Researchers have identified a new state-backed hacker group in North Korea. The group in question is the North Korean hacker group APT43, which has targeted government organizations in Europe, the United States, South Korea, and Japan for the past five years.
What is APT43?
APT43 (sometimes called “Kimsuky”) is a North Korean group that became active in 2018. It is considered one of the most closely tied to the personal and geopolitical goals of dictator Kim Jong-un and his ruling elite. The group’s primary focus is strategic data collection. It mainly concerns foreign policy and issues related to his nuclear weapons program. According to the researchers’ report, APT43 targets educational, political, and business services in Europe, the United States, South Korea, and Japan. Moreover, they are particularly interested in research centers dealing with geopolitical and atomic policy. However, between October 2020 and October 2021, there have been instances in which the healthcare industry and pharmaceutical companies have been attacked.
Attack methods
Unlike their other counterparts, APT43 does not tend to rely on sophisticated technical techniques, zero-days, and other advanced intrusion techniques. Instead, they use old, time-tested methods based on phishing and aggressive social engineering to get closer to their targets. For example, they may pose as journalists or researchers. More often, however, they send targeted emails that contain links to websites pretending to be legitimate. These websites have fake login pages where the victim enters their credentials, and they are sent to the attackers. By obtaining these credentials, APT43 can log into the victim’s account to independently gather intelligence of interest. In addition, the victim’s contact list is exciting, as it facilitates spear phishing attacks.
APT43 Uses Dirty Crypto Money
As stated above, the ideology of APT43 is the interests of the North Korean regime. However, the government does not fund them, forcing them to hack and steal to fulfill their “main” mission. Thus, cybercriminals steal cryptocurrency wallets from their victims and then use hash rental and cloud mining services to launder the creation of new pure cryptocurrency. These funds are then used to purchase additional infrastructure and tools to support hacking operations.
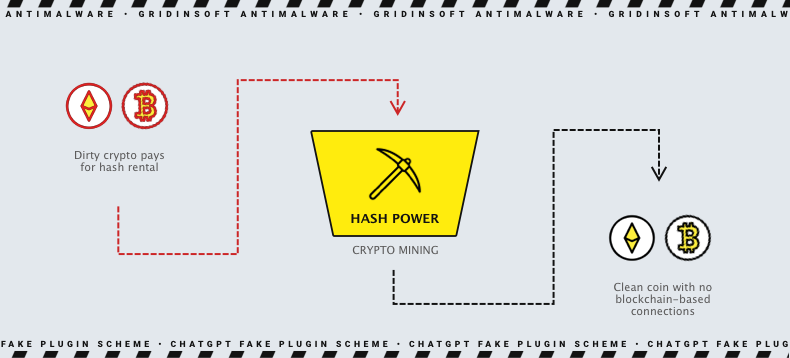
North Korean hackery
Hacking activities in North Korea go hand in hand with government agencies. For example, APT43’s activities allegedly align with the Reconnaissance General Bureau, North Korea’s foreign intelligence agency. Moreover, North Korea has been accused of cyber attacks against various targets, including financial institutions and cryptocurrency exchanges. One of the most notorious groups linked to North Korea is the Lazarus Group. The group has been blamed for many significant cyberattacks, including the WannaCry attack in May 2017. It was one of the most significant cyberattacks in history, infecting the computers of more than 200,000 organizations in 150 countries. Although North Korean authorities have denied any connection to the WannaCry attack, many experts believe North Korean hackers were behind the attack.
Is it dangerous?
Although APT43 does not exploit critical unknown vulnerabilities in systems, the group collaborates with several state-supported hacker groups in North Korea. In addition, although APT43 uses publicly available tools such as “gh0st RAT,” “QuasarRAT,” and “Amadey,” it has its own set of custom malware that no one else uses. These include the “Pencildown,” “Pendown,” “Venombite,” and “Egghatch” downloaders, the “Logcabin” and “Lateop” (“BabyShark”) tools, and the “Hangman” backdoor. In addition, researchers believe APT43 will support spying efforts through cybercrime in the regime’s cyber apparatus.




