DNS Spoofing: Key Facts, Meaning
What is DNS Spoofing? DNS (Domain name server) spoofing or DNS cache…
Some Tips About Data Loss Prevention (DLP) For Users
Data Loss Prevention (DLP) is a method of detecting data loss and…
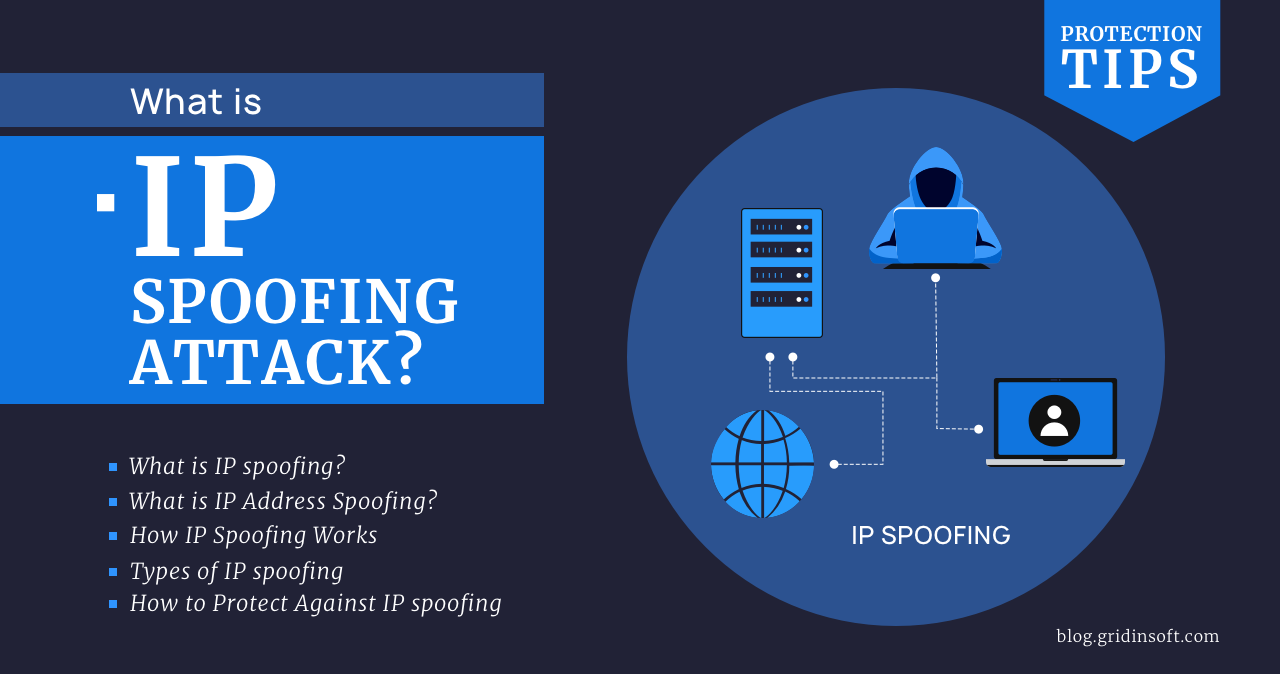
IP Spoofing Attack: Explanation & Protection
Among other types of attack, IP spoofing stands out for its simple…
10 Ways To Recognize and Avoid Phishing Scams
Phishing attacks are a scam that aims to steal confidential data through…
15 Reasons to Choose GridinSoft Anti-Malware
Choosing the anti-malware solution these days is a tough decision. Over a…
Working Tips and Recommendation: How to Use OSINT
OSINT, or open-source intelligence, is a kind of reconnaissance operation that became…
Top Threats That Anti-Malware Catches
As technology advances, cyber-attacks become more prevalent, with attackers constantly developing new…
10 Signs That Your Computer Is Infected With Spyware
What Is Spyware? It is a malicious program that secretly gets installed…
TOP Facts About Adware Attacks To Be Reminded Today
To begin with, each of you has faced this challenge. Namely, the…
Antivirus Is Important! Advantages Of Using
If you are one of those people who are contemplating whether to…
What is SSL Certificate?
Many of us have probably noticed various security-related markings around browsers' address…
LockBit attacks the Canadian defensive co. Top Aces inc
Canadian defense contractor Top Aces Inc became the victim of a ransomware…