The Malware world evolves constantly, and it would be reckless to ignore newcomers and their potential. Meduza Stealer appears to be a pretty potent stealer variant with its unique features and marketing model. Additionally, this malware may be considered a firstling of a new malware generation – one which breaks old geolocation filtering rules.
What is Meduza Stealer?
Meduza is an all-encompassing infostealer, which is somewhat similar to the old guard at a glance. However, well-known things such as Redline or Raccoon stealers gained the ability to steal cryptocurrency information only with further updates. Meduza, on the other hand, can do this out-of-box, with the ability to circumvent more tricky protection measures of crypto apps. Moreover, it includes a much bigger list of wallets and browsers it can extract data from than any of the mentioned stealers.
The distinctive feature of Meduza Stealer is the way it hides its samples. Instead of a usual packing, hackers use code obfuscation and recompiling, which allows them to circumvent even the most robust anti-malware engines. Well, these approaches do not sound like something phenomenal, but when applied together, and in an unusual way, things may become way less predictable – and detectable.
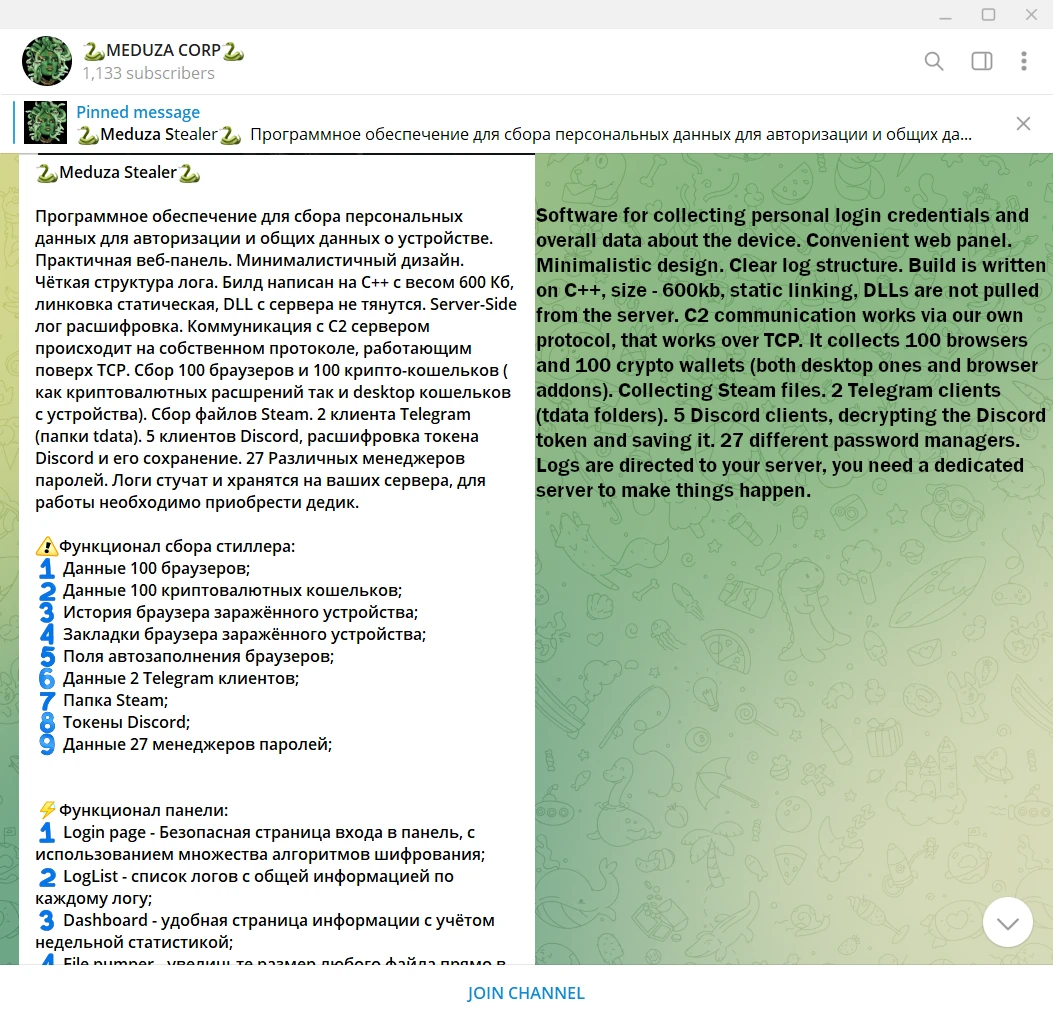
Though, this is not the full list of unusual things for this malware. In price, the malware offers 2 fixed plans and a negotiable lifetime license. For $199 you receive malware, all possible customization options for the payload, admin panel, and the ability to download all the logs in one click, for the term of 1 month. Hackers offer the same stuff for $399 for 3 months. And the cherry topping, as I said, is the ability to negotiate the prices of a lifetime license for this malware. Probably, malware developers are even ready to share the source code – but that is only a guess since there were groups that used such a model earlier.
