One Year of Russian-Ukrainian War in Cybersecurity
February 24, 2022, will be a turning point in history. It was…
Five Easy Smartphone Security Tips to Keep It Safe From Hackers
These days, the smartphone is more than just a means of communication.…
How DDoS Can Badly Hurt Your Business
Everyone at least once faced the fact that they cannot go to…
TrickBot Members Sanctioned By U.S. and UK
US and UK law enforcements imposed sanctions against 7 members of a…
IceBreaker Backdoor Emerged, Exploiting New Phishing Way
A new player has appeared in cyberspace, with surprisingly new methods. A…
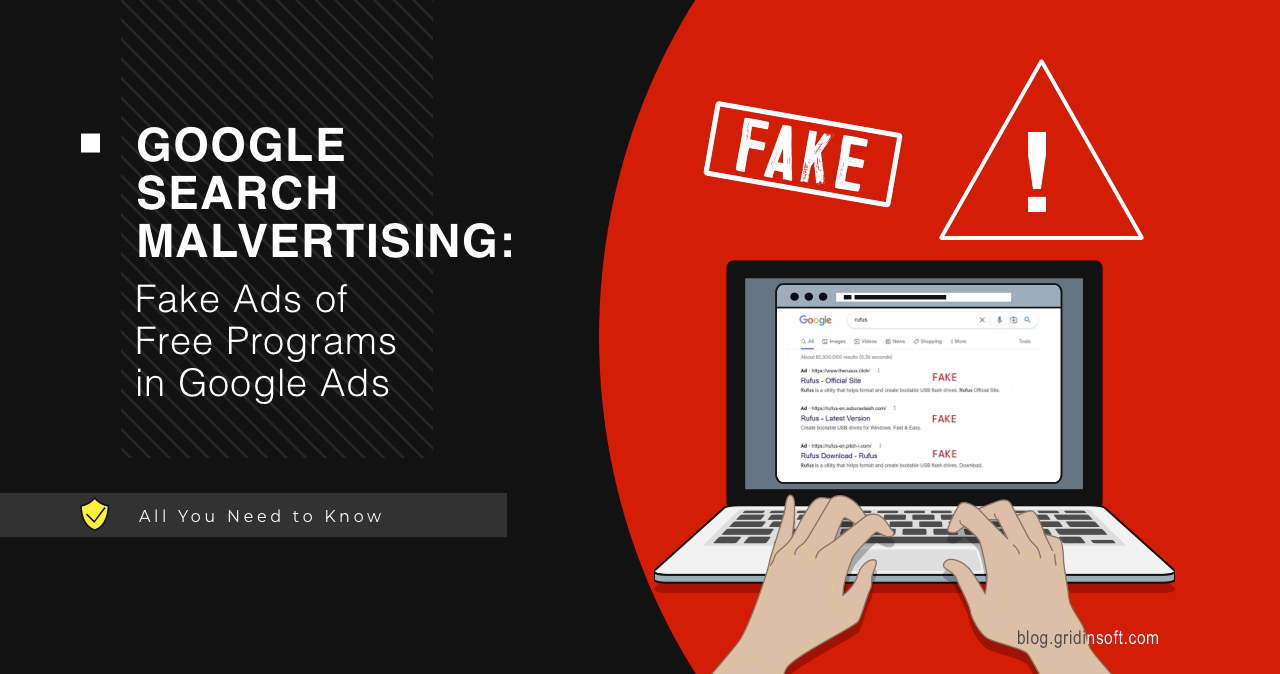
Google Search Malvertising: Fake Ads of Free Programs in Google Ads
Google Search malvertising is an unpleasant phenomenon of malicious advertisements in search…
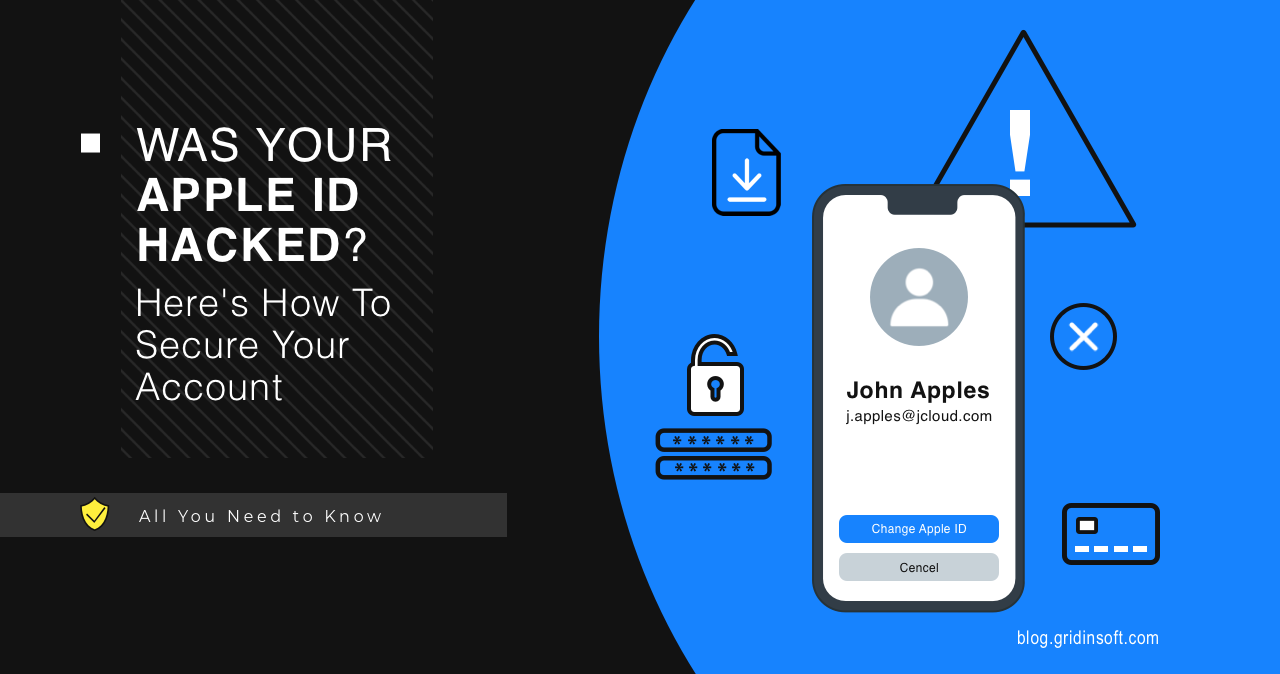
Was Your Apple ID Hacked? Here’s How To Secure Your Account
Apple's services and products are only accessible through their walled garden. Users…
Windows 7 Extended Security Update Program cancelled
On January 8, 2023, Microsoft announced the cancellation of the ESU program…
Web Application Firewall: Difference Blocklist and Allowlist WAFs
You may have come across a Web Application Firewall (WAF) concept but…
Dangerous Virus & Malware Threats in 2023
Virus and malware threats are constantly evolving and become more sophisticated and…
Security Breach
A security breach is an unauthorized access to a device, network, program,…
Browser Cookies Definition And Most Significant Types
Cookies are an essential part of how the Internet works. They help…