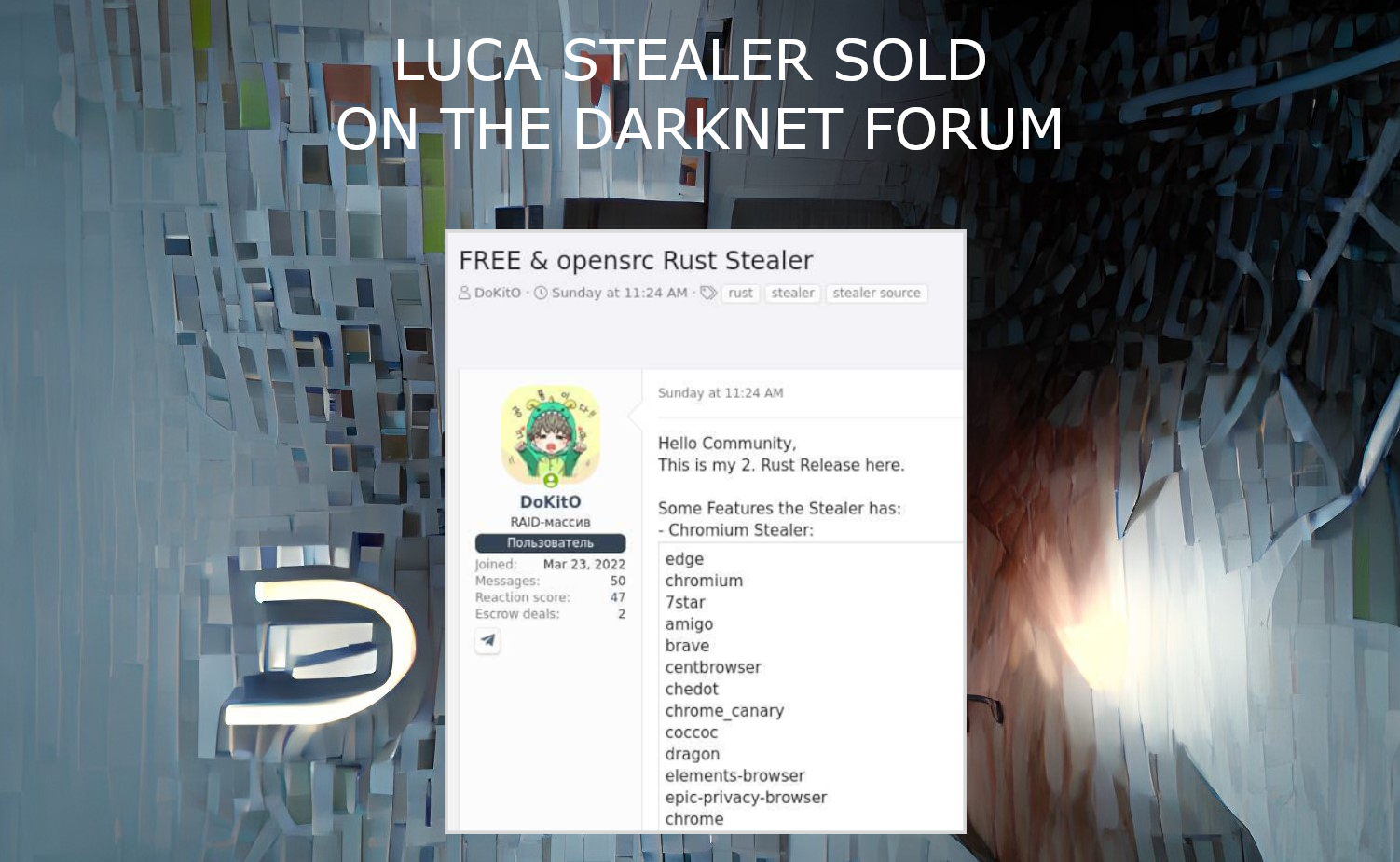
Luca Stealer, an omni-purpose stealing malware programmed on Rust, was published on the Darknet forum in recent days. The source code of a well-done stealing tool is now available for everyone. This stealer generally aims at web browsers, particularly the plugins and data that belongs to cryptocurrency wallets and online banking.
