sensitive data and systems.
To minimize the risk of attacks, companies should implement various security measures. These include adopting robust security strategies, such as the Zero Trust model, regularly updating and patching systems, providing thorough security awareness training, implementing strict access controls, segmenting networks, using advanced threat detection tools, regularly backing up data, conducting security assessments, and utilizing third-party security services. By taking these steps, companies can significantly reduce their vulnerability to attacks.




