People often confuse personal data and sensitive data. But what exactly is the difference between them? What makes data sensitive, and what personal? Why are corporations so eager to collect even the smallest pieces of user data? Let me explain the differences between personal and sensitive data, risks related to their exposure and best practices for keeping it safe.
Personal Data, Sensitive Data – What’s the Difference?
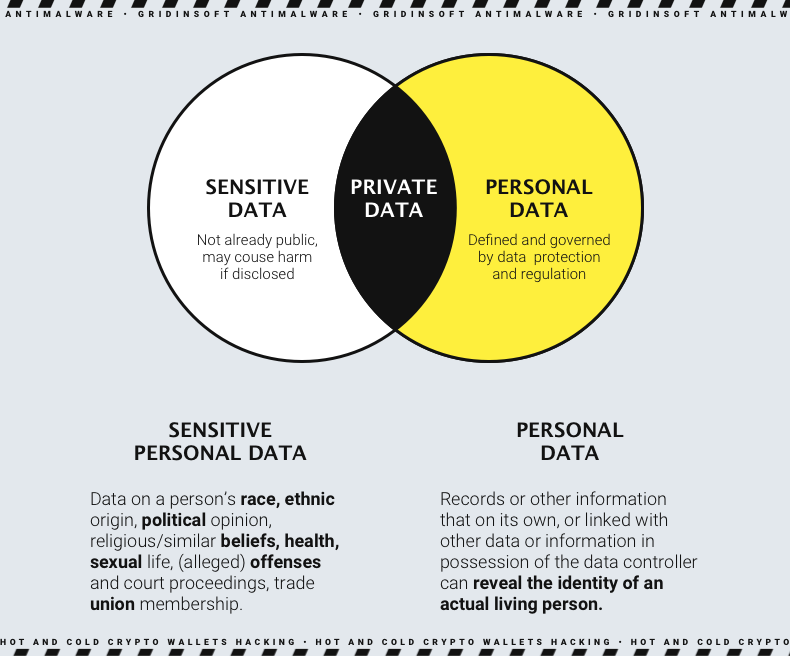
Sometimes people confuse the meaning of the terms personal data and sensitive data, or mistakenly think they are the same thing. As you could have already guessed – they are not. While both refer to types of information related to individuals, they differ in the level of sensitivity, potential risks, and legal protections they require. Sensitive data has more stringent requirements that must be met by the organization that processes it. In turn, the conditions for processing personal data are different.
Collecting this data is a common action for most applications and websites. And that is normal – payments, subscriptions and registrations are barely possible without any user data identifying the process. At the same time, it is a foul tone for a website to collect any sensitive data – even in the form of locally stored cookies.
But what is sensitive data? The most weighted definition says it is a type of personal information, the disclosure of which can leave the one vulnerable to different identity-based attacks. While laws generally protect personal information, sensitive information (also called confidential) receives special attention. This is primarily because it can affect a person’s livelihood, quality of life and ability to go about daily activities. To be more specific in definitions and conclusions, let’s have a more detailed look on every data type, with corresponding examples.
What is Personal Data?
Personal, is essentially any information that we can use to directly or indirectly identify a person. Among the most typical examples of such data are details like a name, phone number, address, age, or email. This category of data can extend to more unique identifiers, such as CCTV footage, biometric data like fingerprints, or even eye scans. So, any piece of information, when combined with other relevant details, that leads to the identification of a person is considered personal data.
Personal data examples:
- full names
- birthdays
- telephone numbers
- home addresses
- email addresses
- bank details
However, not all data can be personal. For example, a name by itself is not initially personal data. It only becomes one when combined with other information, like name and telephone number. Only then can it accurately identify a person. Organizations typically collect and store several pieces of information about data subjects. This information can be considered personal data if they are collected together to identify the data subject. Common examples of personal data include first and last names, home addresses, e-mail addresses, identification numbers, location data, Internet Protocol (IP) addresses, etc.
What is Sensitive Personal Data?
As for sensitive data, it refers to a particular category of personal data, i.e. it is a more narrow selection of information. Since it contains some specific facts about the person, sensitive information demands enhanced security measures and specific processing protocols. Under the GDPR, sensitive personal data encompasses quite a lot of categories, and they make sense pretty much around the world.
Sensitive data examples
- Political opinions
- Religious or philosophical beliefs
- Racial or ethnic origin
- Genetic data, including information about an individual’s inherited or acquired traitss
- Trade union membership
- Sexual orientation or sex life
- Biometric data such as fingerprints
- Data about a person’s physical or mental health
The General Data Protection Regulation outlines guidelines for collecting and processing sensitive personal data of EU citizens. There are separate rules for controllers and processors handling special categories of data. Processing and storing such data poses risks to human rights. Therefore, additional security measures are necessary to protect sensitive personal data.
Obtaining consent and rules for storing sensitive personal data
One common misunderstanding about GDPR is that businesses always need to obtain consent to process personal data. In reality, this isn’t true: consent is only one of six lawful bases for processing personal data. Explicit consent is specifically required for processing sensitive data.
Organizations that have not thoroughly researched compliance requirements risk a number of problems: lawsuits, fines, and loss of customers. In the context of data storage, the UK’s Data Protection Act (DPA) provides clear instructions. Physical copies of sensitive information should be kept securely, like in a locked drawer or cabinet. Digital files containing sensitive personal data should be encrypted and stored with restricted access.
What if Personal or Sensitive Data is Leaked?
Sometimes organizations and companies can put sensitive data at risk. This typically occurs when the database storing sensitive information is inadequately protected, whether due to weak encryption, software vulnerabilities, or human error. Sensitive data at risk may include medical records, banking information, home or work addresses, or contact details. Data disclosure is different from data leakage, where information is accessed without consent or authorization. In a data breach, personal information such as name, contact information, bank account and statement numbers, and ATM pin numbers are used by hackers to misuse the data and obtain money.
Unfortunately, for the end user, it is nearly impossible to fully prevent data leaks. As leaks happen on the corporate side and every Internet user leaves a digital footprint, leaks are hard to avoid proactively. Still, users can take steps to minimize the consequences. You should be vigilant about your online interactions and information sharing. Familiarize yourself with the privacy policy of any service to which you are providing data or planning to. Reputable services will explain what data they collect and why.
Secondly, if you suspect your data has been leaked, you can use services like Have I Been Pwned to check it. If it turns out your data has been compromised, change the passwords for any affected accounts to reduce potential risks.




