The Twitter account of Google’s Mandiant cybersecurity service has been hacked to promote a cryptocurrency scam. It happens along with the massive spread of cryptocurrency drainer scams on different social media platforms. Mandiant has lost control of its X/Twitter account Early this morning Eastern Time, cybersecurity company Mandiant’s account on the social network X (formerly… Continue reading Mandiant Account in X Hacked to Spread Cryptocurrency Scams
Author: Stephanie Adlam
I write about how to make your Internet browsing comfortable and safe. The modern digital world is worth being a part of, and I want to show you how to do it properly.
Qualcomm RCE Vulnerabilities Expose Millions of Users
Vulnerability in several Qualcomm chipsets allows for remote code execution during the phone call. This and other vulnerabilities were uncovered in the latest security bulletin released by the chipmaker. The optimistic part here is that the company uncovered the flaws half a year ago, and arranged the fixes with the OEMs. RCE Vulnerability In Qualcomm… Continue reading Qualcomm RCE Vulnerabilities Expose Millions of Users
Black Basta Ransomware Free Decryptor Available
SRLabs researchers published a free decryptor for BlackBasta ransomware. They discovered the vulnerability in the way malware handles the encryption process and found the way to recover the encryption key and get the files back. The decryptor is called Black Basta Buster and is available for free on the devs’ GitHub page. Black Basta Decryptor… Continue reading Black Basta Ransomware Free Decryptor Available
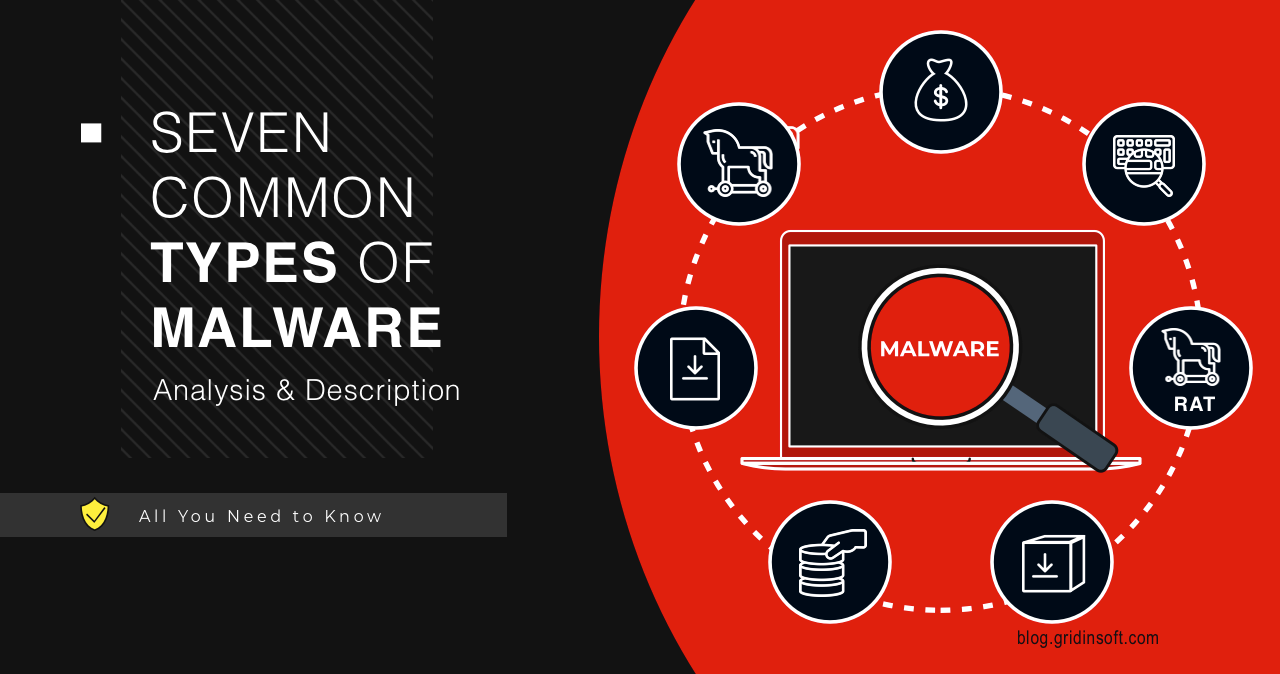
Seven Common Types of Malware – Analysis & Description
In the intricate landscape of cybersecurity, comprehending the various forms of malware is crucial. This article offers an in-depth look at the most pervasive malware types, from Loaders to Keyloggers. We’ll explore their mechanisms, impacts, and how they compromise digital security, providing you with the knowledge to better safeguard against these ever-evolving cyber threats. Let’s… Continue reading Seven Common Types of Malware – Analysis & Description
DLL Search Order Hijacking Technique Bypasses Protection
A new DLL (Dynamic Link Library) Search Order Hijacking variant emerged. This method capitalizes on executables in the trusted WinSxS folder of Windows 10 and 11, allowing threat actors to execute malicious code without needing high privileges. How Does DLL Search Order Hijacking Work? Researchers detect a novel DLL search order hijacking variant. It leverages… Continue reading DLL Search Order Hijacking Technique Bypasses Protection
