Google experts have warned that the Chinese “government” hack group APT41 is abusing the red team’s GC2 (Google Command and Control) tool. According to experts, GC2 was used in attacks on Taiwanese media and an unnamed Italian recruiting company.
Let me remind you that we also wrote that Chinese Hackers Injected a Backdoor into the MiMi Messenger, and more that Chinese Hackers Use Ransomware As a Cover for Espionage.
And also information security specialists reported that Three Chinese APT Groups Attack Major Telecommunications Companies.
The Google Threat Analysis Group (TAG) links this campaign to the hacker group HOODOO, also known as APT41, Barium, Bronze Atlas, Wicked Panda and Winnti. Typically, this grouping targets a wide range of industries in the US, Asia, and Europe.
Google Command and Control is an open source project written in Go and developed specifically for the red team.
Essentially, the project consists of an agent that is deployed to compromised devices and then connects to a Google Sheets URL to receive commands to execute. The received commands force the agent to download and install additional payloads from Google Drive or, on the contrary, steal data, “uploading” it to the cloud storage.
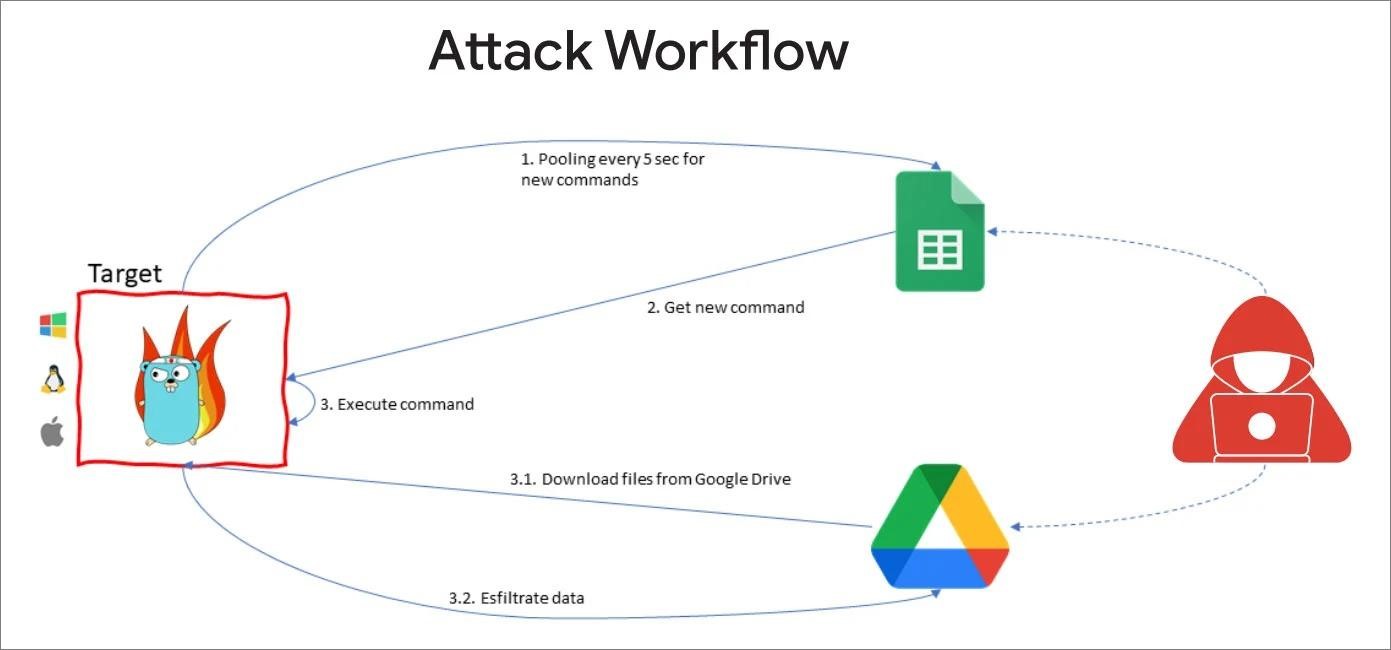
According to the TAG report, APT41 attacks start from phishing emails containing links to a password-protected file hosted on Google Drive. This file contains GC2, which penetrates the victim’s system.
While it is not known what additional malware was distributed with GC2 this time around, APT41 typically deploys a wide range of malware on compromised systems. For example, a 2019 report by Mandiant explained that attackers use rootkits, bootkits, custom malware, backdoors, PoS malware, and in some cases even ransomware in their campaigns.
The researchers write that this find is notable for two reasons: first, it shows that Chinese hackers are increasingly relying on freely available and open-source tools to make attacks more difficult to attribute. Second, it points to the growing proliferation of malware and tools written in Go, which is popular with attackers due to its cross-platform and modular nature.
Google also warned that “the undeniable importance of cloud services” has made them a profitable target for both “government” hackers and ordinary cybercriminals, who are increasingly using them “either as hosts for malware or as C2 infrastructure”.




