On February 19, 2024, LockBit ransomware was taken down by the UK National Crime Agency in cooperation with a selection of other law enforcement agencies. The banner typical for such takedowns now illustrates all the web assets of LockBit ransomware. There is quite a hope about the possible release of decryption keys and even a decryptor tool.
LockBit Taken Down by NCA
On February 19, 2024, analysts noticed that the LockBit leak site on the Darknet went offline. Some time after, a banner stating about the takedown appeared. On that banner, the UK National Crime Agency claims about this being the result of a successful multinational law enforcement cooperation, called Operation Cronos. The text also contains the offer to visit the page the next day – on February 20 – to get more information.

That is not the first network asset takeover from law enforcement that high-end ransomware group suffers. A couple of months ago, a similar story happened to ALPHV/BlackCat, another infamous ransomware group. In their case, however, not all Onion websites were down, and they managed to get the access back. That in fact turned into a comic story, where the access to the site was more like a reversed hot potatoes game.
Nonetheless, the current takedown appears to be as serious as it can be. All the mirrors of their main Darknet site are now having the said banner. Well, it is possible for any miraculous thing to happen, but in my humble opinion, their onion infrastructure is done. Either this, or NCA will be quite ashamed for announcing details disclosure on 11:30 GMT, and failing to fulfill the promise.
International Law Enforcement Blocks LockBit Infrastructure
Shortly after the original news release, the info from LockBit affiliates arrived. VX-Undeground team shares a unique info and a screenshot taken by one of the gang members upon the attempt to log into the system.
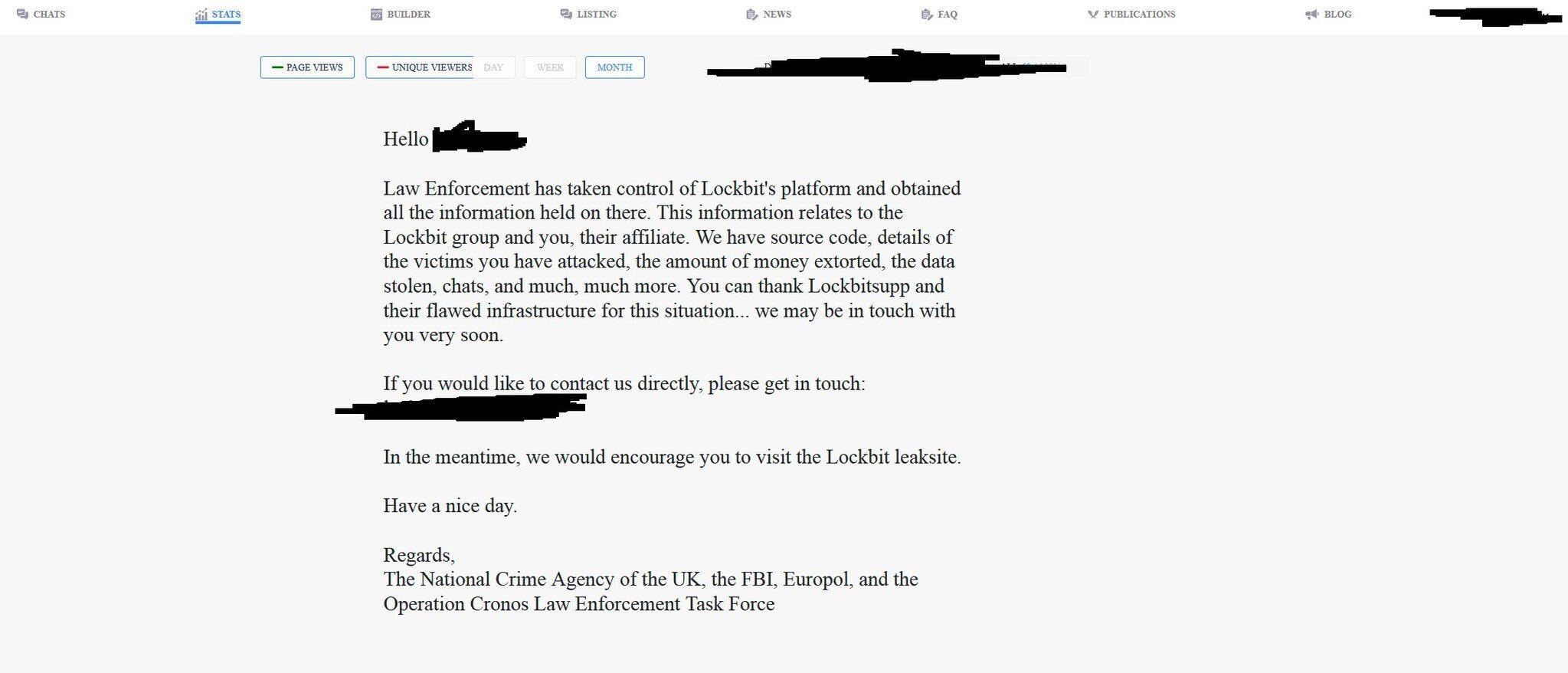
The text states the following:
