Fraudsters are using fake websites and Facebook Ads to steal users’ financial data. Researchers named the campaign Eriakos after the CDN that fraudsters used in all campaigns.
Facebook Ads Steal Credit Card Information
On April 17, 2024, specialists from Recorded Future discovered a fraudulent campaign with Chinese origins that had targeted Facebook users. They named it Eriakos after the content delivery network (CDN) oss.eriakos[.]com that scammers used in most cases.
In brief, scammers created a selection of fake shopping websites that impersonate well-known brands and advertised them through Facebook ads. These sites lure people into buying from them by offering huge discounts (53%, 75%, etc.) that are available for a limited time. Additionally, scammers use different tricks to bypass automated detection systems to avoid being blocked.
The final goal of this scam is to steal confidential data, particularly payment information. As it usually goes for delivery orders, the user should specify their delivery address, postal code, phone number, email, and real name. And as the site is controlled by cybercriminals, they’ve managed to gather all the sensitive data input in a rather easy manner. To top this all up, the payment is also done on the same scam page, so all the bank card data will get to the frauds, too.
Eriakos Facebook Ads Scam Details
Researchers discovered a total of 608 fraudulent websites that imitated popular brands. The scammers used several tricks, which we will discuss further, to avoid detection and continue their malicious activities.
Social Engineering
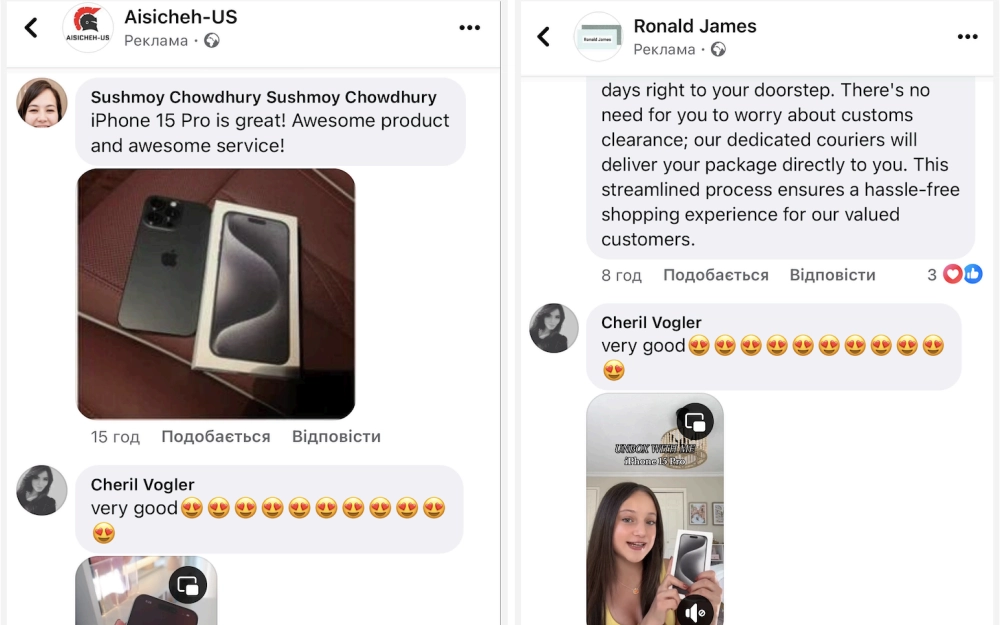
This classic tactic in online fraud aims to prevent the victim from taking time to think. The fraudulent site uses a countdown timer with text like “Time left for the sale: xx:xx”, which resets upon refreshing the page. This advertisement also includes “reviews from people” who supposedly bought the product. In reality, these reviews are fake and serve to lull the victim into a false sense of security.
Detection Avoidance
Users primarily land on such sites through Facebook ads. Researchers noted over a hundred Meta Ads related to a single fraudulent site can appear every day. To avoid automated detection systems, scammers designed the sites to target mobile users exclusively. This means that before opening the site, a check based on referrer and user-agent headers is performed, and if the site is accessed from a PC, it simply doesn’t open.

CDN and Domain Registrar
Another noteworthy detail is the domain registration location. All their domains were registered with Alibaba Cloud Computing Ltd. They also used a single CDN oss[.]eriakos[.]com. On the other hand, the www subdomains were registered under Cloudflare. This should have mixed the tracks for anyone who was about to research the scam.
How To Stay Safe
Today, we increasingly see fraudulent schemes targeting human inattention or lack of awareness. To avoid falling victim to such schemes, users should be particularly vigilant when making online purchases. I recommend refraining from buying items advertised through social media ads. Instead, consider purchasing the desired item from official stores.
If you still decide to make a purchase through marketplaces, be sure to conduct your own research and investigate the store, the seller, and the desired product. Do not rely solely on reviews directly on the current page. Instead, search for the product online. Use a URL scanner to check the online store’s address. Finally, check out our post on this topic.
Consider using anti-malware solutions as an additional preventive measure. GridinSoft Anti-Malware includes an Internet Security module that can automatically block suspicious and fake websites.