FIN8, an infamous group of cybercriminals, has updated its backdoor malware to avoid being detected. They made improvements and prepared to release a new type of crimeware called Noberus. This threat actor has returned after inactivity, using a modified version of their Sardonic backdoor to distribute the Noberus ransomware. This is a part of their typical approach of constantly changing and improving their malware arsenal.
Who are FIN8 a.k.a “Syssphinx”?
There is a financially motivated cybercrime group known as FIN8 or “Syssphinx” with a reputation for targeting various organizations without discrimination. They have been known to target companies in industries such as chemicals, entertainment, finance, hospitality, insurance, retail, and technology.
The malicious group FIN8 uses spear phishing and social engineering tactics to target victims while employing living-off-the-land techniques to conceal their activities. Recently, researchers discovered a new version of the Sardonic backdoor, initially identified by Bitdefender in 2021. Although the latest version is more extensive and has some differences, it may not necessarily be an improvement overall. The researchers noted that some of the changes seem unnatural and could be an attempt by the threat actors to avoid detection by disguising similarities with previous versions.
Updated Sardonic Backdoor Malware
Some hackers might update their malware after it has been discovered. Same happened with Sardonic in 2021, to bypass cybersecurity measures designed to detect it. The researchers found that the new Sardonic backdoor is very similar to the previous one. But it has many code changes that give it a unique look. However, these changes were not arbitrary. The updated version has added support for more plugin formats, which provides attackers with more options and enhances their abilities.
Experts have analyzed a new Sardonic backdoor variant written in C instead of C++, which was used for the previous variant. This backdoor was found to be embedded indirectly into a PowerShell script that is used to infect target machines. Unlike the last variant, this new variant doesn’t use an intermediate downloader shellcode to download and execute the backdoor.
This script in PowerShell decodes a binary file for .NET Loader and then loads it into the current process. The loader will then decrypt and execute both the injector and the backdoor.
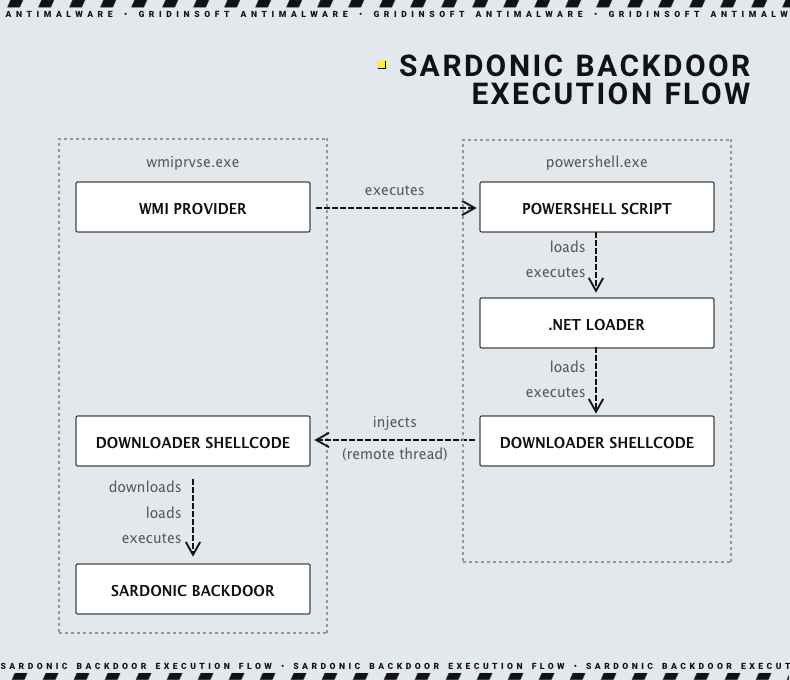
According to the researchers, the backdoor allows attackers to have interactive control over the infected system through processes such as cmd.exe. They analyzed a sample that showed the backdoor can support up to 10 simultaneous sessions. Additionally, the backdoor has three different formats to expand its capabilities: PE DLL plugins, shellcode, and shellcode, with a unique approach for passing arguments.