Law Enforcement has taken control of Lockbit’s platform and obtained all the information held on there. This information relates to the Lockbit group and you, their affiliate. We have source code, details of the victims you have attacked, the amount of money extorted, the data stolen, chats, and much, much more. You can thank Lockbitsupp and their flawed infrastructure for this situation… we may be in touch with you very soon.
If you would like to contact us directly, please get in touch: [removed]
In the meantime, we would encourage you to visit the Lockbit leaksite.
Have a nice day.
Regards,
The National Crime Agency of the UK, the FBI, Europol, and the Operation Cronos Law Enforcement
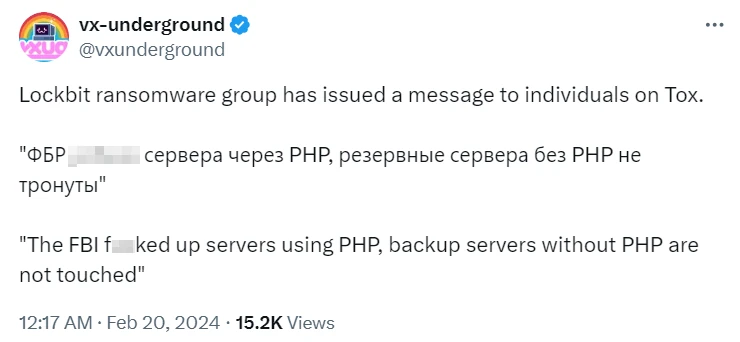
Another piece of info comes from the gang’s Tox chat. In a short message, they say about the PHP servers being taken over, while the non-PHP reserve servers being OK. Considering the use of obscene language, non-typical for LockBit representatives, the situation is rather tense, to say the least.
LockBit Decryptor Coming Soon?
What is more exciting than the info that will be published tomorrow is the thing that will follow. The takedown supposes leaking the decryption keys along with their proprietary decryptor tool. Maybe not all of them are available that easily, but accessing such a large chunk of internal info is definitely a key for exposing it all.
The fact of the leak and the decryptor being available is just miraculous for the victims. Sure enough, this will not delete the data the frauds have stolen from the network. But getting all the files back at no cost is much more important. And since it will work even for victims that failed the payment deadline, the question arises once again – why would you pay the ransom? It may be a much more reasonable option to just wait, and it looks like more and more ransomware victims stick to that opinion.
UPD 20.02 – LockBit Darknet Site Filled With Leaks and Announcements
On the designated time of 11:30 GMT on February 20, all of the LockBit’s sites that were taken over started redirecting to what used to be their leak page. Now, it is filled with the information gathered by law enforcement agencies. In particular, the information about the backend structure of the cybercrime network was revealed, demonstrating the screenshots of seized servers.
