Massive complaints come from Indian users regarding a new wave of SMS phishing scams, particularly targeting iPhones. They mimic delivery notification messages from India Post, one of the major postal services in the country. Fraudsters try stealing user credentials associated with that service, which may be the fuel of further scams.
Fraudsters Impersonate India Post in SMS Phishing
The wave of smishing messages started flooding mobile phones in India, specifically aiming for iPhones. These SMS look like just regular notifications about the incoming delivery, but with the mentions of some issues “due to incomplete address information”. To fix up the issue and let the service finish the alleged delivery, users should follow the link and fill in the missing details, and also pay a service fee.
As you may have guessed, neither the website by this link nor the message itself has any relation to India Post. What in fact happens is the adversary reaches the victim out through iMessage, using a newly-created iCloud account and the templated text. You can see the most common example below:
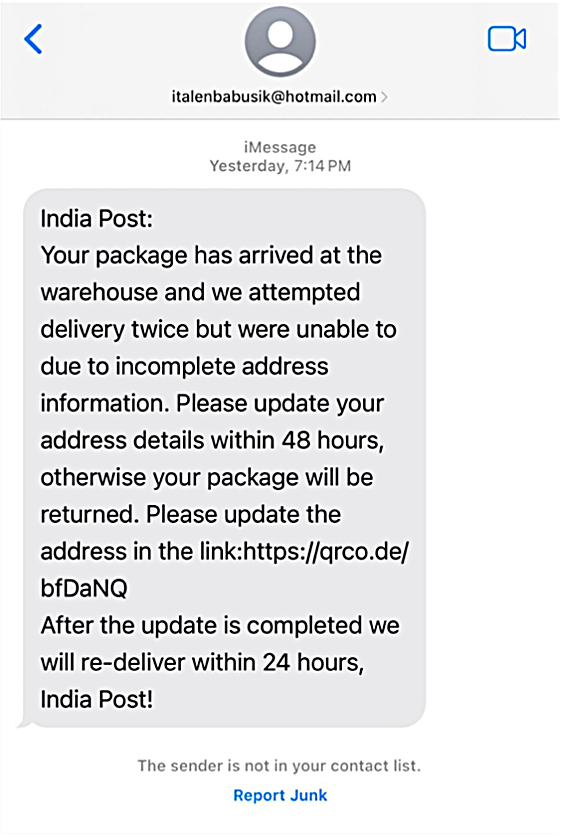
Original research published by Fortinet also features the list of domains that scammers use in that campaign. Their number – over a hundred at the moment of writing – gives out the tremendous scale of this phishing. It is unlikely, and simply irrational, to use one domain for just a few victims, so most likely, several thousand victims get through the malicious domain before it is taken down.
Fake India Post SMS Collect Credentials
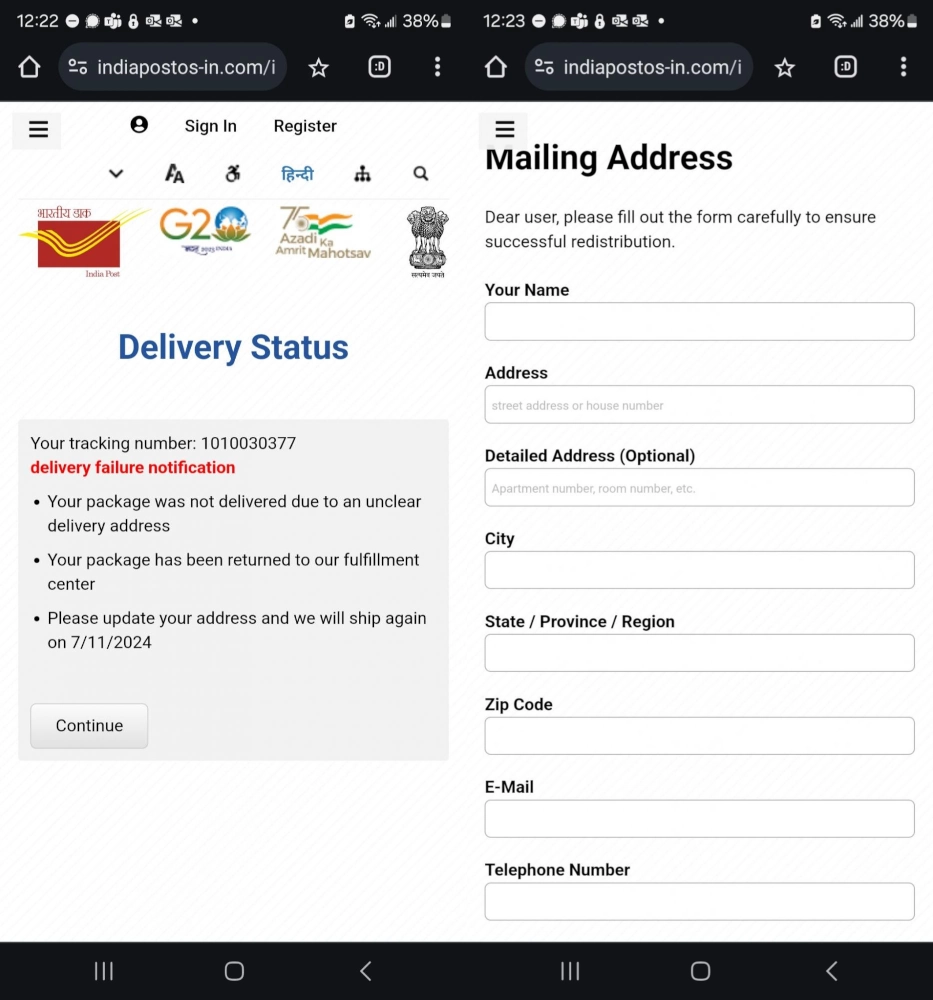
Main part of the scam is, actually, gathering what users type in the login forms of the fraudulent websites. Despite having different domain names, these sites are made by the same template, and are indistinguishable from one another. Nonetheless, the frauds managed to copy some of the elements from the original India Post page, so for someone who can’t exactly remember how it should look the fake will be rather convincing.
On the site, users are guided into sharing all kinds of their personal data. It requests their name, detailed address (including city, street, building and apartment number), ZIP-code, email and phone number. This pack of data is already enough for a wide range of impersonation attacks. But to add insult to the injury, adversaries also ask for a small fee “to finalize the delivery”. Banking data that one types into this form is likely stolen, too, so what looks like paying 25 rupees is in fact sharing all the savings from your card.
Chinese Smishing Triad Suspected Guilty
Same research says about signs of this fraud being a yet another campaign run by the Smishing Triad threat actor. This is a China-based group of criminals who, as their name supposes, are heavily involved in SMS phishing of different sorts. In previous years, that group was attacking Pakistan, UAE and even the United States. But their interest in a neighboring huge country, with citizens being quite malleable to phishing tactics, is rather expected.
Historically, their frauds were concentrated not only around identity theft or personal data collection. In some of the attacks, Triad were going for credit card data. Further, this info is sold to third parties on the Darknet, or used for cyber espionage purposes – being a Chinese cybercrime group creates some obligations before CCP.
How to Protect Against Smishing?
Same as other types of phishing, smishing attacks rely heavily on lack of user awareness about the possibility of this situation. Only by sharing info about the ongoing phishing campaign will you decrease the chances of your friends and family getting scammed in this, or a similar situation. Another part of personal education is remembering how postal companies typically communicate with their customers. That is not the first time fraudsters use this scheme, but it is SMS all the time – and they did not pick a service that really sends such messages even once.





