PaperCut Vulnerability Allows RCE, Exploited in the Wild
PaperCut, a software solution used for print management, appears to be vulnerable to remote code execution (RCE). Another security violation that popped out along with the former allows extracting user…
New SLP Vulnerability Allows 2200x DDoS Amplification
A recently-discovered vulnerability in SLP, a legacy network protocol, can be used for disastrous increasing in DDoS-attack efficiency. As researchers say, the use of SMP vulnerability can push the amplification…
Supply Chain Attack Leads to 3CX Hack and Other Supply Chain Attacks
An investigation into a supply chain attack that hit 3CX last month found that the incident was caused by another supply chain compromise. First, the attackers targeted Trading Technologies, which…
Capita Hacked, Black Basta Gang Publishes Data
Capita, a London-based international business process outsourcing company, was hacked recently. Users noticed strange events in the company earlier this month, but the confirmation appeared only on April 20, 2023.…
Medusa Groups Claims That It “Merged” the Source Code of Bing and Cortana into the Network
Medusa extortionist group claims to have published internal materials stolen from Microsoft, including the source codes of Bing, Bing Maps and Cortana. Microsoft representatives have not yet commented on the…
Chinese Hackers Use Google Command & Control Capabilities in Attacks
Google experts have warned that the Chinese "government" hack group APT41 is abusing the red team's GC2 (Google Command and Control) tool. According to experts, GC2 was used in attacks…
5 Signs That You’ve Fallen Victim to a Scam
Internet fraud is becoming increasingly widespread and sophisticated. From simple phishing to romantic scammers, fraudsters are always looking for and inventing new ways to deceive unsuspecting victims. Let’s talk about…
Legion Hacker Tool Used to Steal Data from Poorly Protected Websites
Experts have discovered a Python-based Legion hacking tool that is sold via Telegram and is used as a way to hack into various online services for further exploitation. Let me…
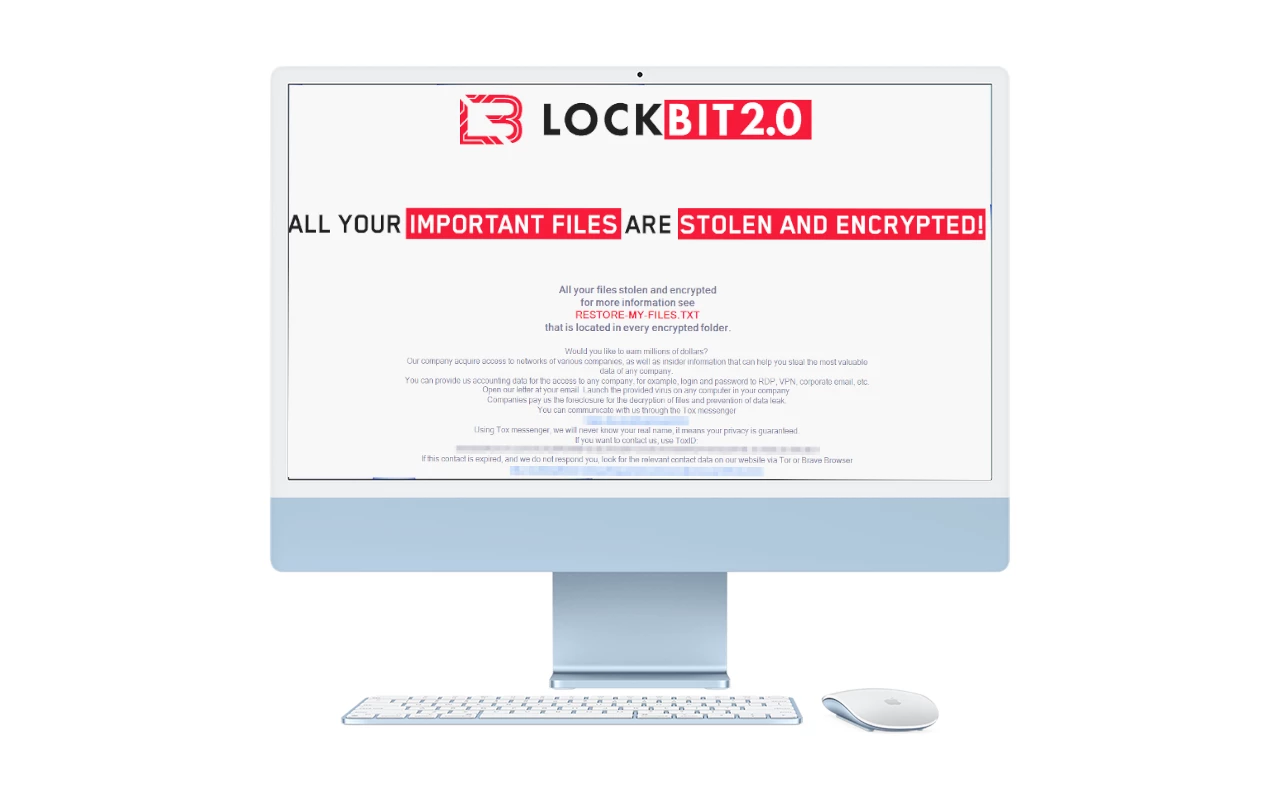
LockBit Releases World’s First macOS Ransomware
LockBit, an infamous ransomware gang that became a major threat actor over the last two years, released the variant of its ransomware for macOS. Previously, this system was considered safe…
Domino Backdoor is Lead by FIN7 and Conti Actors
A new Domino Backdoor popped out at the beginning of 2023. Since February, a new malware family coined Domino is used for attack on corporations, having Project Nemesis stealer as…
PDF Virus
Among numerous other files, PDFs are considered one of the most convenient to use for read-only documents. They prevent editing the content, yet retain the ability to carry interactive content.…
Microsoft Told How to Detect the Installation of the BlackLotus UEFI Bootkit
Microsoft has shared a guide to help organizations detect the installation of the BlackLotus UEFI bootkit that exploits the CVE-2022-21894 vulnerability. The company also explained how best to restore an…