An Offspring of Aurora Stealer?
There are plenty of examples of how brand-new malware may be a re-branded old sample, with a slightly different team of crooks behind it. Malware is rarely developed by a single person. Developers of one malware may start working on another, and bring their prior developments in a new product. Alternatively, a part of a cybercrime gang that stopped functioning may decide to resume their illegal deeds – and they rebrand their “tools” to start with a new image. This or another way, is a common occasion there.
In the case of Meduza Stealer, things are not that straightforward. Due to the use of enhanced obfuscation, it is hard to say whether it shares any code details with known malware families. Some malware analysts claim that Meduza is an offspring of Aurora Stealer – malware that popped out in late 2022. Their main arguments are similarity in the form of C2 calls and logs with collected data.
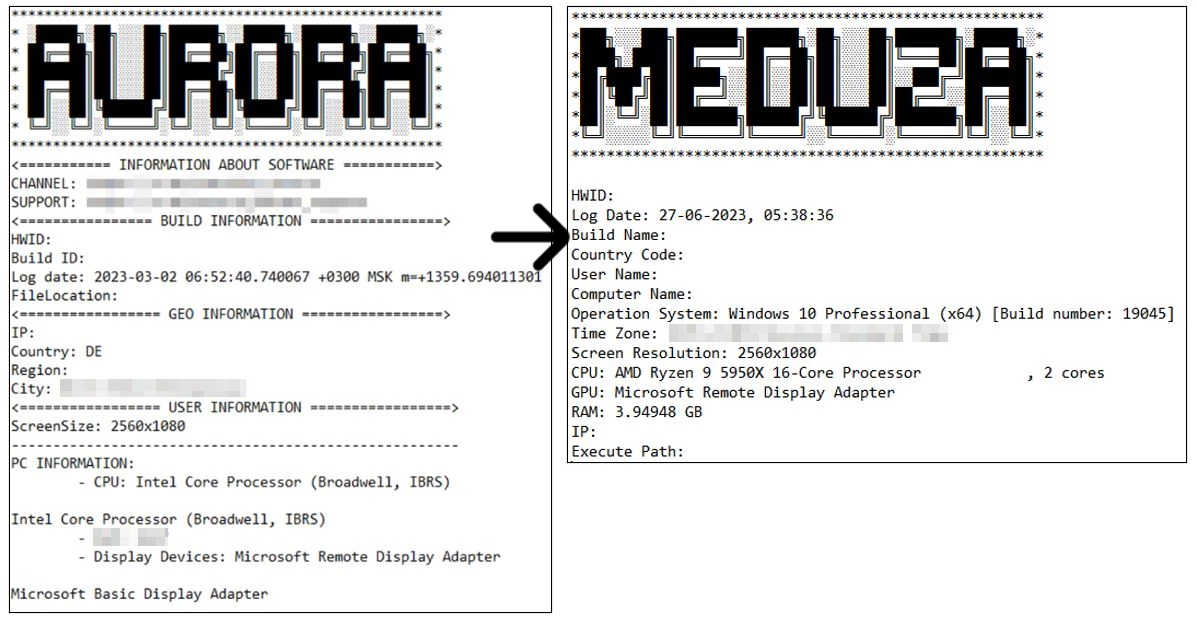
As you can see, Meduza’s logs resemble Aurora’s by the ASCII-styled header and some visual elements. However, it is not a definitive thing – malware developers sometimes inspire with or completely copy things from other malware families. Other details that researchers put under the suspect are file naming policies – but this is not the brightest proof as well.