Luca Stealer functionality
As analysts from Cyble state in their report, the set of functions Luca malware offers is similar to the ones available in other stealers. It can successfully break into all Chromium-based web browsers, and deliver different types of information to the hacker. In particular, it aims for cookie files, Discord login tokens, accounts on game distribution platforms, credit card info and cryptocurrency wallets. The last two categories of information are obtained through digging the extensions installed in the browser. Malware checks them by the list of installed plugins and, once getting a match, steals the data these plugins store locally. This technique is different from what is usually applied by stealers.
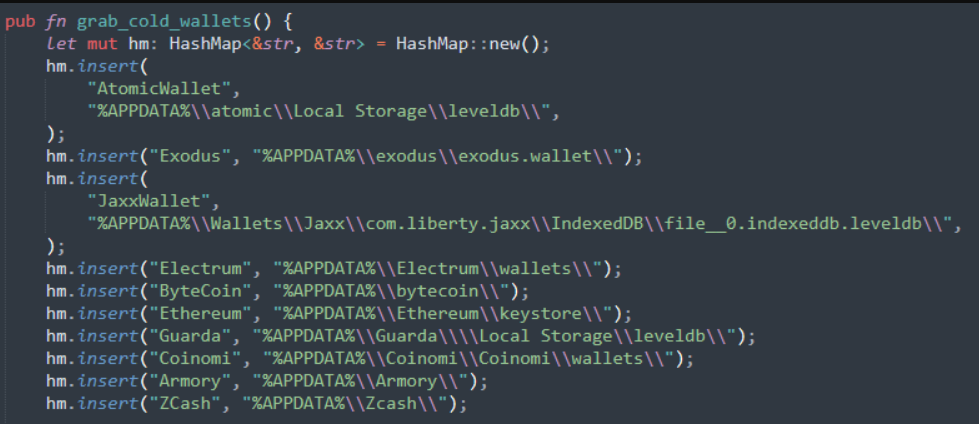
Besides the categories of data I have mentioned before, Luca Stealer also grabs the information about the attacked system. Using the specific calls, it receives the system memory amount, swap file size, number of CPU cores and so on. After finishing the data collection, Luca packs it into the zip archive and sends it via Discord webhooks, or through bots in Telegram. The choice depends on the size of the resulting file.
There is a single significant difference between Luca and other stealers. It is not able to hijack the cryptocurrency transactions through editing the data copied to clipboard. Still, that function is highly notable for antivirus software. Reading the clipboard contents without the user’s command is suspicious, so the absence of this function makes this malware harder to detect. Moreover, stealing the entire wallet instead of the single transaction may be much more profitable, and the former has more chances to remain undetected.
Luca stealer spreading
It is not clear how exactly this stealer spread. Luca is quite stealthy, as only each fifth antimalware vendor among present on VirusTotal actually detects it. It is likely caused by the programming language of this malware – Rust. It has already appeared in ALPHV/BlackCat ransomware, and showed up as the great way to mask the malware. Additionally, that makes it easier for the crooks to make their malware cross-platform. Usual ways of stealer distribution – through the malicious spamming on different platforms and phishing – will fit Luca as well. But which one will the cybercriminals actually opt for – only God knows.
A few days ago an individual on XSS leaked [sic](shared?) the source code to a Rust-based data theft malware.
We have added it to the vx-underground Malware Source Code collection on GitHub:
/Leaks/Win32/Win32.Rust.LucaStealerhttps://t.co/5RHeEYWYth
— vx-underground (@vxunderground) July 26, 2022
Is there a reason to be concerned?
There is always a reason to be concerned, if you have anything valuable in a digital form. Cryptocurrencies prices are going up, and so do the hackers’ interest to someones’ savings in crypto. The full-scale pandemic of cryptostealers is already gone, but that makes each new stealer with the ability to dig into crypto wallets even more hazardous. Such programs now cannot just rely on an increased demand on the black market. They should offer something ridiculous – or will definitely fail. There are already around 25 cases of Luca Stealer usage in the wild. Not pretty impressive – but still a lot for a newbie that appeared several days ago.
It is recommended to keep all login information in a separate application, rather than in the web browser. But it will be much better to avoid the infection at all by following the rules of cybersecurity. It is better to make the situation less possible, but never deny the probability of such an unpleasant case.