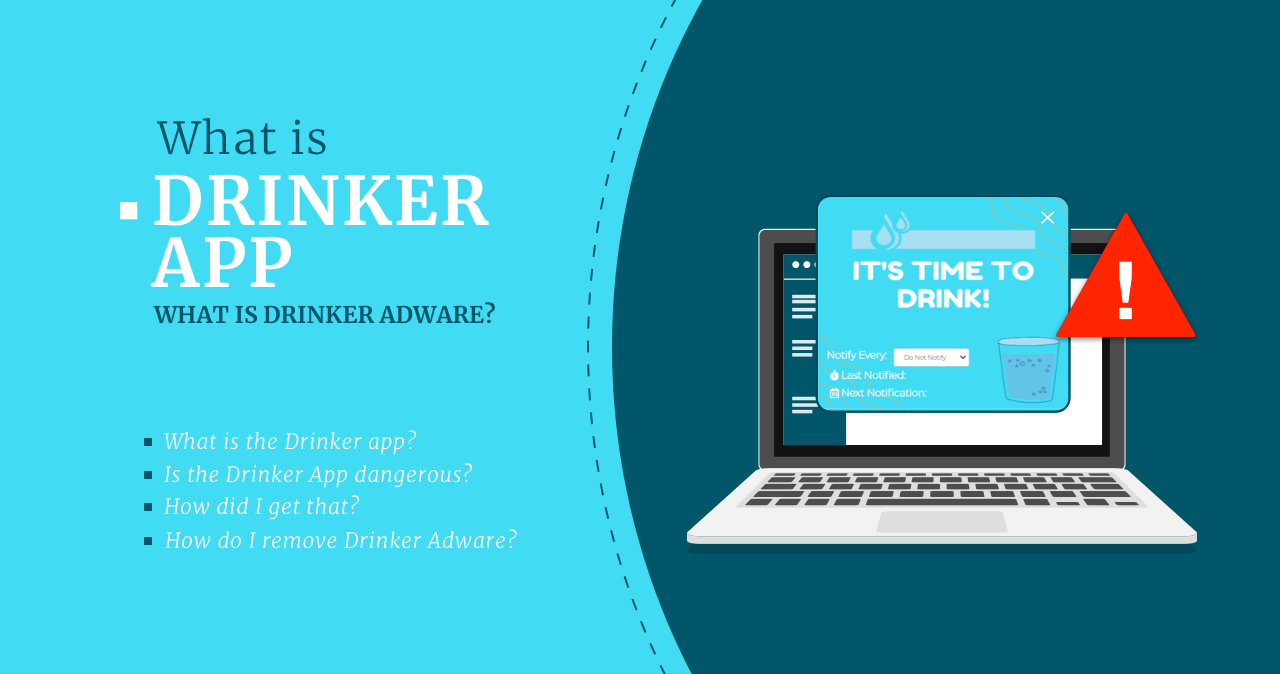
Drinker App – what is Drinker Adware?
The Drinker app is another example of a malicious program that disguises…
10 Reasons to Choose GridinSoft Trojan Killer
We used to think of anti-malware software as a program that features…
Healthy App (HealthySoftware) – What is Healthy?
Healthy App seems to be the companion of the other unwanted app…
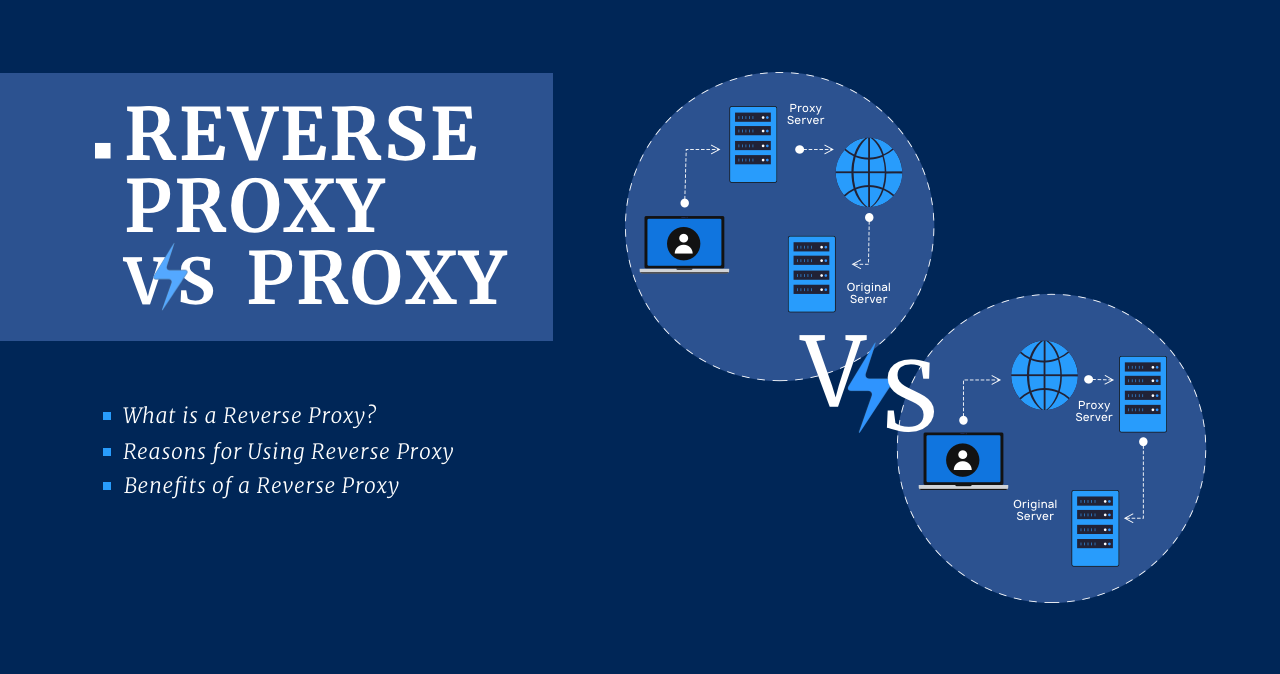
Reverse Proxy vs Proxy
What is a Reverse Proxy? A reverse proxy is the same server…
Strength Adware – What Is Strength App?
