The Cisco Talos security team has released information about a new campaign of attackers targeting mass account compromise. Specialists have recorded countless login attempts to gain unauthorized access to web infrastructure, particularly SSH servers, VPN clients and web applications. This is alarming and frightening for both big companies and home users.
Cisco Reports Massive Brute Force Attack
The first observed attacks date back to March 18 of this year. Cisco announced the last warning of this campaign three weeks ago. At that time it was a “password spray” method targeting VPN access.
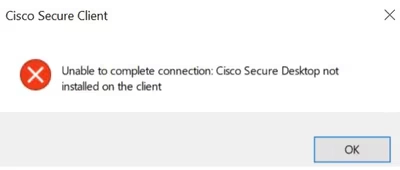
During the attacks, adversaries attempted hundreds of thousands or even millions of failed authentication attempts. Some login attempts ended with the error “Unable to complete connection. Cisco Secure Desktop not installed on the client” error. Specialists also record problems with hostscan token allocation<.
Attackers use a wide range of credentials, from commonly known usernames to organization-specific credentials. Researchers on GitHub list more than 2,000 usernames and nearly 100 passwords involved in the attacks, as well as approximately 4,000 IP addresses from which connections were made. The addresses listed come mostly from TOR exit nodes and other anonymizing tunnels and proxies. Experts note that the attacks are non-targeted and opportunistic in nature, not focused on any region or industry.
According to research, attackers target the following resources:
- Draytek
- Checkpoint VPN
- Cisco Secure Firewall VPN
- Fortinet VPN
- RD Web Services
- SonicWall VPN
- Mikrotik
- Ubiquiti
The following code displays a log entry where an unauthorized user attempted to access the Cisco VPN service, but their login was unsuccessful.
{"timestamp": "2023-01-0311:38:35. 000Z", "user": "unknown", "account": "*****", "result" : "FAILED_BAD_LOGIN" ,
"source_ip": "62.204.41.146", "service": "vpn", "geoip_country_code": "RU", "geoip_country_name": "Russia", "geoip_organization": "Horizon LLC", "source_data":"<166>Jan 03 2023 05:38:35 FW : %ASA-6-: Group User <*****> IP <62.204.41.146> Authentication: rejected, Session Type: WebVPN. "}
{"timestamp": "2023-01-06T11:03:59. 000Z", "user": "TestUser", "account" : "test", "result": "FAILED_BAD_LOGIN", "source_ip": "179.60.147.152", "service": "vpn", "geoip_city": "Moscow", "geoip_country_code" : "RU" , "geoip_country_name" : "Russia", "geoip_organization": "Flyservers S.A.", "geoip_region": "MOW", "source_data" : "<166>Jan 06 2023 05:03:59 FW-%ASA-6-: "}
Potential Risks
Penetrating corporate networks through VPNs or servers can give attackers access to sensitive information such as personal data. Also, through unauthorized access to VPNs, attackers can distribute malware within a company’s network, which can lead to infections of workstations and servers. Additionally, unauthorized access eventually leads to data leaks. This is unpleasant on it own, and also violates regulatory requirements such as GDPR or HIPAA, resulting in severe fines and legal consequences for the company. The number of such attacks has been increasing over time, and this trend is expected to continue.
Cisco Protection Recommendations
Cisco has provided a series of recommendations to strengthen security and prevent successful cyberattacks. These suggestions are part of the described account hacking campaign. Here are the key recommendations for organizations to minimize risk and better protect their information systems:
- Detailed logging should be configured, with logs going specifically to a remote syslog server. This allows administrators to recognize and correlate attacks across different points in the network, which is critical for rapid incident response.
- It is recommended that default remote access accounts be sinkholed. Access to these accounts should be limited or completely denied if they use the DefaultRAGroup and DefaultWEBVPNGroup profiles.
- It is recommended to use blocking lists to prevent access to VPN services from IP addresses known to be malicious.
- Configuring interface-level access lists and control planes will help filter out unverified public IP addresses and prevent them from being able to initiate remote VPN sessions.
- The shun command in Cisco IOS allows the administrator to block malicious traffic from specific IP addresses, which prevents further attack attempts.