The Conti Ransomware Ceases Operations and Breaks Up into Several Groups
Experts report that the Conti ransomware is going out of business, group ceases operations, its infrastructure is disabled, and the group's leaders have said the brand already does not exist.…
10 Signs That Your Computer Is Infected With Spyware
What Is Spyware? It is a malicious program that secretly gets installed onto your device. Sometimes you can get it by downloading it together with other usually freeware programs and…
Cybersecurity Experts Analyzed the Methods of a Group of Russian Hackers Wizard Spider
Information security specialists from PRODAFT have published the results of an investigation into the Wizard Spider group, which is allegedly associated with the Grim Spider and Lunar Spider hacker groups.…
TOP Facts About Adware Attacks To Be Reminded Today
To begin with, each of you has faced this challenge. Namely, the infestation with advertising: pop-up windows, banners on your screen left and right when you want to do your…
Antivirus Is Important! Advantages Of Using
If you are one of those people who are contemplating whether to buy a new antivirus solution, we can only envy your confidence. These days going into the cyber world…
Information Security Specialist Showed How to Steal a Tesla Car
Sultan Qasim Khan, a security consultant of the NCC Group, has disclosed a vulnerability that allows attackers to enter the salon and steal a Tesla car. The vulnerability consists of…
Germans Interested in the Situation in Ukraine Are Attacked by the PowerShell RAT Malware
An unknown hacker attacked German users who are interested in information about the Russian invasion of Ukraine, infecting them with PowerShell RAT malware (more precisely, a remote access trojan) and…
Microsoft Has Not Fully Coped with PetitPotam Attacks in Windows NTLM Relay
In May, Microsoft released a security update, as it had previously not fully coped with attacks called PetitPotam. The update and mitigation recommendations target a heavily exploited vulnerability in NTLM…
What is SSL Certificate?
Many of us have probably noticed various security-related markings around browsers' address bars, but our understanding of what it all meant remained vague. These things are a closed padlock icon,…
LockBit attacks the Canadian defensive co. Top Aces inc
Canadian defense contractor Top Aces Inc became the victim of a ransomware attack. LockBit group, an infamous ransomware gang known for its strict principles, already claimed responsibility. They boasted of…
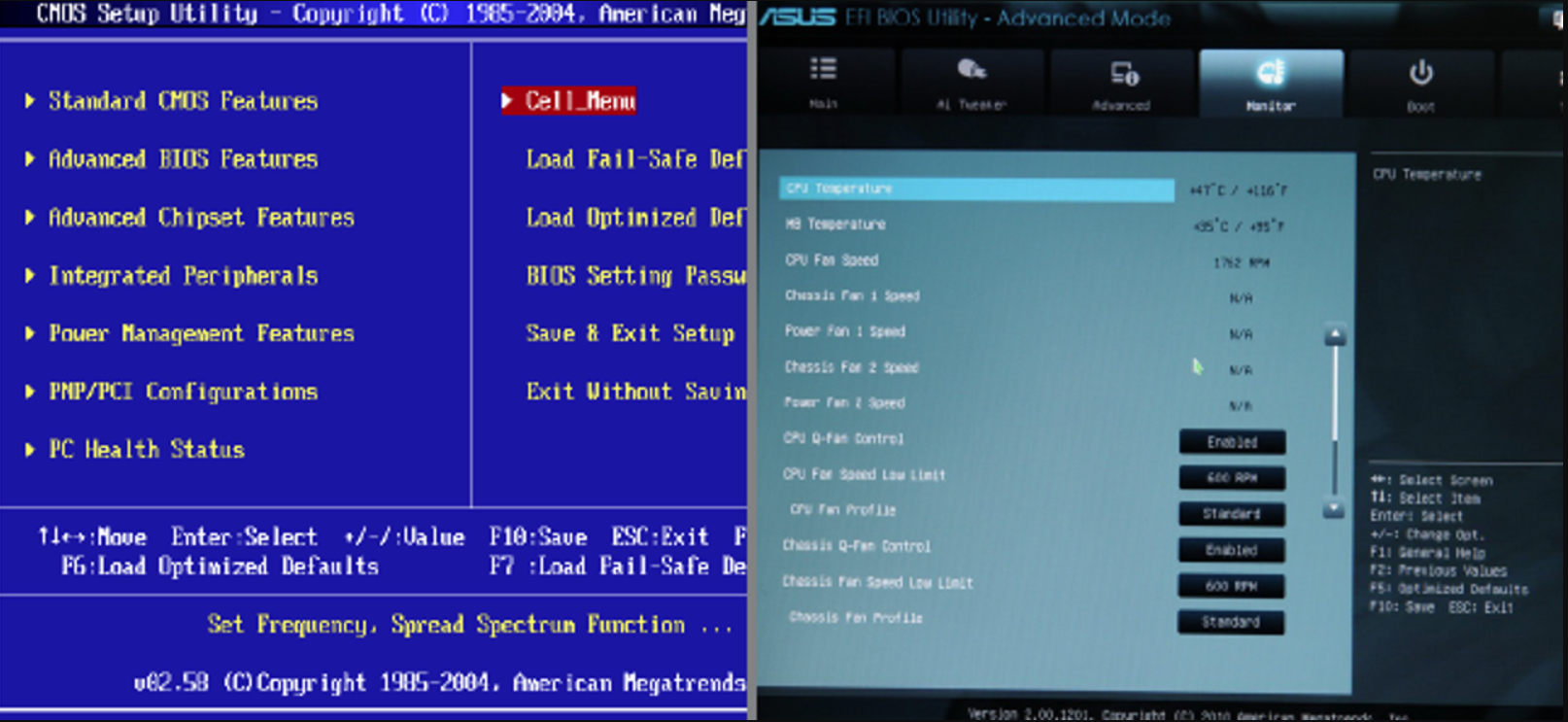
Vulnerability in HP BIOS causes system takeover
Following recent fixes for a large number of UEFI vulnerabilities, worldwide-known PC and laptop vendor HP is releasing a new BIOS update. This time around, two serious vulnerabilities affecting a…
The 5 Most Famous Spyware Attacks
Spyware can be called the most sophisticated malware these days. It never acts openly, uses tricky techniques, and appears more often with other viruses. Together with its brother-in-law - stealer…