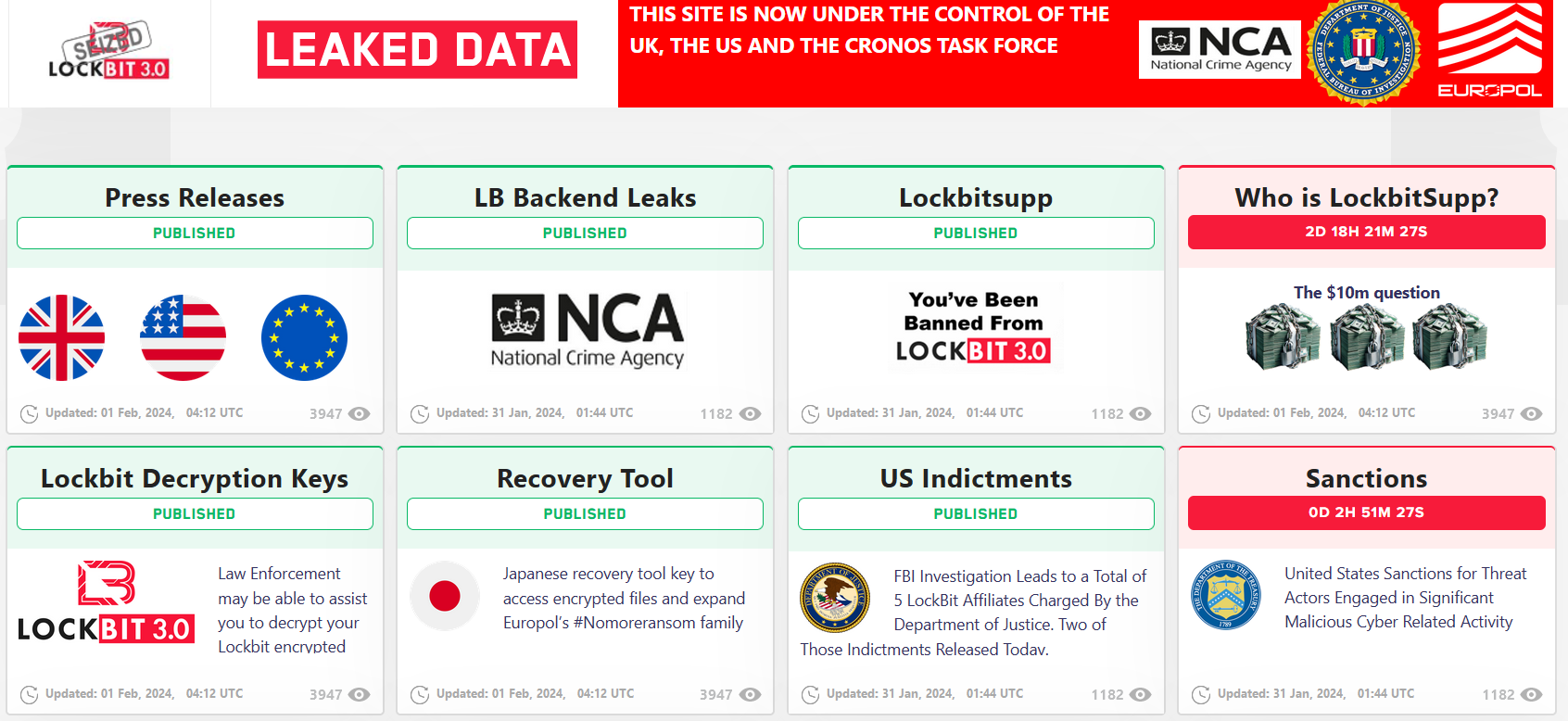
Aside from that, law enforcement added a tempting one – the info about the admin of the group, known as LockBitSupp. “The $10m question” will be answered on February 23, 2024. Some of the lower-ranked staff have already been arrested in Poland and Ukraine. Well, LockBitSupp did not lie by saying their group is multi-national.
