A worldwide-known scandal around Sean Combs, known as P.Diddy, gave boost to malware spreading. Known as P. Diddy malware, it spreads under the guise of deleted social media posts of the rap star, that were allegedly collected by its fan. In fact, a short sequence of actions leads nosy persons to a remote-access trojan running in their systems.
Media Scandal Fuels P. Diddy Malware Spreading
An unknown group of cybercriminals piggybacks on the massive fuss around P. Diddy to trick people into installing malware. Under the guise of logs or screenshots of posts from his deleted account on X/Twitter, con actors offer people to follow the link that distributes malware. This virus already got a moniker “PDiddySploit”, and is in fact a version of open-source PySilon RAT, a remote-access trojan.
When the media storm regarding questionable business around the US rapper Sean Combs arised, the star deleted his account, wiping the publications. As people interested in the situation expect, they could have contained compromising or revealing information about him or the participants of the case. And cybercriminals decided to piggyback this interest of masses, packing the said malware into the file with “records of P. Diddy X/Twitter account”.
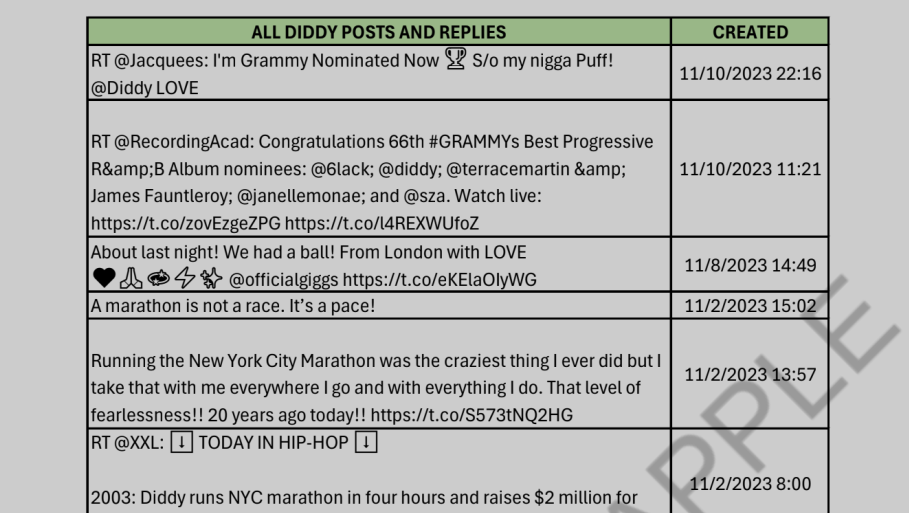
Files or links to ones with such content spread massively on different social media platforms; frauds offer it as a backlog of a bot that recorded every single publication of the account. While this is clearly possible, and I’m even sure there can be actual log dumps with that data, the files contain nothing but malware. As the original Veriti report on the attacks noted, high media attention, when combined with curious users, result in perfect conditions for malware attacks.
What is PDiddySploit, a P. Diddy Malware?
The malware in question, as I’ve mentioned above, is a variation of PySilon RAT, an open-source Python-based remote access utility. Anyone can get it from the GitHub repository, so it is common to see it as an improvised tool for establishing backdoor connections in spontaneous cyberattacks. What’s less spontaneous and improvised is the functionality of that virus: it is not to be treated as an amateur toy.
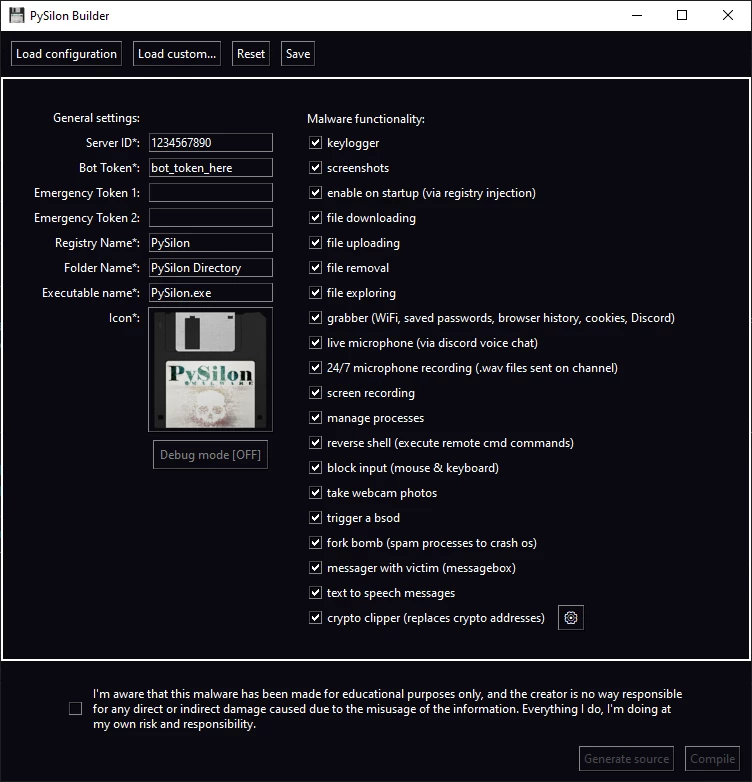
Main functionality of P. Diddy malware expectedly revolves around providing remote access to the system, together with the ability to execute commands. Aside from this, there are some spyware-like treats: it can log keystrokes, steal certain types of data from the host system and even record the screen. Sure enough, it may lack detection evasion measures and all the fancy tricks that “professional” crimeware has, but as the saying goes, you won’t like being on the receiving end.
Information stolen from the system in this way is typically of a great value on Darknet marketplaces, especially in large bundles. Further, users attacked with P. Diddy malware can experience losing access to their online accounts, see their crypto wallets and banking accounts drained, and tons of spam received to email inboxes. And the worst part is that it is already too late to react when the symptoms are live.
How to avoid such malware?
The best way to stay safe in this specific case is to hold your curiosity, and seek for more trustworthy sources of information than some random person on social media. Never haste opening the freshly downloaded files; it will be great to check it with online malware scanners. I’d recommend you a particular one – GridinSoft Online Virus Scanner, a free malware scanning service. It features a user-friendly interface, coupled with more diverse scanning approaches than what other similar services offer.
But the ultimate protection against threats like P. Diddy malware will be reliable anti-malware software. Ideally, one should feature sturdy online protection, to prevent possible malicious connections, and a multi-component scanning system that would be able to stop even the trickiest malware samples. GridinSoft Anti-Malware is a program that delivers all these qualities in one package – give it a try.