A sardonic backdoor can execute multiple commands, including dropping files from the attacker, sending the contents to the attacker, loading a DLL plugin provided by the attacker, and running the shell code supplied.
FIN8 and Ransomware Operations
Although FIN8 was known for focusing on point-of-sale (POS) attacks, in recent years, the group has been utilizing various ransomware threats as part of its attacks. Operations with ransomware are not something new for that group. The only difference here is the name of the final payload – Noberus. Noberus is, in fact, a well-known ransomware. It is a strain used generally by ALPHV/BlackCat (a.k.a FIN7) extortion gang.
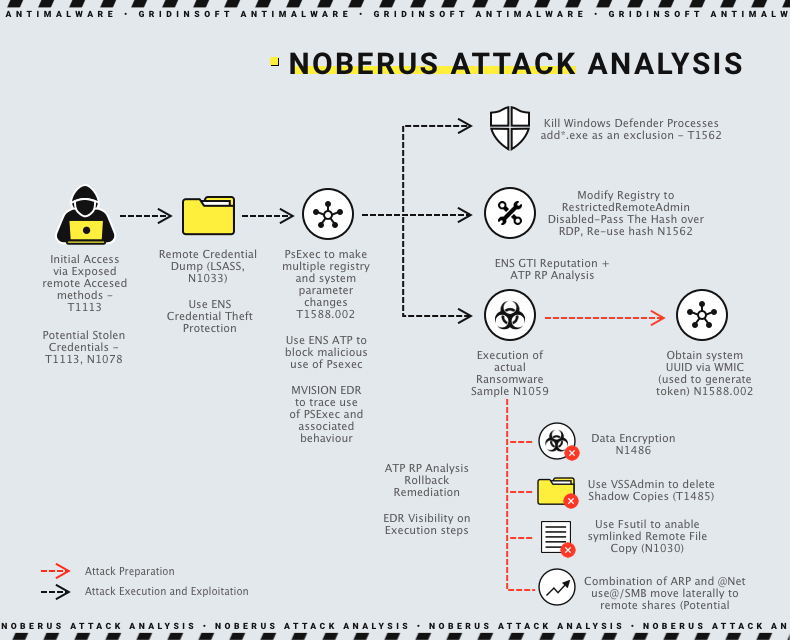
Noberus has several features that enhance its superiority over rival ransomware. These include providing an entrance through a unique onion domain architecturally excluding all possible connections with forums in the affiliate program. This makes it impossible for attackers to reveal the actual IP address of the server even if they obtain a full-fledged command line shell and encrypted negotiation chats that the intended victim can access.
The ransomware had two encryption algorithms available, ChaCha20 and AES, and four encryption modes – Full, Fast, DotPattern, and SmartPattern. The Full mode is the most secure but also the slowest. SmartPattern encrypts a certain amount of data in percentage increments. It defaults to encrypting 10 megabytes of every 10 percent of the file beginning from the header, making it the ideal mode for attackers regarding speed and cryptographic strength.
It’s just the beginning
The group FIN8 is constantly enhancing its abilities and infrastructure for delivering malware. They frequently refine their techniques to avoid being detected. Their recent shift from point-of-sale attacks to ransomware shows their commitment to maximizing profits from their victims. The Researchers share the tools and tactics this financially-focused threat actor uses, emphasizing their ongoing danger to organizations.
How to defend against organized cybercrime?
To protect against the ever-changing malware of FIN8, we suggest implementing a defense-in-depth strategy that involves using multiple layers of detection and protection tools and incorporating multi-factor authentication (MFA) and access controls.
Organizations can consider implementing one-time credentials for administrative work to prevent theft and misuse of admin credentials. It’s also a good idea to create usage profiles for admin tools, as attackers often use them to move undetected through a network.