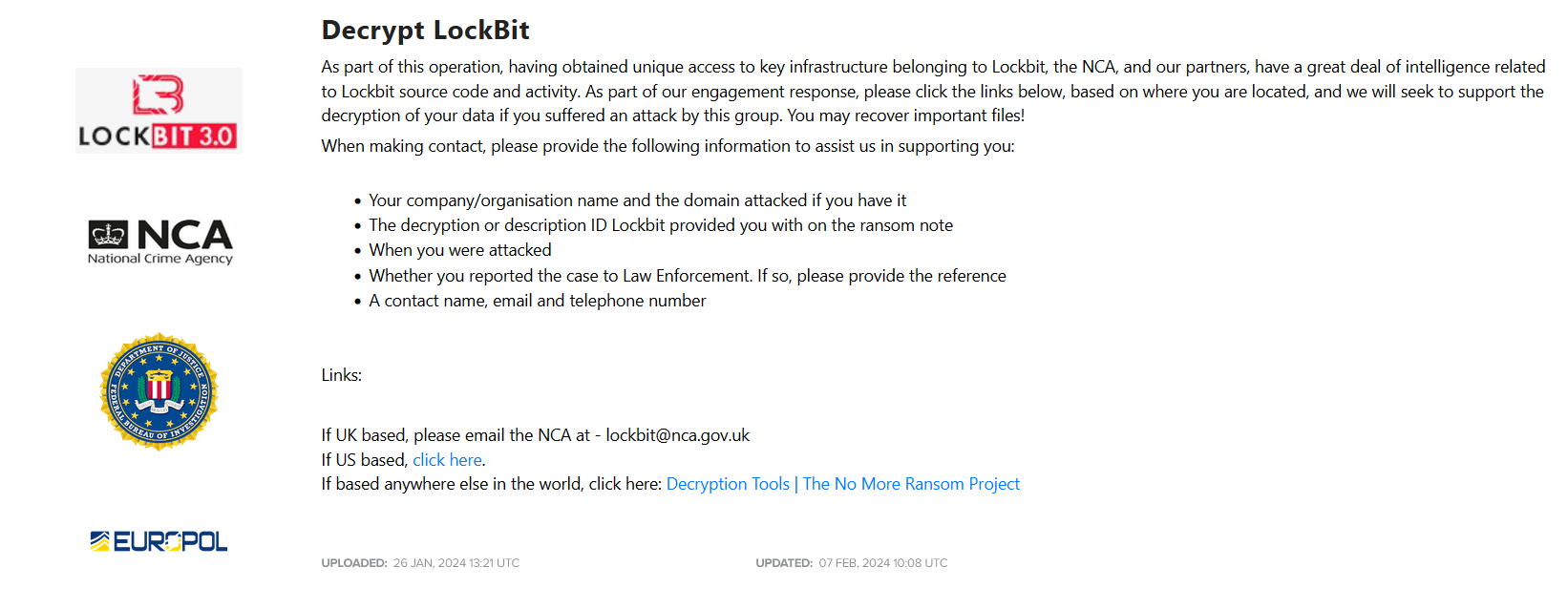
What is even better news is the confirmation of decryption keys release, as I’ve predicted in the original text. The keys, along with recovery tools, will be available to any victim upon contacting NCA for UK residents, IC3 for US and NoMoreRansom project for others.
What is LockBit Ransomware?
LockBit is one of the most successful ransomware groups that are currently active on the ransomware market. Its efficient software and meticulous attack planning rendered them dominant over the last few years. Their ransom sums are large, attacks are rapid and methods are as unprincipled as you can ever imagine. To be brief – nothing short of leaders in the cybercrime industry.
It is obvious that LockBit will eventually become a target for law enforcement, sooner or later. They were attacked before, but in a more mild form, that led to the temporal downtime or the urgent shift to a different software. Still, they were recognizing their mistakes and opening the entire bug bounty programs (!!) for people who can find issues in their software. This, along with continuous modernization of their software and updates to the online infrastructure is what made LockBit the image of unbreakable. And that is why the fact of the takedown set the community abuzz.





