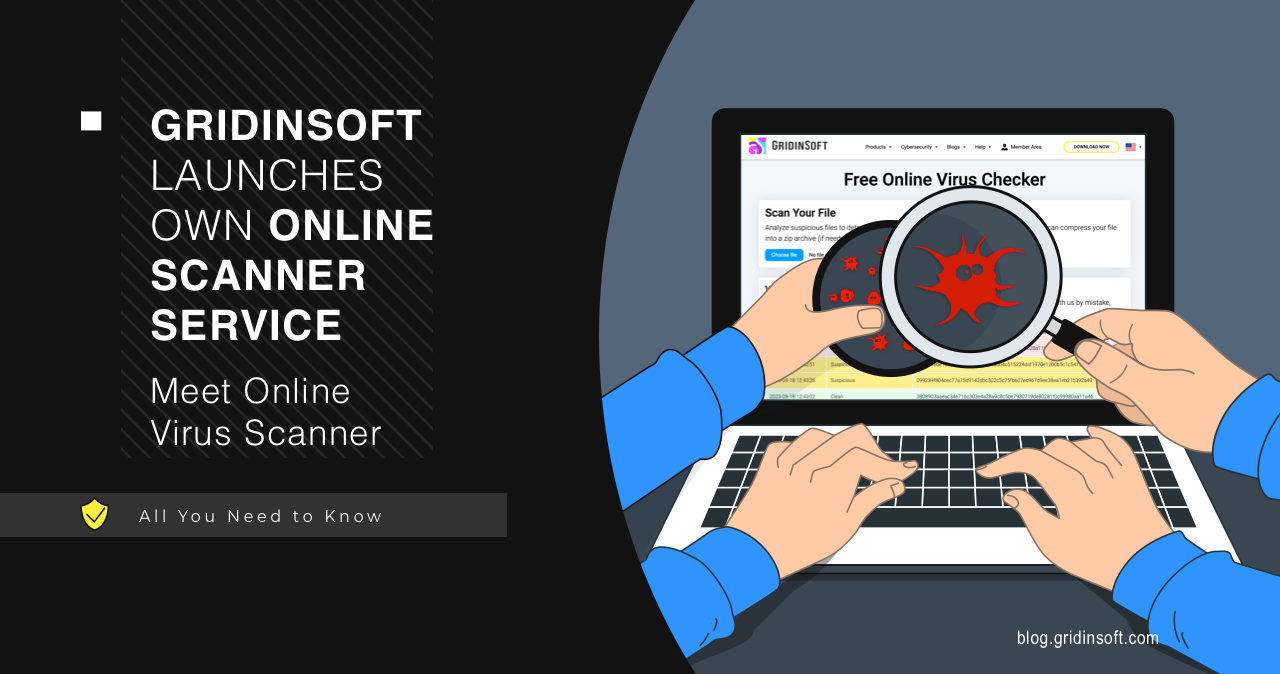
GridinSoft Launches Own Online Scanner Service – Meet Online Virus Scanner
As a part of the GridinSoft team, I am proud to announce the public release of our own online virus scanner service! Now, you can scan the file and see…
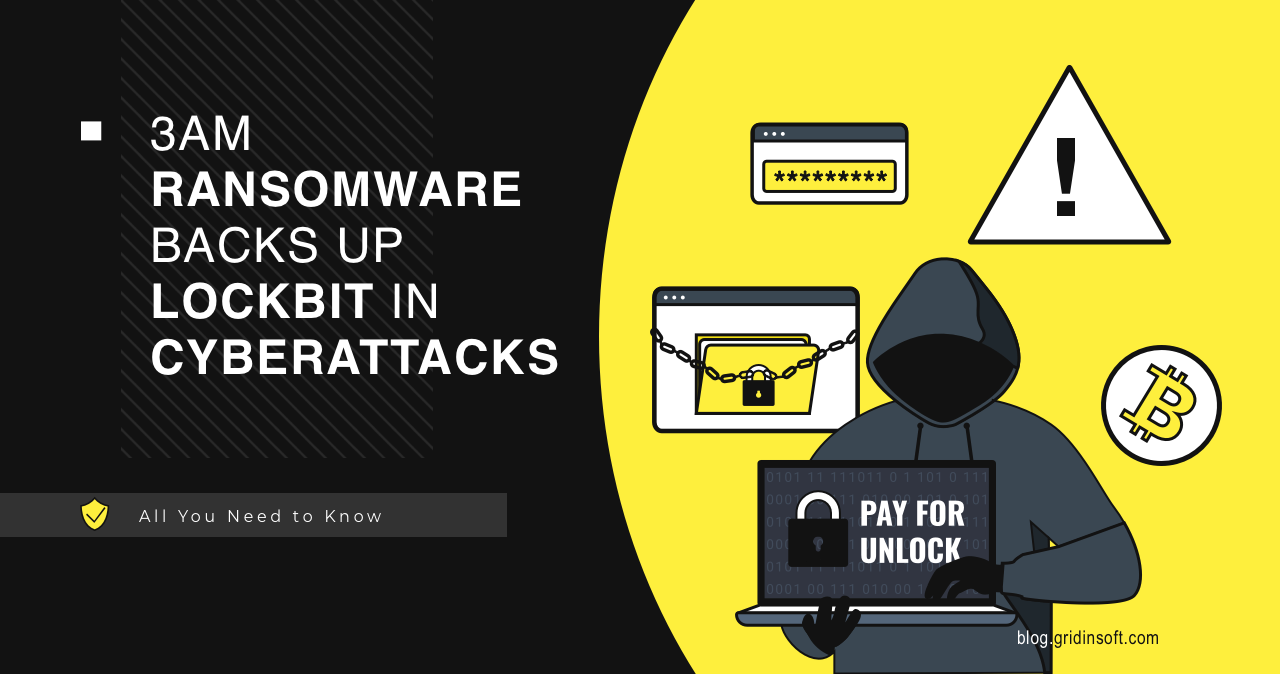
3AM Ransomware Backs Up LockBit In Cyberattacks
Cybersecurity researchers have discovered a new family of ransomware called 3AM. Attackers attempted to use it as an alternative attack method during the failed LockBit deployment. 3AM Ransomware - The…
What Is Identity Theft & How to Protect Against It
Identity theft is a significant issue affecting millions yearly, whether through stolen credit card information or fraudulent accounts. It's a lucrative business for criminals, who can steal billions of dollars…
Google Fixes Critical Vulnerability in Chrome, Exploited in the Wild
Google released an urgent security update for its Chrome browser. The patch contains the fix for CVE-2023-4863, a heap buffer overflow vulnerability that can simply be exploited. Actually, Google states…
Spyware in Fake Telegram Apps Infected Over 10 million Users
It is important to exercise caution when using messenger mods. There have been reports of spyware disguised as modified versions of Telegram on the Google Play Store. This malware designed…
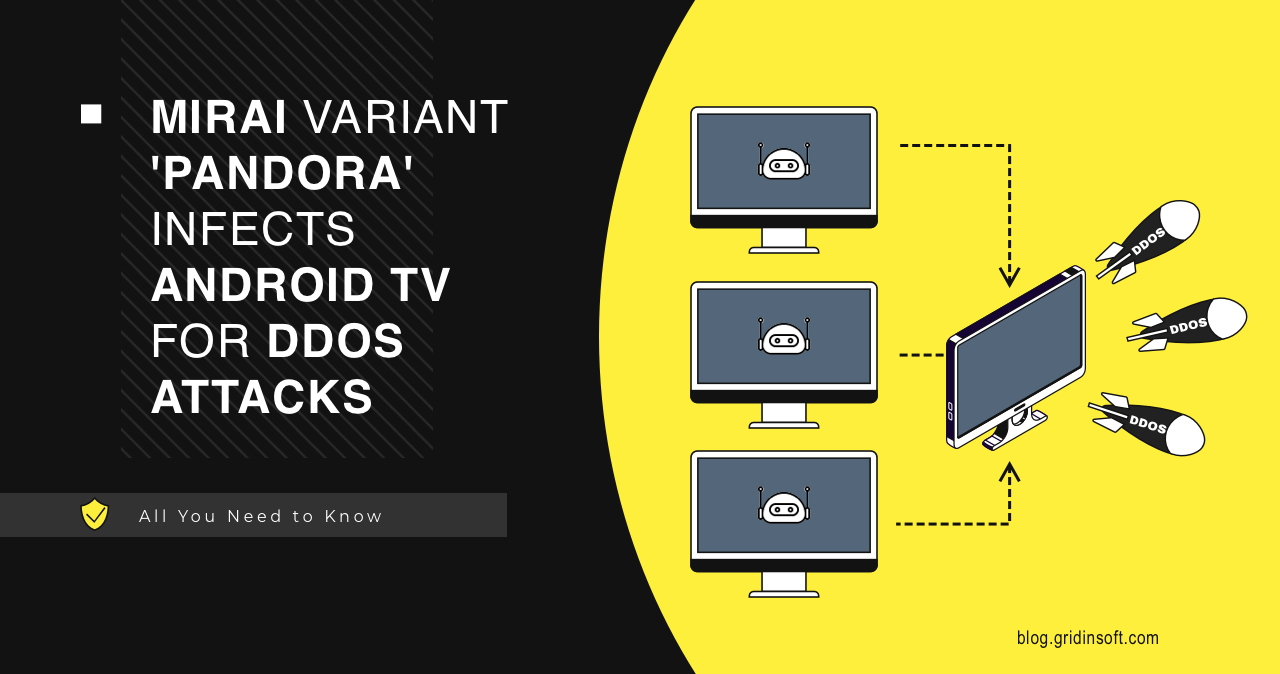
Mirai variant “Pandora” infects Android TV for DDoS attacks.
A new variant of the Mirai malware botnet has been detected, infecting low-cost Android TV set-top boxes. They are extensively used for media streaming by millions of people. The present…
