Gridinsoft Security Lab
RedEnergy Stealer-as-a-Ransomware On The Rise
Researchers have discovered a new form of malware called RedEnergy Stealer. It is categorized as Stealer-as-a-Ransomware but is not affiliated with the Australian company Red Energy. A malware called RedEnergy stealer uses a sneaky tactic to steal sensitive data from different web browsers. Its fundamental spreading way circulates fake updates – pop-ups and banners that […]
Malware Propagation On Darknet Forums
The forums on the dark web are well-known for being a hub of cybercriminal activity, including an auction system. Here, bad actors can trade tips on hacking, share samples of malware, and demonstrate how to exploit vulnerabilities. For those who develop malware, Darknet communication platforms, specifically forums, became a perfect marketing platform. The developers of […]
Cloud Mining Scams Spread Banking Trojans
It’s no secret that cybercriminals are increasingly using mobile platforms as an attack vector lately. One example is a new Android malware. It spreads through fake cloud mining scams services and targets cryptocurrency wallets and online banking apps. Analysts dubbed this banking trojan as Roamer, though hackers may use different other malware for such attacks. […]
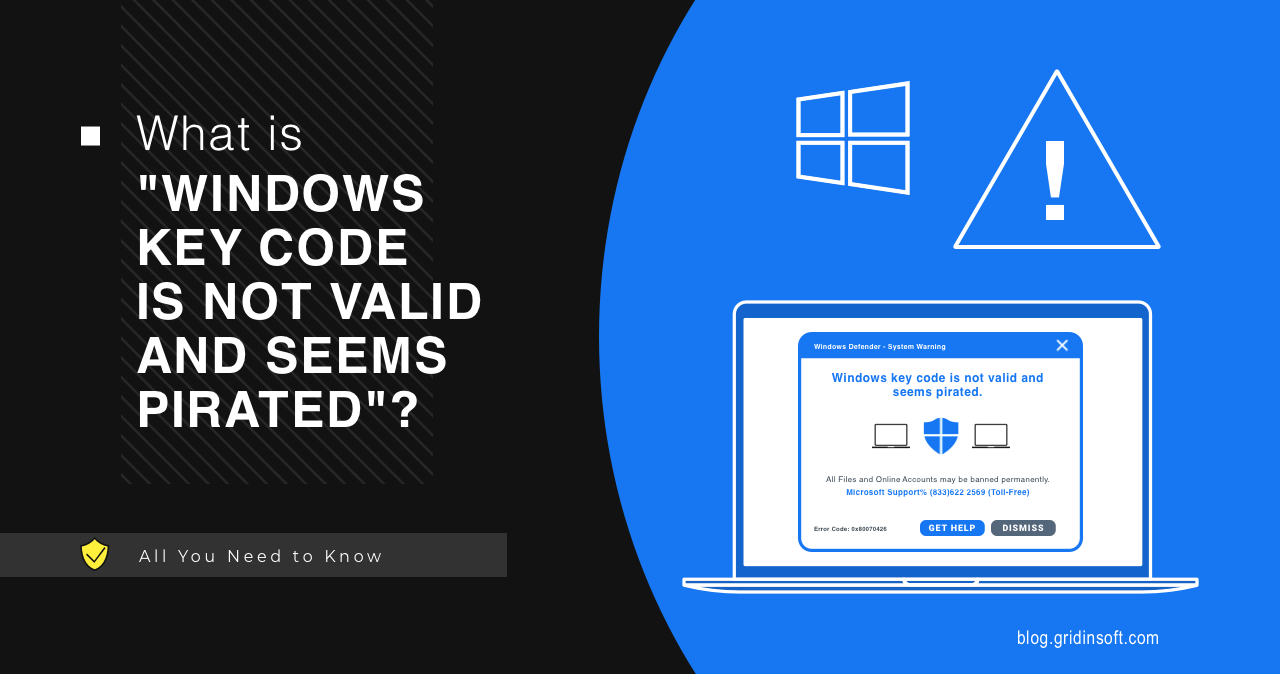
What is “Windows Key Code Is Not Valid And Seems Pirated”?
Windows Key Code Is Not Valid And Seems Pirated appears to be a new scary scam approach used to trick Windows users. Banners with this prompt may appear out of nowhere, and can really scare inexperienced users. Let me explain to you what’s the matter with this banner, if you really have any issues, and […]
What is Business Email Compromise (BEC) Attack?
