The blue screen of death is probably the most unpleasant thing Windows users may ever see. In most cases, it is an alarming sign that something is wrong with your computer’s hardware or software. Some errors can mean that one or more components will soon be replaced. However, the Blue Screen of Death is not always what it claims to be. Resourceful hackers decided to employ the folks’ fear of BSOD and PC breakdowns.
How fake BSOD Messages Trick Victims
Today, unscrupulous tech scammers take advantage of users’ ignorance and trick them into believing there is a computer problem. Moreover, they charge their victims for unnecessary technical support or services. For example, researchers recently discovered a fake site with adult content that could cause harm to whoever visits it. The point is that every time a user opens the website, a malicious executable is automatically downloaded. Since this executable uses the VLC media player icon, it looks like a video file. Thus, an inattentive victim might try to open it thinking it is a video file.

As soon as the victim runs this file, the malware will do its dirty work. It will hide the mouse cursor from the screen and display a fake BSOD popup window covering the entire screen. However, unlike the blue screen of death, which contains a QR code and brief information about the error, the fake BSOD includes a phone number. This way, scammers try to make the user think that his PC is infected and to call the indicated number to solve the problem. If the victim calls the number, he will contact the scammers, who will, in turn, use social engineering, greatly exaggerating the “problem”. All this is done to convince the user to pay for useless technical support or product.
It’s a common tactic when tech scammers use executable files to commit scams. They usually send out emails with an attachment that looks like a legitimate document. However, the file contains malware that floods users with fake pop-ups urging users to pay for tech support or services. Most often, these are pseudo-antiviruses that masquerade as legitimate software but are malicious.
How fake Blue Screen of Death works
The Web site that contains the explicit content is located at hxxps[:]//mydoc.hsc-lb[.]net/, which has been determined to be a subdomain of hsc-lb[.]net. This domain impersonates the healthcare provider Hopital Du Sacre Coeur in Lebanon. A peculiarity of the website is that whenever a user visits the site, there is a redirect to hxxps[:]//mydoc.hsc-lb[.]net. /milf-pornvideo-pornhubdviideos[.]exe and starts downloading the malicious executable. Since the site uses the auto-download function in the background, and most web browsers automatically download files to the default download directory, most users won’t notice when the file is already in the download folder.
An executable file is intended for Windows users and is a 32-bit .NET binary file. Fraudsters changed the timestamp of this file to interfere with the incident response process. Once executed, the binary creates a Windows form named “Form1” and uses the Resources.ResourceManager.GetObject method to retrieve the background image of that form from the resources directory. As mentioned above, although visually it looks like a BSOD, it is a fake popup because the real messages contain an error message and not a phone number.
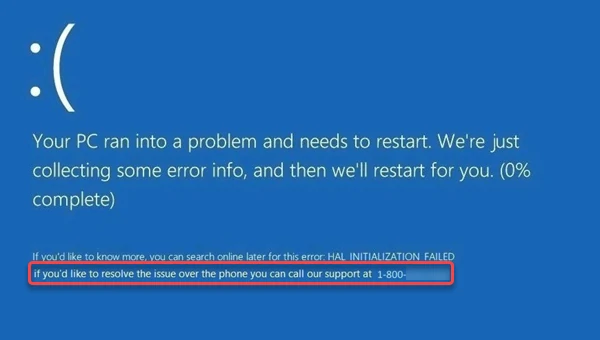
To be more realistic, the malware uses the Screen.PrimaryScreen.Bounds property to fill the entire screen and the cursor.hide() method to hide the cursor. The binary also initializes a SoundPlayer object named “soundPlayer” with an audio file named “backgroundmusic” which is also located in the resource directory of the executable. The Play() and PlayLooping() methods of the SoundPlayer class are used to play and loop the audio file. The audio message states that the user’s computer has been blocked because of a virus infection or illegal activity. To unblock it, you need to call the fake helpdesk immediately.
How to avoid fake BSOD
As we can see, scammers use various strategies to mislead users. Often these are methods of intimidation and psychological impact, such as audio and visual messages, which make users contact a fake support number. The following recommendations will help you avoid potential problems:
- Don’t click on links that seem suspicious.
- Make sure you’re downloading from trusted sources.
- Avoid technical support or services offered through unsolicited messages or calls.
- Update your operating system and software regularly. It’s necessary to fix any security vulnerabilities.
- Use reliable antivirus software. It will prevent you from launching and sometimes downloading a malicious file.
In addition, you can change your browser settings and set the browser to ask you to choose a download location or even block downloads altogether. Most browsers provide settings to control file execution and warn you about possible threats to opening downloads from Web sites.