This, however, caused a harsh reaction from malware developers. In their “support” channel they called all the proofs rubbish, and also said they picked up the trail of one who leaked the malware build. Also, there was decent evidence that proves Meduza’s originality – it is written in C++, which is not even close to the Golang used in Aurora Stealer.

Meduza Stealer Analysis: Catch Me or I Catch You
The threat that comes from each specific malware sample roughly depends on two factors: how hard it is to detect it and how much damage it can deal. Meduza Stealer tries to outpace its counterparts in these two factors. It is not the most stealthy malware, for sure, and there are ones that steal even more data, but rare samples may boast of a combination of these two. And Meduza does.
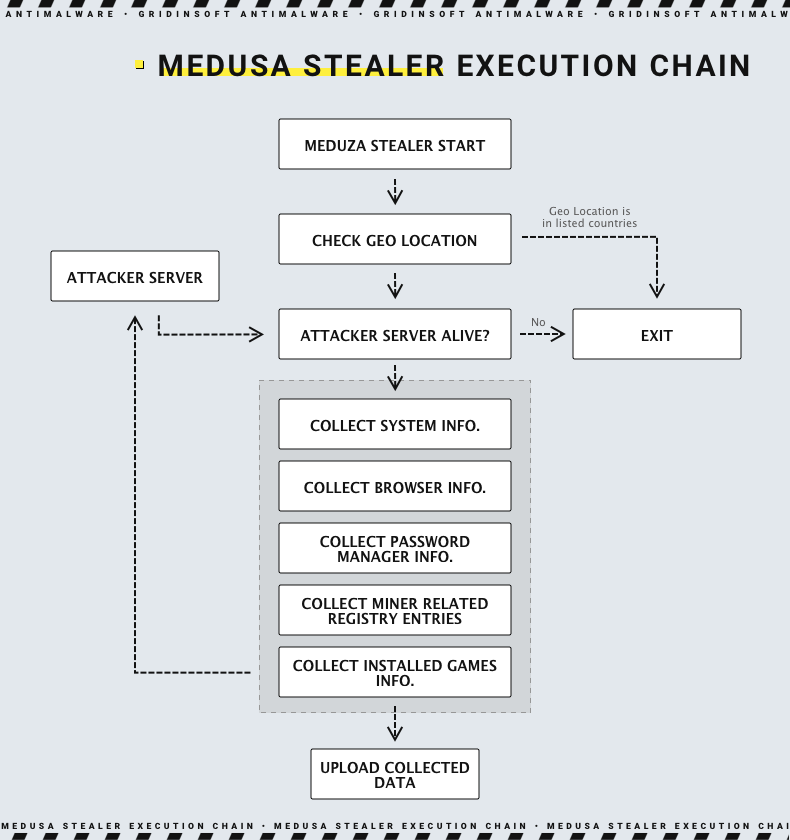
In the picture above you can see the simplified scheme of the Meduza Stealer operation process. First of all, it checks the geolocation of the attacked system by its IP address. There lies another unusual feature of this malware — it has a typical ban list of countries for malware from Russia, though it does not include Ukraine. Instead, malware will exit once the IP of the attacked system is in Georgia. The latter has become quite a popular destination among Russians who try to avoid enlistment in the army. Overall, malware will not run in Armenia, Belarus, Georgia, Kazakhstan, Kyrgyzstan, Moldova, Russia, Tajikistan and Turkmenistan.

