Information security experts have discovered that the aCropalypse vulnerability, which allows restoring the original image edited on a Google Pixel device (using the Markup tool), is turning into a 0-day for Windows.
Let me remind you that we also wrote that YouTube Video Causes Pixel Smartphones to Reboot, and also that Information Security Specialists Discovered a 0-day Vulnerability in Windows Search.
Also information security specialists reported that the Google Pixel bug prevented users from calling 911.
It turned out that the aCropalypse bug also works for images cropped using the Windows Snipping Tool, which means that previously deleted content can also be restored for these images.
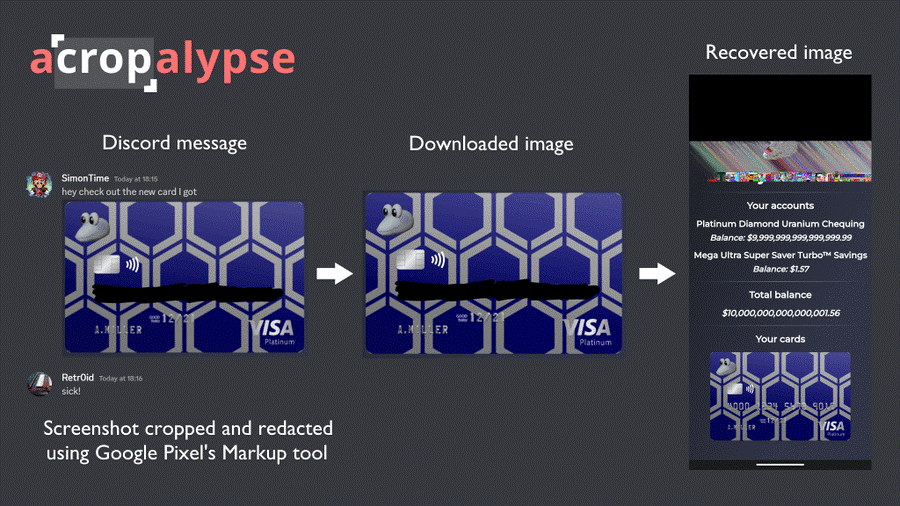
Restoring a shaded bank card number
The aCropalypse vulnerability (CVE-2023-21036) was discovered by cybersecurity experts Simon Aarons and David Buchanan. It allows restoring any images modified using the built-in Markup screenshot editor, which appeared on Pixel smartphones in 2018 with the release of Android 9.0 Pie.
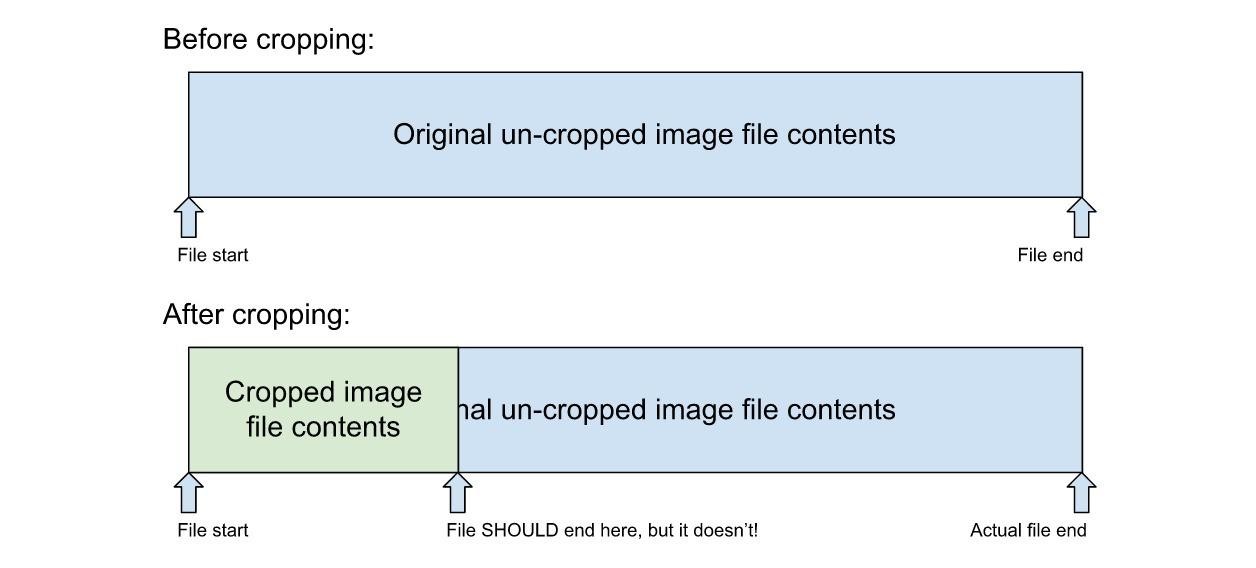
In the case of the Pixel, the problem lies in how the image file is opened for editing: the cropped data still remains in the new saved image, allowing about 80% of the original image to be restored.
The researchers warned that aCropalypse could expose users’ sensitive information if they had once edited an image with Markup and then shared the file with other people or even posted it online.
Because some platforms don’t compress user-uploaded media, the sensitive data contained in the images may have been left untouched and stored somewhere online all these years. In this light, the example given by Aarons with the blurred bank card number shown above is very revealing.
It looks like the aCropalypse issue has gotten a lot worse now, as programmer Chris Blume has discovered that the vulnerability also affects the Windows Snipping Tool.
