A proof-of-concept exploit for the CVE-2023-21716 vulnerability in a Microsoft Office product, namely Microsoft Word, has emerged online. This issue has been rated 9.8 out of 10 on the CVSS Vulnerability Scoring Scale and can be used for remote code execution attacks via a malicious RTF file.
Let me remind you that we also wrote that Weak Block Cipher in Microsoft Office 365 Leads to Message Content Disclosure, and also that Microsoft Will Block Excel XLL Files Downloaded from the Internet.
The media also wrote that Experts have published an exploit for a 0-day vulnerability in Windows MSHTML.
Vulnerability CVE-2023-21716 was discovered by information security specialist Joshua Drake in the Microsoft Office wwlib.dll file and fixed by Microsoft developers in February this year.
As the company’s engineers warned, a remote attacker could use the bug to execute code with the same privileges as the victim who opened the malicious .RTF document. There are many ways to deliver a malicious file to a victim, for example, as an attachment to an email.
At the same time, to exploit the bug, user don’t even need to open a malicious document: for compromise, it will be enough to download the file in the preview mode (via the Preview Pane).
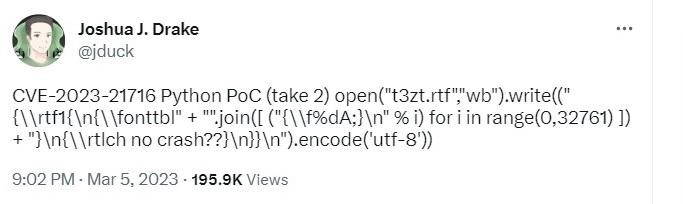
As Drake has now explained, Microsoft Word’s RTF parser has a heap corruption issue that is triggered “when working with a font table (*\fonttbl*) containing an excessive number of fonts (*\f###*)”. According to the expert, after memory corruption occurs, additional processing occurs, and a hacker can use the error to execute arbitrary code, creating a “correct heap structure.”
The researcher’s PoC exploit, which he reported to Microsoft immediately after discovering the bug and which has now been made public online, demonstrates the hip corruption issue and also launches the Calculator app on Windows to demonstrate the execution of the code.
Initially, the exploit consisted of about ten lines of code, including comments. Now, the researcher has slightly reduced it and managed to fit the entire exploit into one tweet.
According to Microsoft representatives, no evidence has been found to indicate continued active exploitation of the vulnerability. Apart from the fixes, Microsoft has also suggested workarounds to fix the error, including reading email in text format and activating the Microsoft Office file blocking policy, although the latter can be difficult.