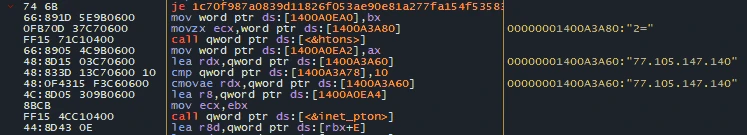
The very next step is contacting the C2 server. This step is not very common among stealers, as they prefer to knock back the C2 only after succeeding with data stealing. Instead, Meduza contacts the server immediately after ensuring that the system is not in the forbidden location – but without any strict actions. Malware sends the blank POST request, that does not receive any response from the server. Only once the connection is successful, malware will keep going.
Data Gathering
As I said, Meduza is distinctive for an outrageously wide number of web browsers, desktop apps, and crypto-wallets it can rummage through. More common malware samples usually stop on the most popular apps and wallets, including some from alternative options. This one, however, does not disdain even underdogs. Kinza, Mail.ru, Atom, Amigo – some of them are even considered PUPs by security vendors, and I bet you didn’t even know that some of them exist.
List of browsers Meduza gathers data from:
| Chrome | Chrome Beta | Chrome SxS | 360ChromeX | ChromePlus |
| Chromium | Edge | Brave Browser | Epic Privacy Browser | Amigo |
| Vivaldi | Kometa | Orbitum | Atom | Comodo Dragon |
| Torch | Comodo | Slimjet | 360Browser | 360se6 |
| Baidu Spark | Falkon | AVAST Browser | Waterfox | BitTubeBrowser |
| NetboxBrowser | Mustang | InsomniacBrowser | Maxthon | Viasat Browser |
| Opera Stable | Opera Neon | Opera Crypto Developer | Opera GX Stable | QQBrowser |
| SLBrowser | K-Meleon | Go! | Secure Browser | Sputnik |
| Nichrome | CocCoc Browser | Uran | Chromodo | YandexBrowser |
| 7Star | Chedot | CentBrowser | Iridium | Naver Whale |
| Titan Browser | SeaMonkey | UCBrowser | CLIQZ | Flock |
| BlackHawk | Sidekick | Basilisk | GhostBrowser | GarenaPlus |
| URBrowser | IceDragon | CryptoTab Browser | Pale Moon | Superbird |
| Elements Browser | Citrio | Xpom | ChromiumViewer | QIP Surf |
| Liebao | Coowon | Suhba | TorBro | RockMelt |
| Bromium | Kinza | CCleaner Browser | AcWebBrowserr | CoolNovo |
| SRWare Iron | Mozilla Firefox | AVG Browser | Thunderbird | Blisk |
| Cyberfonx | SwingBrowser | Mozilla IceCat | SalamWeb | SlimBrowser |
Browsers commonly have different ways to handle passwords and autofill info – and the malware has its approach for each one. For ones that store such data in databases, malware prepares an SQL database request, which simply extracts all the valuables. Other, less secure browsers, keep this info in a plain text file – which is not a big quest to find.
One more point of interest for stealer malware in web browsers is cookie files. Cookies can contain different things – from almost useless shopping cart contents to session tokens, usernames, emails, and the like. Cookie files can have a great value when it comes to data stealing – especially when they are fresh. One may say – just the like real ones.
Desktop apps
Aside from web browsers, Meduza Stealer gathers information from several desktop applications, namely Telegram, Steam, and different Discord clients. To put its hands on Steam session tokens, malware gets to the program’s registry key in the CurrentUser branch. The HKCU\Software\Valve\Steam key contains a lot of info, aside from login data and session information – so malware does not go purely for the account.
Telegram does not keep login details in such an accessible form, though malware manages to gather sensitive information similarly. By checking these two keys, Meduza can get information about the system kept in Telegram session info, app versions, usernames, and other important stuff.
