Hackers appear targeting logistics and transportation companies in North America with Lumma Stealer. A phishing campaign utilized various info-stealers and remote access trojans for espionage. Experts suspect several cybercrime groups backed by the governments of Russia and China are behind the campaign.
Transportation Companies Hit by Cyberattacks
Proofpoint researchers reported a new cyberattack targeting shipping logistics companies in North America. The campaign began in May 2024 and involved using remote access trojans to steal information. In addition to malware, attackers are using combined with phishing and social engineering to gain initial access.
Notably, the attackers disguise the malware as Samsara, AMB Logistic and Astra TMS management software. These software suites are made specifically to manage transportation operations. Phishing emails that the hackers were sending aimed at employees of logistics companies.
In other words, the attackers researched the target quite well before acting, so it is not an occasional attack. The malware used in attacks, as well as targeting also suggests the lean towards government-backed attacks, specifically from Russia and China. And, well, there is barely a reason for ordinary cybercriminals to get their hands on shipping data, contrary to cyber warfare actors. By the way, Lumma Stealer actively targets individuals in a similar scheme right now.
Technical Details
Experts do not specify the initial attack vector, the only thing noted is that at least 15 legitimate email accounts belonging to transportation and shipping companies were compromised. This allowed the attackers to send malicious emails with malicious payloads from what looked like legitimate senders. Most of the activity took place between May and July 2024, when attackers used Lumma Stealer, StealC or NetSupport as payloads. However, experts say that since August 2024, attackers have changed tactics. Instead of the previously used info-stealers, they used new infrastructure and delivery techniques, and added DanaBot and Arechclient2 delivery payloads.
To initiate the payload download, the attackers attached .URL files as an attachment to an email. Alternatively, the email could contain a link leading to Google Drive, which in turn hosts the aforementioned .URL file. Upon opening this file, the victim’s system connects to a remote Server Message Block server that contains the payload executable.
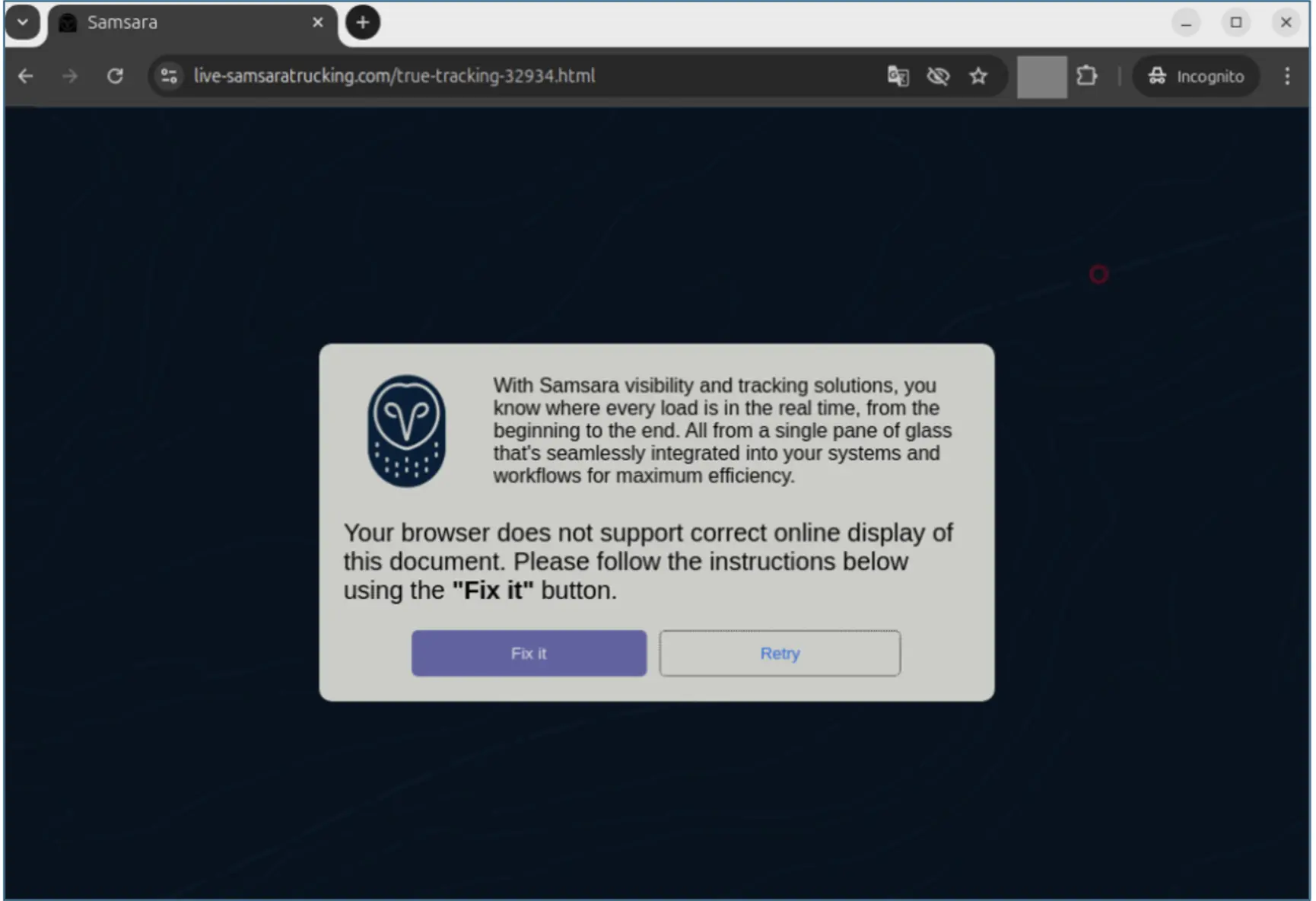
As mentioned above, around August 2024, attackers started employing a new infection method, known as ClickFix. This method involves sending a phishing email with a link to the user. Upon clicking the link, the user sees a web page with instructions on how to “fix” the error. The key issue is that the phishing page is disguised as Samsara, AMB Logistic, or Astra TMS, specialized logistics software. Combined with a legitimate sender, this dispels any doubt about the legitimacy of the email. As a result, the victim clicks on the link and follows the instructions. Due to this manipulation, the victim received DanaBot as a payload.
Potential Threat Actors
Although experts have not provided any clear indications as to who might be behind these attacks, given the motives behind these attacks, one can infer some conclusions. The first is the objective of the attacks, which appears to be purely espionage (there have been previous cases of ransomware deployment, but these efforts later shifted to spyware). The second is the recent events related to the detection of backdoors in modems installed in U.S. port equipment from Chinese manufacturer ZPMC. Considering these two factors together, it seems likely that China could potentially be behind these attacks.
On the other hand, the use of Lumma Stealer allows us to make an unmistakable assumption about the second potential threat actor – Russia. Moreover, given the current geopolitical situation in the world, Russia has all the prerequisites to unite with China for a common goal.




