Cisco has rolled out security updates to fix two critical vulnerabilities in its Identity Services Engine (ISE). If exploited, these flaws could allow remote attackers to execute commands as root.
Cisco Identity Services Engine Authorization Bypass Vulnerabilities
Cisco has released critical security updates for its Identity Services Engine (ISE) after discovering two serious vulnerabilities. These flaws could allow attackers to gain elevated privileges and execute commands as the root user.
Cisco Identity Services Engine is a security policy management platform that secures network access for users and devices. It simplifies identity management for endpoint devices connected to an organization’s network, providing visibility into who is connected and what applications are active.
Both flaws require authentication but can be exploited remotely, meaning that the hacker may not even have a foothold in the infected system. Attackers could use them to manipulate system configurations, extract sensitive data, or completely compromise affected devices.
Details of the Vulnerabilities
The two security flaws, both affecting the API (Application Programming Interface) of Cisco ISE, have been classified as follows:
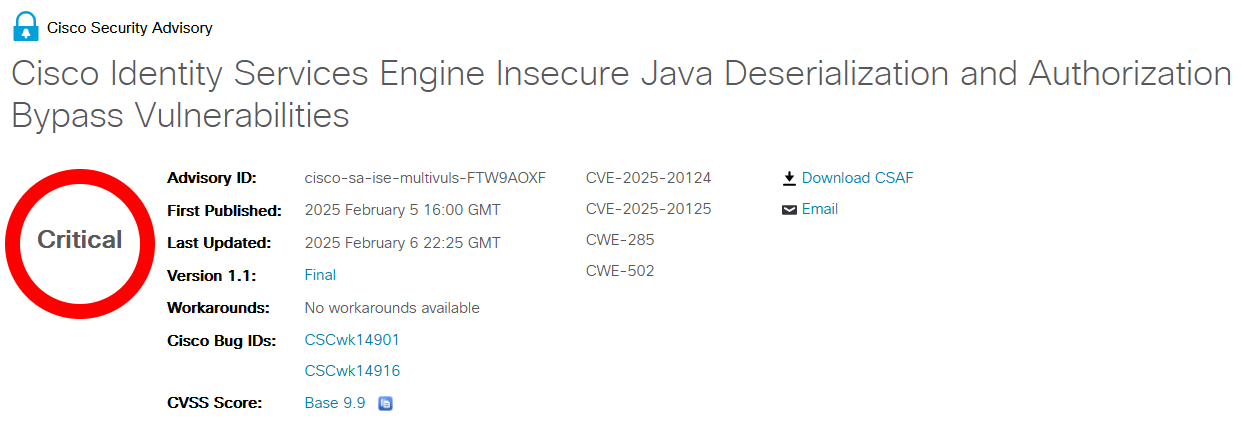
CVE-2025-20124, rated at CVSS 9.9, is an insecure Java deserialization vulnerability within an API of Cisco ISE. Insecure deserialization occurs when untrusted data is used to abuse the logic of an application, inflict a denial of service (DoS) attack, or execute arbitrary code.
In this case, an attacker could exploit this flaw by sending a crafted serialized Java object to the vulnerable API endpoint, leading to command execution as the root user. That, in turn, opens flood gates for any kind of malicious activity, yet most typically it would be used to deploy dropper malware or backdoors.
The second flaw, CVE-2025-20125 (CVSS 9.1), is an authorization bypass vulnerability in an API of Cisco ISE. This flaw allows an attacker with valid read-only credentials to send a crafted HTTP request to an unspecified API endpoint. As a result, the attacker can obtain sensitive information, alter node configurations, and restart the node — actions that should typically require higher privileges.
These vulnerabilities are independent of each other, so exploiting one does not necessitate exploiting the other. Yet upon discovery and publication of the flaw, the probability of it being exploited grows by orders of magnitude.
How Does It Work?
An attacker could take advantage of these vulnerabilities by sending a specially crafted serialized Java object to exploit CVE-2025-20124 or by sending a manipulated HTTP request to an unspecified API endpoint to exploit CVE-2025-20125. Since these flaws are independent of each other, they can be used separately.
Due to their high severity, a successful attack could grant full administrative control over Cisco ISE deployments. This could potentially lead to system compromise and unauthorized access to sensitive data.
Patch Now!
As of now, Cisco has not found any evidence of these vulnerabilities being actively exploited. However, given the critical severity and potential impact, organizations using Cisco ISE should immediately update to the latest patched versions. The developer also has confirmed that no workarounds exist to mitigate these vulnerabilities, making patching the only viable solution. The issues have been addressed in the following fixed versions of ISE:
- 3.0 – Requires migration to a fixed release
- 3.1 – Fixed in 3.1P10
- 3.2 – Fixed in 3.2P7
- 3.3 – Fixed in 3.3P4
- 3.4 – Not vulnerable