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{53F49750-6209-4FBF-9CA8-7A333C87D1ED}_is1
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{C4A4AE8F-B9F7-4CC7-8A6C-BF7EEE87ACA5}_is1
Discord is also a tough nut when it comes to grabbing session info. For that reason, malware limits to only system info recorded in a session, app configurations, and the like. This, contrary to two other apps, is done directly in the programs’ folder. Malware attacks several different editions of Discord, as the free API allows the creating of forks and user modifications.
2FA Extensions
Well, did I say that Meduza is ravenous when it comes to data gathering? Hold your 2FA browser extensions close to your body – the malware hunts them as well. The list of add-ons it targets is not as big as that of browsers, though there are not many of them present.
| Extension name | Web Store ID |
|---|---|
| Authenticator 2FA | bhghoamapcdpbohphigoooaddinpkbai |
| Authenticator 2FA | ocglkepbibnalbgmbachknglpdipeoio |
| EOS Authenticator | oeljdldpnmdbchonielidgobddffflal |
| Trezor Password Manager | imloifkgjagghnncjkhggdhalmcnfklk |
| GAuth Authenticator | ilgcnhelpchnceeipipijaljkblbcobl |
| 1Password | oeljdldpnmdbchonielidgobddffflal |
| 1Password | dppgmdbiimibapkepcbdbmkaabgiofem |
| Dashlane Password Manager | fdjamakpfbbddfjaooikfcpapjohcfmg |
| Dashlane Password Manager | gehmmocbbkpblljhkekmfhjpfbkclbph |
| Bitwarden Password Manager | nngceckbapebfimnlniiiahkandclblb |
| Bitwarden Password Manager | jbkfoedolllekgbhcbcoahefnbanhhlh |
| NordPass | jbkfoedolllekgbhcbcoahefnbanhhlh |
| Keeper Password Manager | bfogiafebfohielmmehodmfbbebbbpei |
| RoboForm | pnlccmojcmeohlpggmfnbbiapkmbliob |
| RoboForm | ljfpcifpgbbchoddpjefaipoiigpdmag |
| SSO Authenticator | nhhldecdfagpbfggphklkaeiocfnaafm |
| Zoho Vault | igkpcodhieompeloncfnbekccinhapdb |
| KeePassXC | dppgmdbiimibapkepcbdbmkaabgiofem |
| KeePassXC | pdffhmdngciaglkoonimfcmckehcpafo |
| LastPass | hdokiejnpimakedhajhdlcegeplioahd |
| LastPass | bbcinlkgjjkejfdpemiealijmmooekmp |
| BrowserPass | naepdomgkenhinolocfifgehidddafch |
| MYKI | bmikpgodpkclnkgmnpphehdgcimmided |
| MYKI | nofkfblpeailgignhkbnapbephdnmbmn |
| Splikity | jhfjfclepacoldmjmkmdlmganfaalklb |
| CommonKey | chgfefjpcobfbnpmiokfjjaglahmnded |
| Authy | gaedmjdfmmahhbjefcbgaolhhanlaolb |
Cryptocurrency wallets
Gathering data about crypto wallets was not a widespread thing among older-gen stealers. With time, most of the families we know and love adopted such functionality. Modern-gen ones have them present by default, and it probably makes up for the number of names they can gather info from.