W3LL Targets Microsoft 365 Accounts with Sophisticated Phishing Kit
In the ever-evolving landscape of cyber threats, crooks continually find new and inventive ways to exploit vulnerabilities and target valuable assets. One such threat that has recently garnered significant attention…
NCA and DoJ Introduce New Sanctions Against Conti/Trickbot Hackers
On September 7, 2023, NCA released a statement regarding the new complex pack of sanctions against Russian Conti cybercrime group members. Accused of participating in extortions worth $800 million, gang…
Can Zero-Day Attacks Be Prevented With Patches?
In recent years, zero-day exploits and attacks have become prominent emerging threats. These attacks take advantage of unknown vulnerabilities within software, which makes them almost impossible to detect and prevent.…
QakBot Botnet Dismantled, But Can It Return?
On Tuesday, the US authorities announced that as a result of the international law enforcement operation "Duck Hunt," the infamous Qakbot malware platform, which is linked to Russia, was destroyed.…
Chae$4 Malware Released, Targets Banking & Logistic Orgs
Cybersecurity experts have discovered a new variant of Chaes malware called "Chae$4". This malware targets the banking and logistics industries and significant content management platforms. New Chae$4 Malware Targets Banking…
7 Million Freecycle Users Exposed In a Massive Data Breach
Freecycle has alerted its users that sensitive information of over 7 million of them may have been compromised in a recent data breach. The organization suspects that over seven million…