Strength Adware, a new advertising malware, began appearing on users’ devices. It…
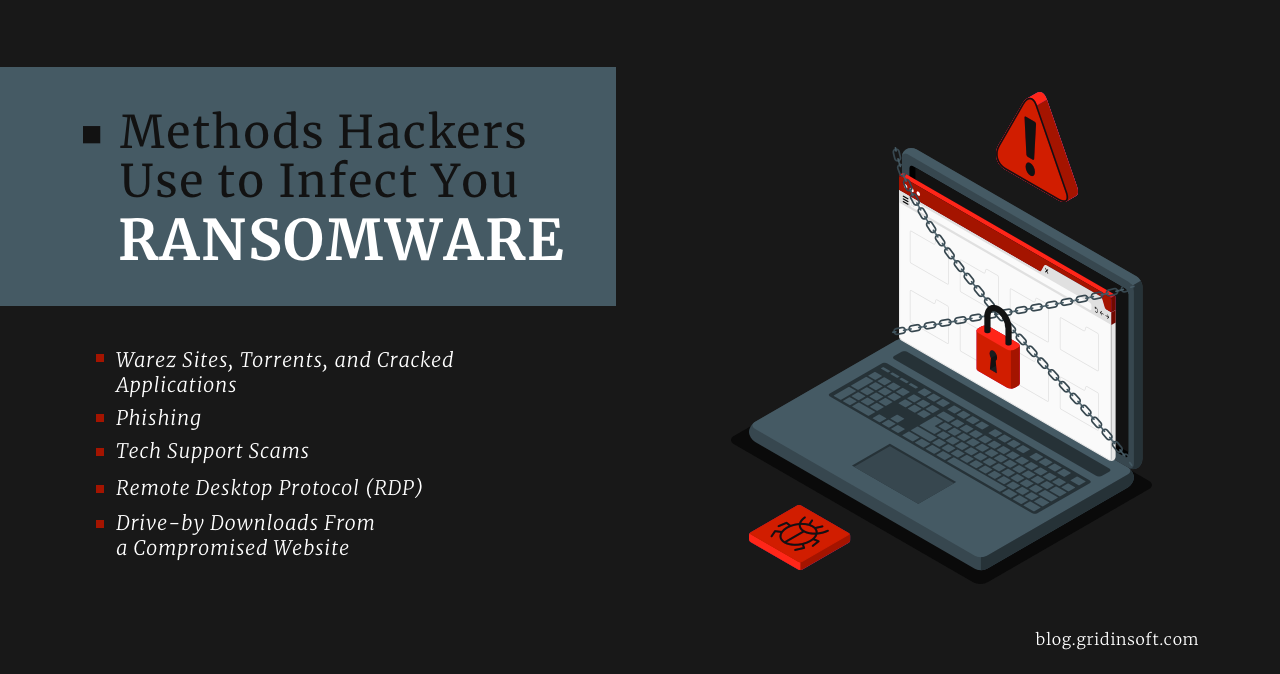
Methods Hackers Use to Infect You Ransomware
Ransomware hits the headlines almost daily. And most incidents target large corporations…
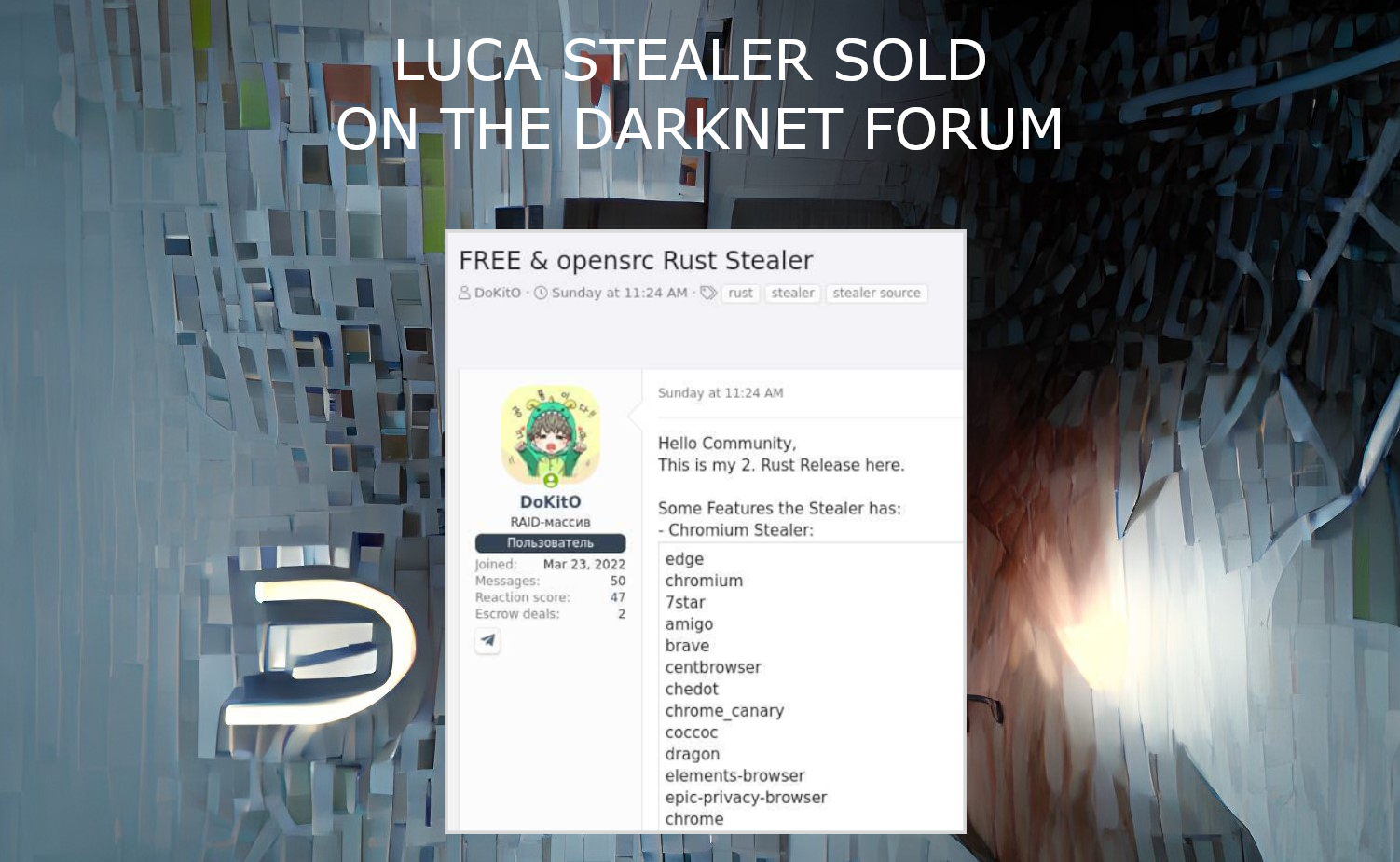
Luca Stealer Source Code Published In The Darknet
Luca Stealer, an omni-purpose stealing malware programmed on Rust, was published on…
Can Someone Track My Device When Location Settings Off?
Any smartphone already has built-in location tracking services. At the beginning location…
How To Know If Your Phone is Hacked?
If your phone stopped working correctly and started showing obvious performance errors,…
Candiru Malware Uses 0-day Vulnerability In Chrome
Following Microsoft, Google and Citizen Lab, another revelation came from Avast researchers.…
Spam Phone Calls Revenge: Prevent Spam Risk Phone Calls
Statistics show that an average of 1,900 spam calls are made every…
“Your Account Has Been Locked”: Top 5 Signs of a Phishing Scam
The topic of our article will be how to understand that you…