| MetaMask | Binance Wallet | BitApp Wallet | Coin98 Wallet |
| SafePal Wallet | DAppPlay | Guarda | EQUA Wallet |
| GuildWallet | Casper Wallet | ICONex | Math Wallet |
| Starcoin | Hiro Wallet | MetaWallet | Swash |
| Finnie | Keplr | Crocobit Wallet | Oxygen |
| MOBOX WALLET | Phantom | TronLink | XDCPay |
| Ton | Sollet | Slope | DuinoCoin Wallet |
| LeafWallet | Brave Wallet | Opera Wallet | CWallet |
| Flint Wallet | Exodus Web3 Wallet | Trust Wallet | Crypto Airdrops & Bounties |
| Nifty Wallet | Liquality | Ronin Wallet | Oasis |
| Temple | Pontem Aptos Wallet | Solflare Wallet | Yoroi |
| iWallet | Wombat Gaming Wallet | Coinbase Wallet | MEW CX |
| Jaxx Liberty | OneKey | Hycon Lite Client | SubWallet |
| Goby | TezBox | ONTO Wallet | Hashpack |
| Cyano | Martian Wallet | Sender Wallet | Zecrey |
| Auro | Terra Station | KardiaChain | Rabby Wallet |
| NeoLine | Nabox | XDEFI | KHC |
| OneKey | CLW | Polymesh | ZilPay |
| Byone | Eternl | Nami | Maiar DeFi Wallet |
This extensive list contains crypto wallets that can have both desktop and in-browser forms. In such cases, malware treats them in a separate way – by collecting data from registry entries they leave. Here are some examples of keys the malware can read to collect login data from your crypto wallet:
HKCU\SOFTWARE\Etherdyne\Etherwall\geth
HKCU\SOFTWARE\monero-project\monero-core
HKCU\SOFTWARE\BitcoinCore\BitcoinCore-Qt
HKCU\SOFTWARE\LitecoinCore\LitecoinCore-Qt
HKCU\SOFTWARE\DashCore\DashCore-Qt
HKCU\SOFTWARE\DogecoinCore\DogecoinCore-Qt
System fingerprinting
To distinguish between the attacked systems, stealers commonly collect some trivial info about the system. Meduza is not an exclusion – it collects all the basic things that can identify the computer among others.
- System build details
- Username
- Computer name
- Screen Resolution details
- Screenshot
- OS details
- CPU details
- RAM details
- GPU
- Hardware ID details
- Execute path
- Public Ip
- Geo
- Time
- TimeZone
Another application for such data comes into view when we remember that Meduza can also collect browser cookies. The combination of cookies, passwords, and system information allows for creating a complete copy of the device – at least from the POV of the website. There even were Darknet services dedicated specifically to the system profile spoofing – you input the cookies and system specs, and it makes your system indistinguishable from the original one. This helps with circumventing the most sophisticated protection mechanisms.
Data extraction
All the data Meduza Stealer manages to collect from the infected system is stored in a specific folder, created after the malware unpacking and execution. When it comes to sending the data to the command server, malware archives this data and sends it to the server – nothing unusual there. Since malware uses a protected connection for the C&C communication, it is not that easy to detect the extraction process.
Contrary to the “classic” stealers, like Vidar, Meduza does not perform the meltdown once it finishes data collection. It keeps running in the background, performing periodic pings to the C2 and waiting for commands. There is a command for self-removal – but they are most likely sent only in exclusive cases.
How to protect against Meduza Stealer?
Actually, the ways to protect against Meduza are the same as in the case of any other stealers. However, there is a difference dictated by the exceptional detection evasion capabilities of this malware. For efficient prevention of Meduza stealer activity, a strong heuristic protection is essential.
Be careful with all things that can act as a malware source. Email spam or phishing posts in social media are among the most exploited ways of malware spreading. A less popular, but sometimes even more efficient approach is exploiting Google Ads in search results. Fraudsters will do their best to make you believe that the thing is legit, and you should not fear interacting with it.
Implement preventive anti-malware measures. To weed out malware with such an unusual detection evasion model the program should include a sturdy heuristic engine. Additionally, you can seek solutions with email protection functions and CDR applications. They help you to secure one of the possible attack vectors.
Avoid cracked software. Yet another place used for malware spreading is cracked programs – they have served this purpose for over two decades now. And even since its share shrunk in recent years, you can still get something nasty from there. You can get dropper malware through the program crack, and it will then inject any other thing – from spyware to ransomware.
Meduza Stealer Removal

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.