Integris Health, Oklahoma’s most extensive not-for-profit health network, fell victim to a sophisticated cyberattack, which compromised susceptible patient data. This unfortunate occasion got some really unusual results: patients of Integris Health in Oklahoma started receiving extortion emails. They threaten the sale of their data to other malicious actors if they fail to pay an extortion demand.
Integris Health Patient Data Extortion
By December 24, Integris Health patients reported receiving extortion emails. The attackers, claiming to have exfiltrated the personal data of over 2 million individuals, demanded payment to prevent the sale of this information. The extortion emails included links to a dark website where around 4,674,000 records were purportedly available.
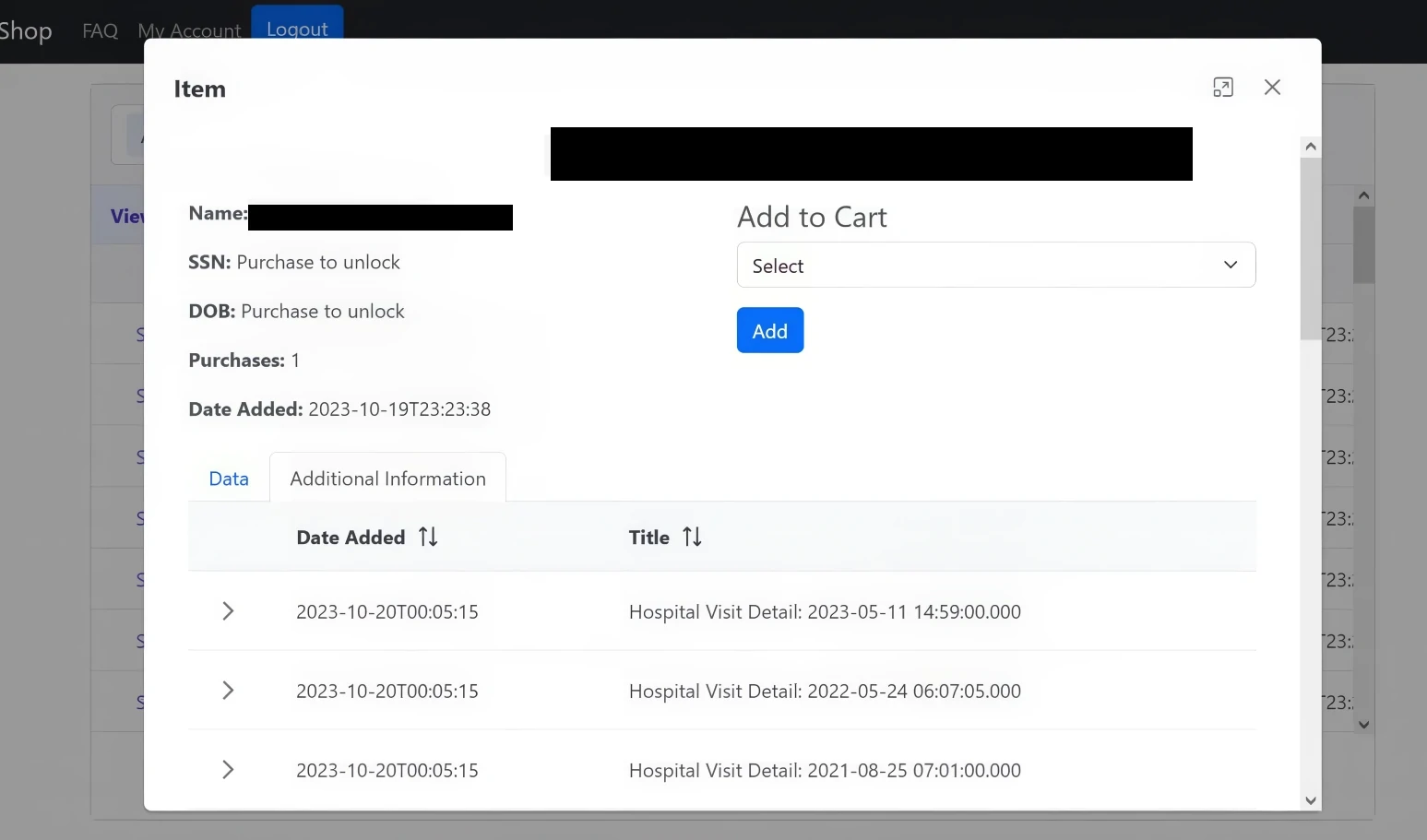
The website provided choices to either delete or view the data upon payment. However, it is unclear whether there are duplicate records among all of them. The compromised data comprised Social Security Numbers, birthdates, addresses, insurance, and employment details. This fact was confirmed by patients who identified their personal information in those emails.
Incident Background
In November 2023, Integris Health detected unauthorized activities within its network. An investigation revealed that an unidentified party accessed confidential patient files on November 28. It is unknown at this time exactly what information was compromised.
Integris Health reports that the investigation is still ongoing. However, given the attack’s scale, cybercriminals likely gained access to a wide range of data, including names, addresses, insurance policy numbers, dates of birth, medical records, and other personal information.
Integris Responds to Ransom Emails
Integris Health has updated its security advisory, warning patients against interacting with the extortion emails. Nevertheless, this incident follows a similar pattern to that observed in the Fred Hutchinson Cancer Center attack. It suggests a potential link between the threat actors.
The dilemma faced by victims is whether to pay the ransom to protect their identity. However, legends say that paying the ransom does not assure data security or deletion. It also potentially marks the payer as a target for future extortion attempts.
Is It A New Cybercrime Meta?
The tactic of contacting users whose data was leaked directly is rather new, but looks organic in the modern threat landscape. While ransomware gangs like BlackCat practice forcing the companies to pay by reporting the hacks to SEC, the hackers who stand behind the Integris hack opted for this peculiar approach. But overall, such unusual steps appear to be if not a new extortion method, then at least a way to enforce paying off the ransom.
The intimidation factor is what makes us blush most. When it comes to multi-billion dollar companies that are listed on stock exchanges – it is much more than just a feeling of embarrassment. It is unlikely for hackers to start texting all their victims, as such practice is simply counter-productive. With large companies, however, it is essential to expect and be ready for some unique new tricks hackers come up with.