When you open a file in the Snipping Tool and overwrite the existing file, the same thing happens as in Markup: instead of truncating the unused data, the tool puts the unused data at the end of the file, which eventually allows to partially restore it.
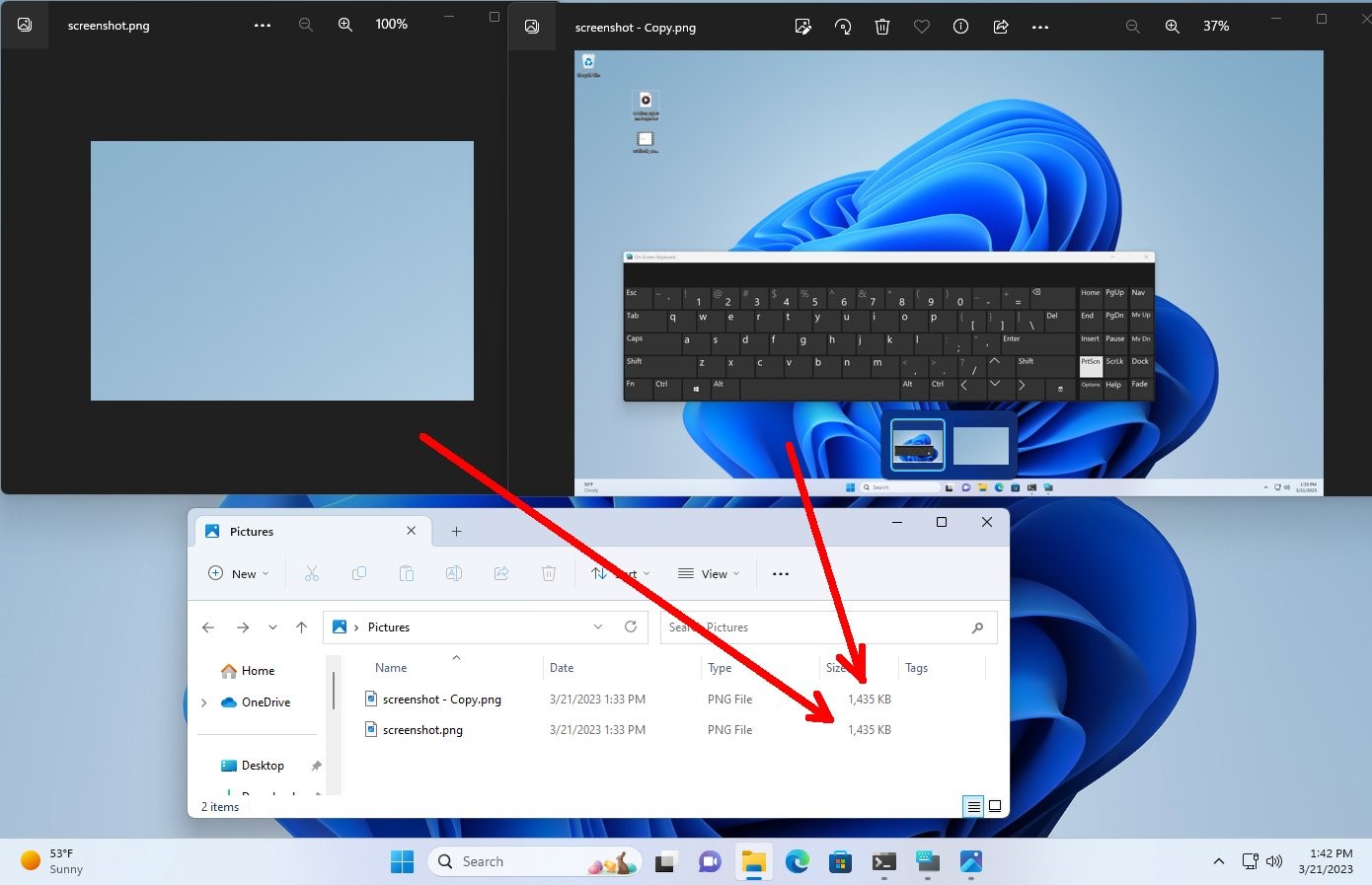
Bleeping Computer and well-known information security expert Will Dormann confirm that the vulnerability actually works in Windows 10 and 11. So, Dormann suggested a simple test: copy any image (to have a backup), then open it with the Snipping Tool ” and crop it to a much smaller size. Save the file and compare the sizes of the cropped and original files. As you can see in the screenshot below, the file sizes are the same.
Bleeping Computer journalists went even further. They note that the PNG file specification requires that a PNG image file always ends with an “IEND” data fragment, with any data added after it being ignored by image editors and viewers. And unused data remains in the file after IEND.
After all the manipulations described above, the journalists decided to “see” this data.
Since the acropalypse.app online application does not work with Windows files, David Buchanan shared with the publication a Python script that can be used to restore Windows files. The successful result of this script, which the expert does not intend to make public yet, can be seen below.

It is noted that not all PNG files are affected by this problem, and not all originals for all files can be completely restored.
In addition, opening a PNG file in a graphics editor (such as Photoshop) and saving it as another file will delete unused data at the end and cannot be recovered.
It is worth saying that the Snipping Tool works exactly the same with JPG files, saving the “cropped” data when overwritten. However, Buchanan says that his exploit does not yet work with JPGs, although recovery of such images is most likely possible.
Microsoft representatives told the media that they are already aware of this problem. The company is currently investigating the matter, and it promises it will “take steps to protect customers if necessary.”




