Two new vulnerabilities in F5 BIG-IP reportedly allow for remote code execution and SQL injection. The company explains it as a bad input validation. The worst part though is that both vulnerabilities were probably exploited in real-world attacks.
F5 BIG-IP Vulnerabilities Allows SQL Injection and Remote Code Execution
On October 26, 2023, F5 published two documents regarding the new vulnerabilities present in their flagship product. Both of them soon received CVSSv3 scores of 9.8 and 8.8 for RCE and SQL injection breach correspondingly. These ratings already explain how bad things are, but let’s dig a bit deeper.
SQL injection vulnerability, denoted as CVE-2023-46748, is considered less dangerous, and for a good reason. For its successful exploitation, authentication is required – in other words, attackers should possess a valid user account for your BIG-IP instance. This may not be a much problem for the circumstances where this injection may be used – for example, after gaining initial access.
Meanwhile, RCE vulnerability is always a mess, as it is useful at the very first stages of attack. That’s actually the reason why it is just shy of the top 10/10 score. F5 assures that this is only about command access, and the vulnerability does not allow for any data access. Still, this is already enough for hackers, as with access to the commands they can, say, create a new admin account for themselves.
Fixes for BIG-IP Vulnerabilities Available
Fortunately for the vast amount of F5 clients, fixes for both these vulnerabilities are available. The breach touches a wide range of BIG-IP versions, starting from 13.X and all the way up to 17.X. Another piece of good news here is that both breaches are fixed with a single patch. See the table below for all the details.
| Software | Vulnerable versions | Fixed in |
|---|---|---|
| 17.1.0 – 17.1.1 | 17.1.0.3 + Hotfix-BIGIP-17.1.0.3.0.75.4-ENG, 17.1.1 + Hotfix-BIGIP-17.1.1.0.2.6-ENG | |
| 16.1.0 – 16.1.4 | 16.1.4.1 + Hotfix-BIGIP-16.1.4.1.0.50.5-ENG | |
| BIG-IP (all modules) | 15.1.0 – 15.1.10 | 15.1.10.2 + Hotfix-BIGIP-15.1.10.2.0.44.2-ENG |
| 14.1.0 – 14.1.5 | 14.1.5.6 + Hotfix-BIGIP-14.1.5.6.0.10.6-ENG | |
| 13.1.0 – 13.1.5 | 13.1.5.1 + Hotfix-BIGIP-13.1.5.1.0.20.2-ENG |
The company also offers a temporary mitigation for these vulnerabilities, though, as it usually happens, they’re not ideal. In the case of SQL injection vulnerability, the only real way to block the exploitation without the update is to restrict access to the system for low-trust users. For CVE-2023-46747 though, F5 prepared a special script that reduces the attack surface by narrowing the list of allowed devices. Thing is, it works only for versions 14.1.0 and above.
Are They Exploited?
As CISA claims, both vulnerabilities are exploited. F5 themselves do not confirm these facts, meaning that there could be cases when vulnerable instances of BIG-IP were present on infected machines. Nonetheless, it is currently not clear whether they were the culprit, or hackers used another way to get in.
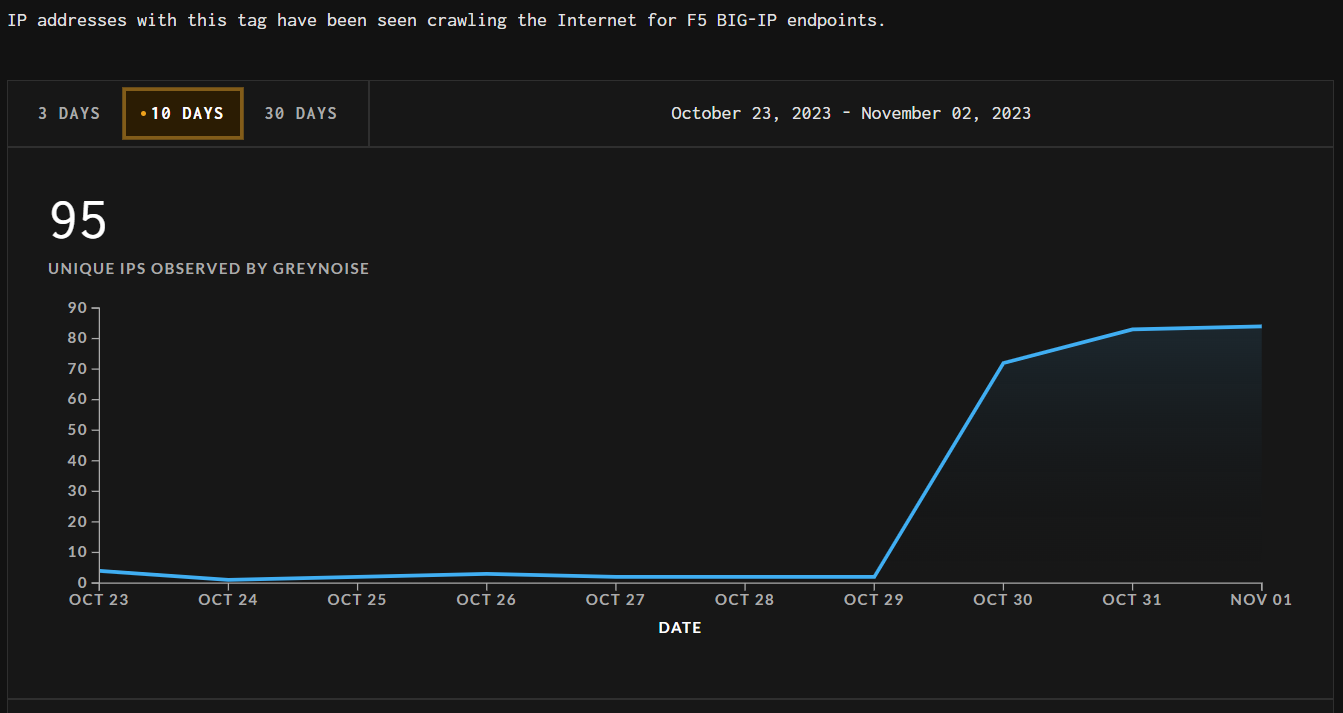
What is clear though is a noticeable hike in the number of IPs scanning the Internet for BIG-IP instances. The stats from Greynoise service you can see on the shot above show that from 2 IPs per day, the number skyrocketed to 80-85 since October 29. That was just 3 days off the date when F5 did initially publish their notification. This obviously means an increase in the interest of hackers that are willing to use new vulnerabilities.
How to stay safe?
As it happens in any case of a critical vulnerability that resides in a massively popular software, the best option is to patch it as soon as possible. There is no room for hope that hackers will ignore such a tiny software – just not in this case. And since there is no solution for the CVE-2023-46748 other than patching it, having only the RCE breach fixed is not really secure. Update is the best option here – though, as it usually happens, it may be troublesome to patch all the machines at the same time.
This is where active protection systems come in handy. XDR solutions, combined with proper UEBA and SOAR can effectively detect and stop questionable activities before they will lead to something bad. Sure, all these solutions can work on their own, though the combination is what makes them really powerful.
Instructing your personnel on the most widespread attack approaches is another proactive step. When there is no one to let the hackers in, the chance of a successful cyberattack becomes significantly lower. What’s even better is that hackers are not creating any new approaches throughout the last decade. Social engineering, email spam, infected MS Office documents or similar files – all these are used in different combinations. Showing how to detect a fishy email or a questionable file is much, much easier than solving the consequences of a cyberattack.