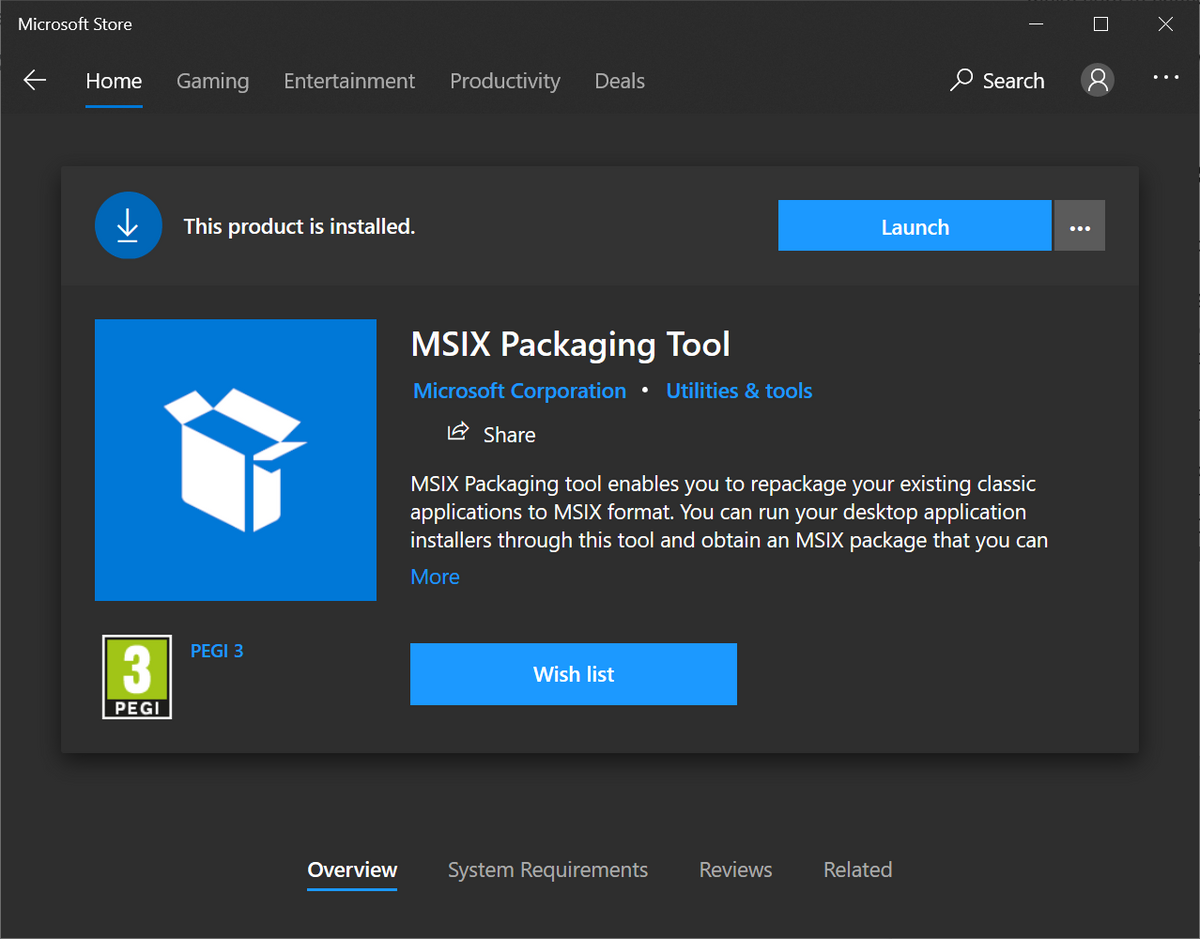
Microsoft Disables MSIX App Installer Protocol
Microsoft reportedly disabled MSIX installer protocol in Windows, due to its exploitation in real-world cyberattacks. Hackers found a way to misuse the protocol to install malicious software, bypassing anti-malware software detection. MSIX Installer Protocol Exploited The emergence of a malware kit market, exploiting the MSIX file format and ms-app installer protocol is nothing new. However,… Continue reading Microsoft Disables MSIX App Installer Protocol
PUABundler:Win32/PiriformBundler
PUABundler:Win32/PiriformBundler is the detection of an unwanted program, developed and issued by Piriform Software. While applications from this developer aren’t inherently malicious, the bundled software they carry and their questionable behavior make them less than desirable. What is PUABundler:Win32/PiriformBundler? PiriformBundler is a detection name for unwanted software developed by Piriform. Microsoft assigns such names to… Continue reading PUABundler:Win32/PiriformBundler
Novice Rugmi Loader Delivers Various Spyware
The threat landscape meets a new player – Rugmi Loader. This threat specializes in spreading spyware, and is in fact capable of delivering any malware type. Rugmi boasts of its unusual structure, which makes it rather promising among other loaders. What is Rugmi Loader? The Rugmi is a complex loader with multiple components that deliver… Continue reading Novice Rugmi Loader Delivers Various Spyware
Xamalicious Trojan Hits Over 327K Android Devices
A new Android backdoor, dubbed Xamalicious, was discovered by the researchers at the edge of 2023. This malware exhibits potent capabilities to perform malicious actions on infected devices. Malware reportedly exploits Android’s accessibility permissions to gain access to various sources of user data. What is Xamalicious Malware? As I’ve said in the introduction, Xamalicious is… Continue reading Xamalicious Trojan Hits Over 327K Android Devices
Integris Health Hacked, Patients Receive Ransom Emails
Integris Health, Oklahoma’s most extensive not-for-profit health network, fell victim to a sophisticated cyberattack, which compromised susceptible patient data. This unfortunate occasion got some really unusual results: patients of Integris Health in Oklahoma started receiving extortion emails. They threaten the sale of their data to other malicious actors if they fail to pay an extortion… Continue reading Integris Health Hacked, Patients Receive Ransom Emails