Business email compromise attack, or shortly BEC, is a relatively new vector of cyberattacks. Dealing primary damage by exposing potentially sensitive information, also allows hackers to use the email for further attacks. The potential efficiency of these attacks is thrilling, and cyber criminals already apply them to conduct chain attacks. Let’s figure out a precise […]
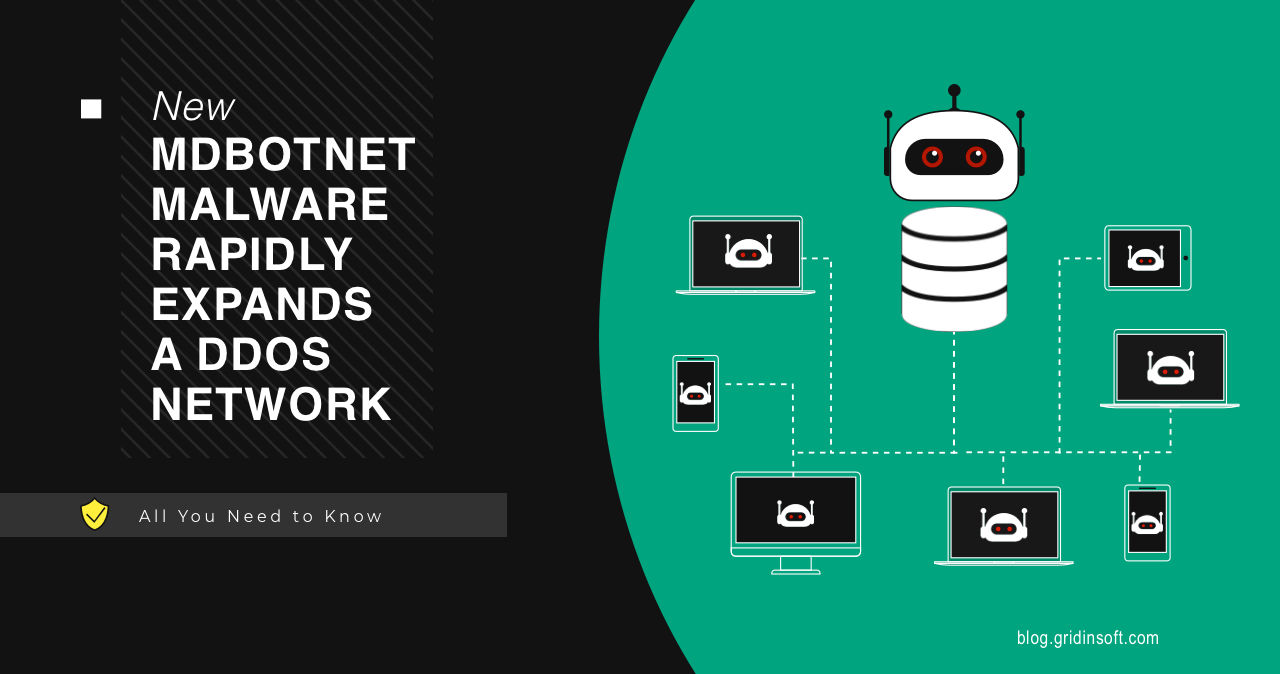
New MDBotnet Malware Rapidly Expands a DDoS Network
MDBotnet is a new malware strain that appears to be a backbone of a botnet, used in DDoS-as-a-Service attacks. Being a backdoor biassed towards networking commands, it appears to be another sample of russian malware. Analysts already report about the IPs related to this botnet being used in DDoS attacks. Let’s see why it is […]
GoDaddy Refund Phishing Emails Spread Infostealer
Hackers started using GoDaddy Refund Emails as a disguise to trick the users into installing malware. In order to deploy the payload, they opted for a particularly new tactic or, well, combination of ones. As a payload, a unique free open-source Invicta Stealer is used. GoDaddy Refund Email Phishing Being a widely popular web hosting […]
Ducktail Infostealer Malware Targeting Facebook Business Accounts
Researchers discovered Ducktail Malware, which targets individuals and organizations on the Facebook Business/Ads platform. The malware steals browser cookies and uses authenticated Facebook sessions to access the victim’s account. As a result, the scammers gain access to Facebook Business through the victim’s account, which has sufficient access to do so. It is a particularly interesting […]
RedLine Stealer Issues 100,000 Samples – What is Happening?
Throughout the entire early May 2023, GridinSoft analysts team observed an anomalous activity of RedLine stealer. It is, actually, an activity different from what we used to know. Over 100,000 samples of this malware appeared through the first 12 days of the month – that is too much even for more massive threats. Needless to […]
Fake Windows Update in Browser Deliver Aurora Stealer
Fake Windows Update became a malware spreading way once again. Updates are a pretty routine part of the Windows user experience. Over the last 7 years, Windows users mostly used to see the familiar update icon in the tray. Inexperienced people, however, do not know the mechanics of Windows update, and can be trapped with […]
LOBSHOT malware steals cryptowallets, exploits Google Ads
LOBSHOT, a recently-detected malware family, appears to be a new strong player in the malware market. Carrying a combination of backdoor and spyware functionality, it uses novice spreading ways that make it more effective. Its ability to provide Hidden VNC connections may be a go-to point for numerous cybercriminals. Let’s analyse this malware and see, […]
Domino Backdoor is Lead by FIN7 and Conti Actors
A new Domino Backdoor popped out at the beginning of 2023. Since February, a new malware family coined Domino is used for attack on corporations, having Project Nemesis stealer as a final payload. Analysts say that the new backdoor is controlled and developed by ex-TrickBot/Conti actors and hackers related to the FIN7 group. Who are […]