CrowdStrike warns that hackers are adding malicious functionality to self-extracting SFX archives containing harmless honeypot files that can launch PowerShell.
This simple trick allows attackers to plant backdoors on victims’ machines without raising an “alarm”.
Let me remind you that we also wrote that Attackers target .NET Developers with Malicious NuGet Packages, and also that Hackers compromised Slack private GitHub repositories.
Also information security specialists warned that Hackers bypass ransomware protection using WinRAR.
The researchers remind that self-extracting archives created with archivers such as WinRAR and 7-Zip are, in fact, executable files that contain archive data along with built-in unpacking functionality.
Access to such files may be password protected to prevent unauthorized access. SFX files were originally created to make it easier to distribute data to users who don’t have a decompressor.
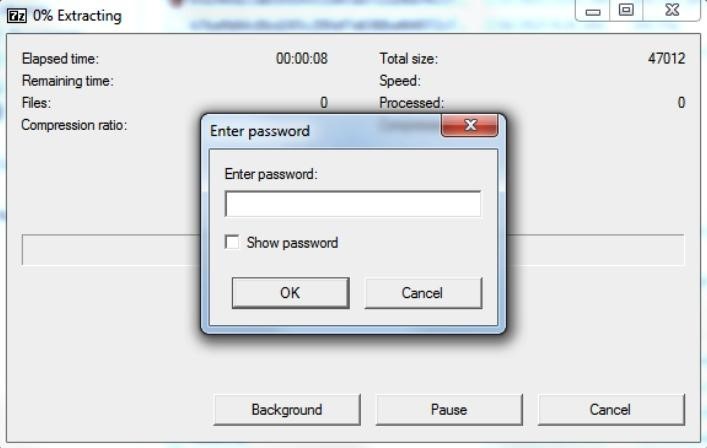
Password protected SFX file
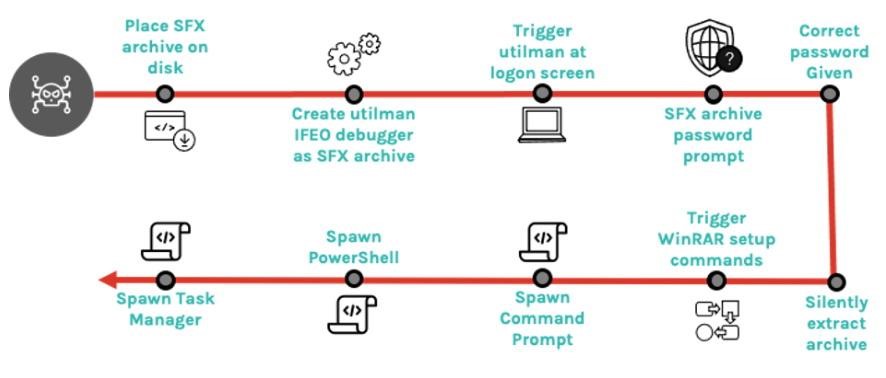
Recently, Crowdstrike experts discovered an attacker who used stolen credentials to abuse utilman.exe (an accessibility application that can be run before a user logs in) and configured it to run a password-protected SFX file that was previously placed on the system.
The SFX file launched by utilman.exe was password protected and contained an empty text file that acted as a decoy. The real purpose of the archive was to run PowerShell, the Windows command line (cmd.exe) and the “Task Manager” with system privileges.
Further analysis of the threat showed that the attacker added several commands at once, which were run after the target unpacked the archived text file.
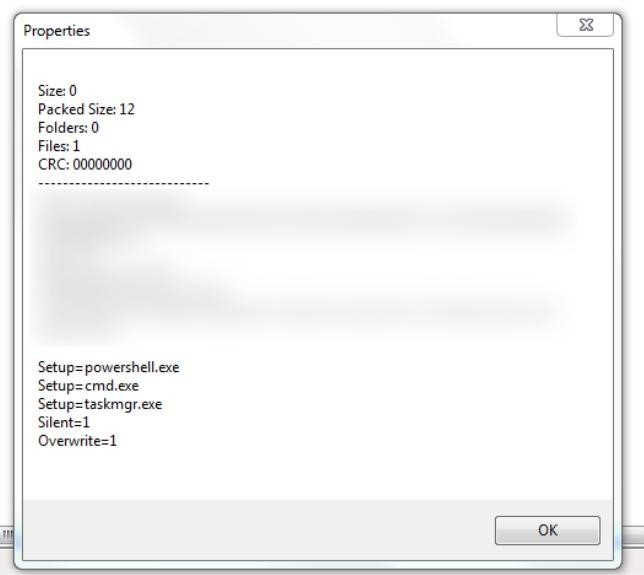
As you can see in the screenshot above, the attacker configured the SFX archive in such a way that no dialog boxes were displayed during the extraction process. He also added instructions for launching PowerShell, Command Prompt, and Task Manager.
The fact is that WinRAR offers a set of advanced settings for SFX, which allow adding a list of executable files to be automatically launched before or after the unpacking process, as well as overwrite existing files in the destination folder if files with the same name already exist.
The researchers remind that users should pay special attention to self-extracting archives and use the appropriate software to check their contents and look for potential scripts and commands scheduled to run on extraction.




