Gridinsoft Security Lab
Jellyfish Loader Malware Discovered, Threatens 2024 Olympics
A new threat has been discovered in the form of a Windows shortcut that is actually a .NET-based shellcode downloader called Jellyfish Loader. It has some strange features that may signify that it is still at the development stage. Nonetheless, this malware is capable of deploying other malicious software in a selection of ways. Jellyfish […]
CSRF (Cross-Site Request Forgery) vs XSS
Cross-Site Request Forgery Cross-Site Request Forgery (CSRF) is an attack targeting vulnerabilities in computer security, posing significant risks to user information and accounts. It manipulates the web browser to perform unwanted actions within an application, harming the user logged into the system. A successful attack can lead to unauthorized money transfers, data theft, password changes, […]
Phishing vs Spoofing: Definition & Differences
What is a Phishing Attack? Phishing is a cyber-attack method that introduces malware to a computer via email. Intruders send users emails containing links under various pretexts. After clicking these links, the malware enters your computer. Thus, cybercriminals deceive the target to get as much data about the user as possible: his card numbers, bank […]
Trojan:Script/Downloader!MSR
Trojan:Script/Downloader!MSR is a malicious script that downloads other malware onto the target system. It is most commonly spread through illegal software and fake documents, and is capable of deploying pretty much any malicious program. Due to the complexity and the use of obfuscation, the exact malicious script may remain undetected, while the Defender will display […]
Trojan:Win32/Bearfoos.B!ml
Trojan:Win32/Bearfoos.B!ml is a detection of Microsoft Defender associated with data stealing malware. It may flag this malware due to the specific behavior patterns, assigning that name even to malicious programs of well-known families. As the Defender uses machine learning for this detection, it can sometimes be a false positive. Trojan:Win32/Bearfoos.B!ml Overview Trojan:Win32/Bearfoos.B!ml is a detection […]
Polymorphic vs Metamorphic Virus
Polymorphic and Metamorphic Malware: the Comparison In this article, we consider two types of pests: polymorphic and metamorphic viruses, which were designed to destroy the integrity of the operating system and harm the user. Before we find out what is the difference between polymorphic and metamorphic viruses, let’s figure out what is virus in general […]
Fake Instagram Hacking Services
Instagram hacking scams is an old-new direction of online fraud that targets people who want to get into someone’s accounts on social media. Frauds poison search results, gather the users interested in such a service and push them to shady pages or ones that promote commercial spyware. A key risk for users here is the […]
Stopabit Virus
Stopabit is an unwanted application that has almost no useful functionality. Users can see its promotions as a useful tool for screen time control, but it in fact aims at exploiting the bandwith. This may lead to connectivity issues and illicit traffic being routed through the system. Such applications are commonly distributed through software bundling. […]
Weather Zero
Weather Zero is a dropper-like unwanted program that disguises itself as a weather widget for Windows. It spreads as potentially unwanted software via bundling and can deliver malware to the target system. Its innocent looks make a lot of people ignore it or believe it is completely harmless and thus have little to no haste […]
Bloom.exe
Bloom.exe is a malicious miner that masquerades as a legitimate process. Its job is to use the victim’s device to mine cryptocurrency for con actors. The most visible sign of its presence, aside from the process in the Task Manager, is an enormously high CPU load that comes from it. This effectively renders your system […]
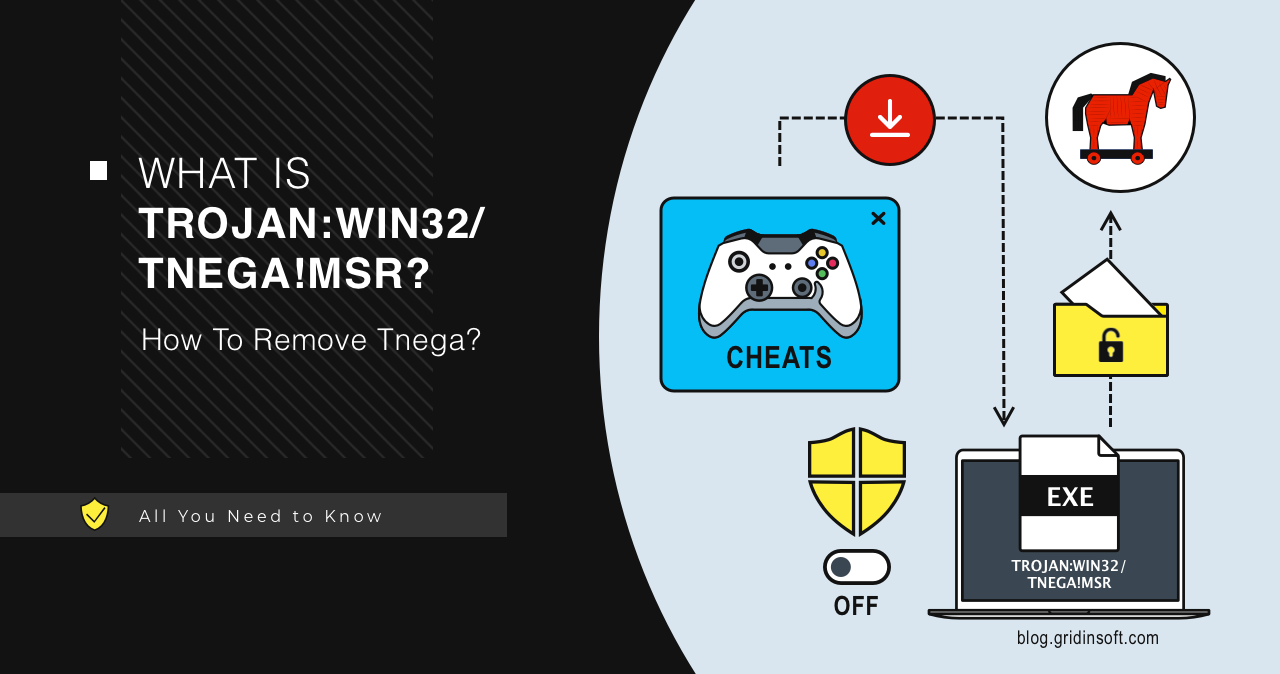
Trojan:Win32/Tnega!MSR
Trojan:Win32/Tnega!MSR is a malicious program that functions to deliver other malware. It uses numerous anti-detection tricks and is often distributed as mods and cheats for popular games. Such threats are capable of delivering spyware, ransomware and pretty much any other malware. Trojan:Win32/Tnega!MSR Overview Trojan:Win32/Tnega!MSR is a Microsoft Defender detection that refers to malware that acts […]
PUADlmanager:Win32/InstallCore: Complete Detection & Removal Guide 2025
PUADlmanager:Win32/InstallCore is a detection that Windows Defender antivirus uses to identify potentially unwanted applications (PUAs). This problematic software combines the functions of a downloader and installer, automatically distributing numerous unwanted applications and potentially dangerous programs to infected systems. While it may not initially appear as serious as other threats, the cumulative effects of InstallCore’s activities […]