Search engine optimization (SEO) is a process of optimization and upgrading of websites to improve the ranking of search engine results pages and to attract traffic. Among other things, SEO helps to create a reliable reputation. But there is also a black SEO, also known as black hat SEO. The article below will tell you what it is, why some users use it and how to fight it.
What Is Black Hat SEO?
Black Hat SEO is any action that aims to improve the site’s reputation and rating in the search engines in an illegal way. This activity uses methods that violate the maintenance rules of search engines such as Bing or Google, pushing the site higher in search results.
Since the Internet’s development, many marketers have tried to attract traffic and improve their reputation by using black SEO. But over the years, search engines have improved the quality of their service and have begun to take appropriate measures against such fraudsters. Unfortunately, penalties for unethical actions have prompted intruders to new methods. Now they’re using these old-fashioned tricks, but under the guise of reputable companies, so users don’t know they’re being robbed.
Why Do People Use Black Hat SEO?
Back SEO works as follows: intruders find the site, which has already taken some positions in the network, gained a good reputation, and recruited customers who trust him and seem quite reliable. Then they take over this site and clone it, using domain spoofing. Then they use the tactic of black SEO on their copy. Despite the mentioned improvements in search engines, they still fall into some methods of black SEO, but only temporarily – for a couple of days. After that, the search engine sees and banishes the attacker, but it may be too late. For prominent business executives, black SEO scams can cost them reputation, loss of traffic, and reduced visitors. Worst of all, before these attacks are detected, some users will already be victims of these intruders.
Reduce the Chances of Customers Visit a Cloned Website
Black SEO has devastating effects on companies and their websites. To warn yourself against this and thus reduce the risk of falling for the ruse of intruders, you need to take the following measures:
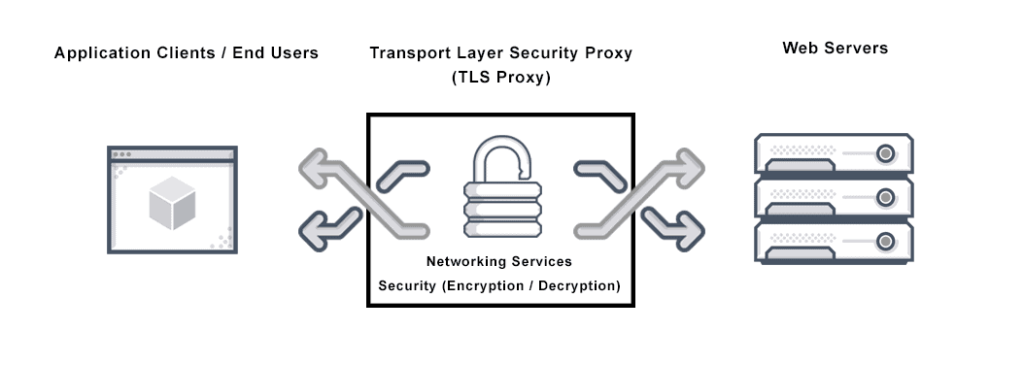
1. Install a TLS Certificate
A Transport Layer Security, or TLS, certificate is a digital protocol that secures websites and establishes an encrypted connection between the website and the user’s browser. The protocol authenticates a website’s identity and allows users to see the HTTPS prefix and certificate in their domain URL. This gives users confidence that their data will be kept private and secure.
2. Secure Your Source Code
Developers need to add security measures to a website. One option is to disable the copy-paste function so attackers can’t easily access the website’s source code. Otherwise, if the source code is successfully stolen, the attacker gets access to the site, can clone it and nourish the owner of any reputation.
3. Remain Proactive
Companies need security teams to monitor their domain and website traffic for any suspicious activity. By implementing data handling procedures and risk management strategies, companies can better identify and defend against threats.
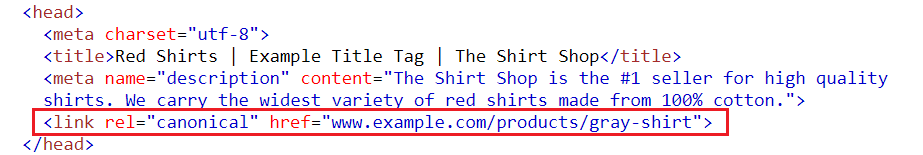
4. Use the rel-canonical Tag.
Search engines can easily detect duplicate pages through slight alterations in URLs. For example, adding a rel-canonical tag to a site tells the engine which page is the original, making it harder for fraudsters to spoof the website.
5. Study Your Website Analytics
Scammers can clone websites to steal easy wins. While they may not take the time to change all internal links, visitors can still navigate to the original domain. Additionally, you can check your website’s analytics to see if any incoming traffic comes from domain names similar to your original site.
Building many internal links on your website has the added benefit of making it easier to find duplicate sites. This is because duplicate sites are more likely to be discovered if they have a lot of external links pointing to them.
Restoring Your Reputation After a Spoof
The advice given above may warn you against an alleged attack. But what if the fraudsters did manage to harm your site and were able to steal some of your data? Below we will look at a few steps to restore your reputation and recreate your trademark.
• Address the Situation Publicly
Don’t try to hide your situation; report it publicly. Report that you are aware of the damage done to your reputation and diligently dealing with the problem. You can also post whether to record a video on YouTube or Instagram in which you apologize for the inconvenience caused to your users. Finally, publicly admit some of the blame for the security negligence and make it clear to your users that you will do everything in your power.
• Remove Fake Reviews
People may add fake online reviews to increase the perceived legitimacy of their fake websites. As a result, asking search engines like Google to remove these reviews is beneficial. Additionally, asking third-party review platforms like Trustpilot to remove these reviews can be helpful.
• Communicate Openly About Your Policies
Let people know when they need to expect two-factor authentication. For example, they may think they’re on a phishing site if they don’t receive a request on their phone or email. Additionally, let people know if you have any other policies related to communication with customers.
Black hat SEO is sneaking a site past search engines to trick users. As a result, it can steal money from users and businesses, making it a problem everyone should watch out for.




