11 Types of Spoofing Attacks
Spoofing is a kind of cybercrime in which attackers impersonate a trusted…
Attackers Exploit MSDT Follina Bug to Drop RAT
Security specialists caution users about the exploitation of the recently disclosed Follina…
New Cuba Ransomware Variant Involves Double-Extortion Scheme
What's new in April Variant of Cuba Ransomware The Cuba ransomware family…
Warning Signs Of DDoS Attack: Symptoms
DDoS attacks can sometimes have devastating effects on various internet users. This…
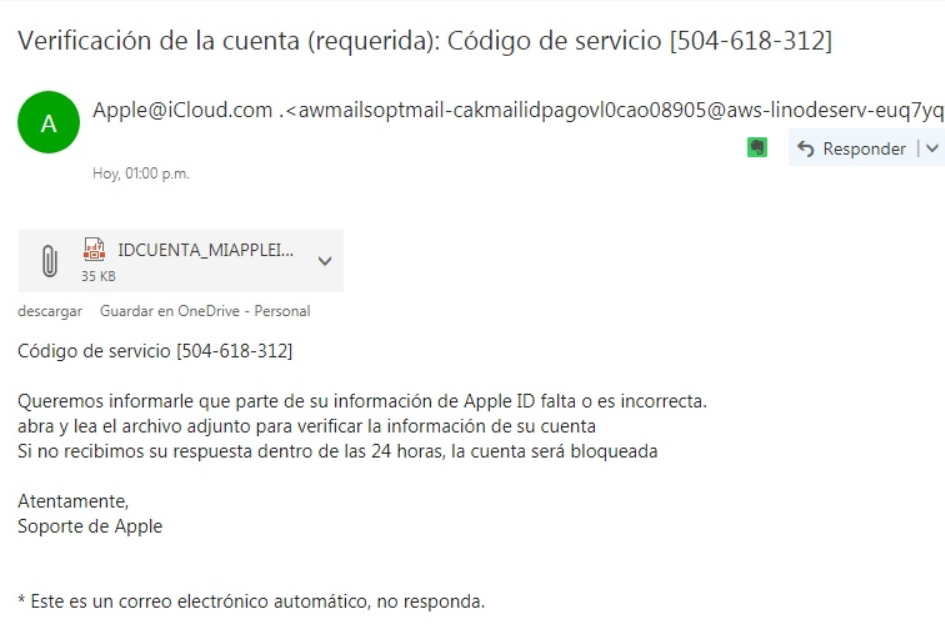
Extension spoofing strikes Spanish-speaking countries
An old-good form of malware disguisment sparked recently in several Spanish-speaking countries…
Types of SQL Injection: Attack Examples
As we wrote in one of the articles, SQL is a structured…
Malware VS Ransomware: What’s the Difference?
To deal with any problem successfully you should first have a clear…
TOP 7 Types of Password Attacks
What is a Password Attack? In the beginning, you probably already understood…
Critical Vulnerability in UNISOC Devices Patched
UNISOC-chip Android Phones are Vulnerable to Remote Modem-Targeting Attacks In May 2022,…
Clipminer – a Million Dollar Clipboard Hijacking Coinminer
Clipminer Malware A bizarrely efficient botnet cryptocurrency miner has been revealed by…
CMD-Based Ransomware YourCyanide With Info-Stealing Functions
New Threat: YourCyanide Ransomware CMD-based ransomware YourCyanide, currently under development, has been…
What is Spear Phishing? Definition with Examples
Spear phishing is a type of phishing attack that targets specific individuals…