Information security specialist Brian Krebs found out that even before the arrests, the Lapsus$ hack group managed to compromise the telecom giant T-Mobile.
The company confirmed this information, saying that a few weeks ago, hackers penetrated the company’s network, gained access to internal tools and source codes. It is emphasized that at the same time, the attackers were unable to steal confidential information about T-Mobile customers.
Let me remind you that we have already talked about the strange hack group Lapsus$, which blackmailed Nvidia, leaked the source codes of Microsoft, as well as Ubisoft, and Samsung, compromised Okta, but fame for hackers was clearly more important than financial gain.
The well-known investigative journalist Brian Krebs, who has specialized in information security for many years and has repeatedly exposed various hack groups and helped law enforcement officers in their investigations, reported on the T-Mobile hack.
Krebs, who got into the private chats of the group members, writes that the attack on T-Mobile took place some time ago, even before the arrests of seven alleged Lapsus$ members, which UK law enforcement agencies reported at the end of March 2022.
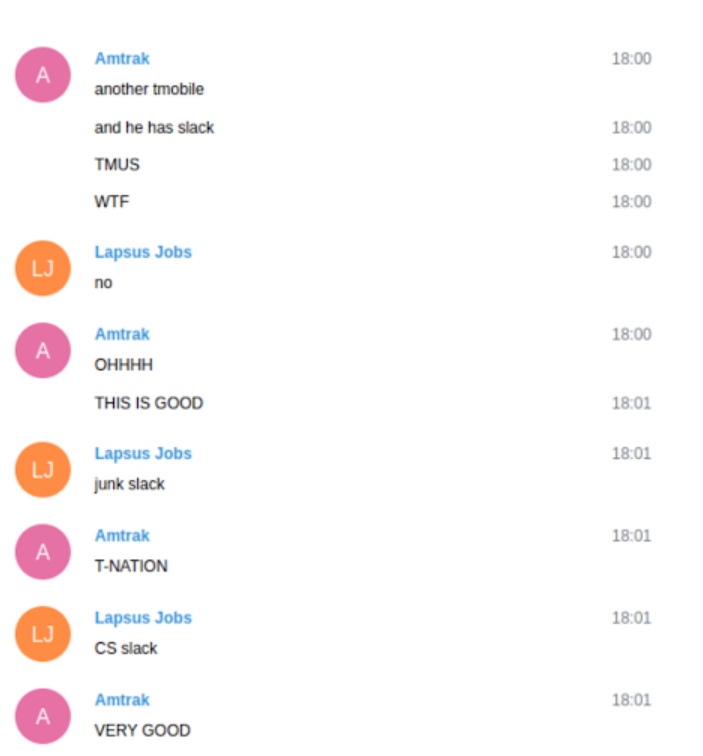
According to the chat logs, the VPN credentials that the group used for initial access were purchased and stored on the dark web, on sites such as Russian Market. The goal of the attackers was to compromise the accounts of T-Mobile employees, which ultimately allowed them to carry out SIM-swap attacks.
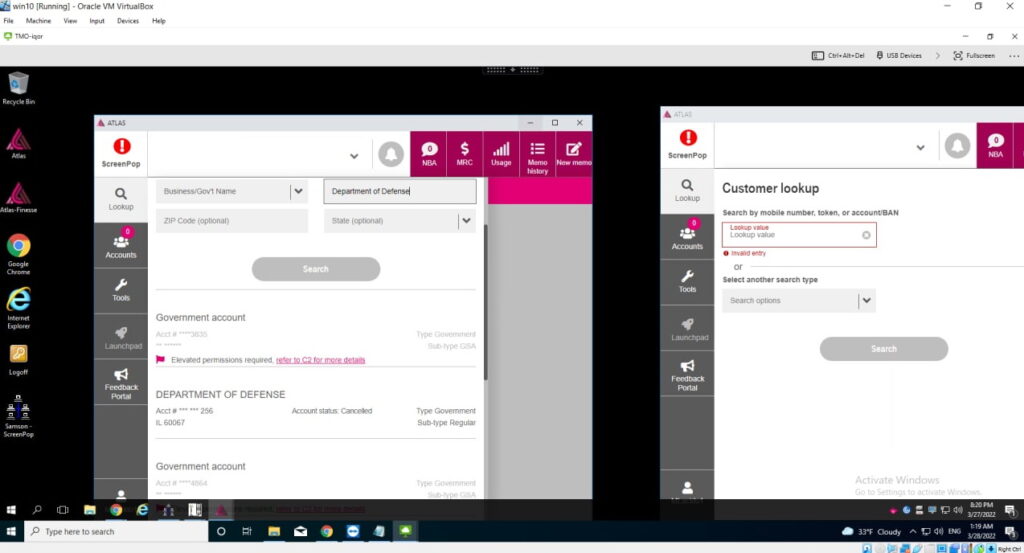
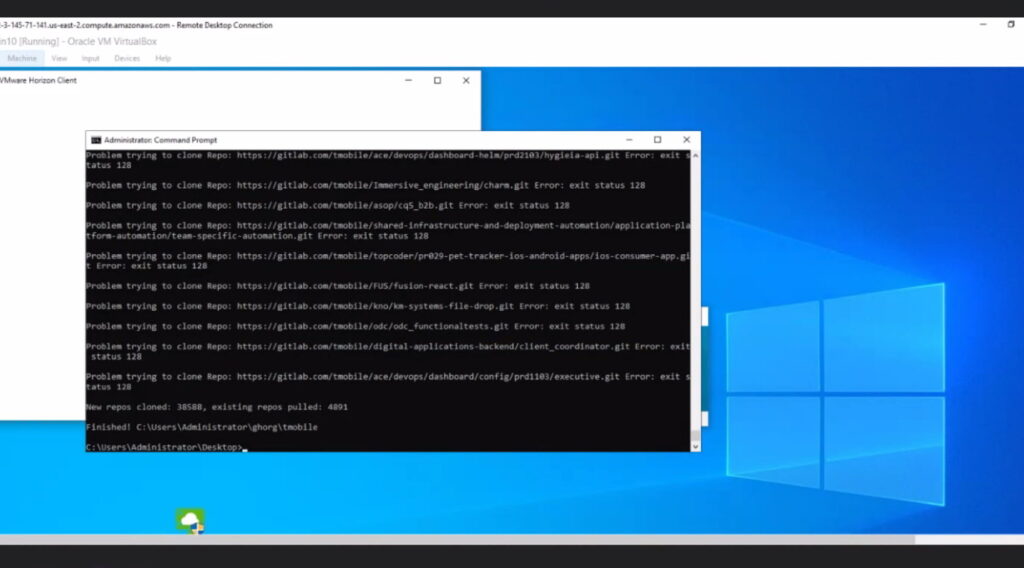
In addition to accessing an internal customer account management tool called Atlas, the hackers’ discussions suggest they gained access to Slack and Bitbucket accounts, using the latter to download 30,000 source code repositories.
At the same time, hackers were looking for T-Mobile accounts associated with the FBI and the US Department of Defence in Atlas (see screenshot below). To their disappointment, it turned out that additional verification procedures were needed to work with such accounts.
Interestingly, after failing to keep records of the FBI and other intelligence agencies, the leader of the group, a 17-year-old teenager from the UK, known by the nicknames White, WhiteDoxbin and Oklaqq, told other hackers to focus on stealing source codes and breaking the VPN connection with Atlas, which WhiteDoxbin considered “garbage”. The other members of the band were extremely unhappy with this decision.
After the publication of Krebs’s article, T-Mobile representatives confirmed the hack. The company stated: