Almoristics Application is a devious crypto miner that’s causing headaches for countless Windows users. It’s definitely not a legitimate Windows process – just a parasite designed to mine cryptocurrency while you wonder why your computer’s fans sound like they’re preparing for takeoff. You’ll typically spot it in Task Manager with a suspicious heart-shaped icon, looking deceptively innocent while it drains your system resources.
Almoristics Application (AlmoritsticsService) Overview
This freeloader (also called Almoristics Service) belongs to the family of crypto-mining Trojans that have been making the rounds lately. Think of it as an unwelcome roommate who moved in without permission and is now running a bitcoin mining operation from your living room.
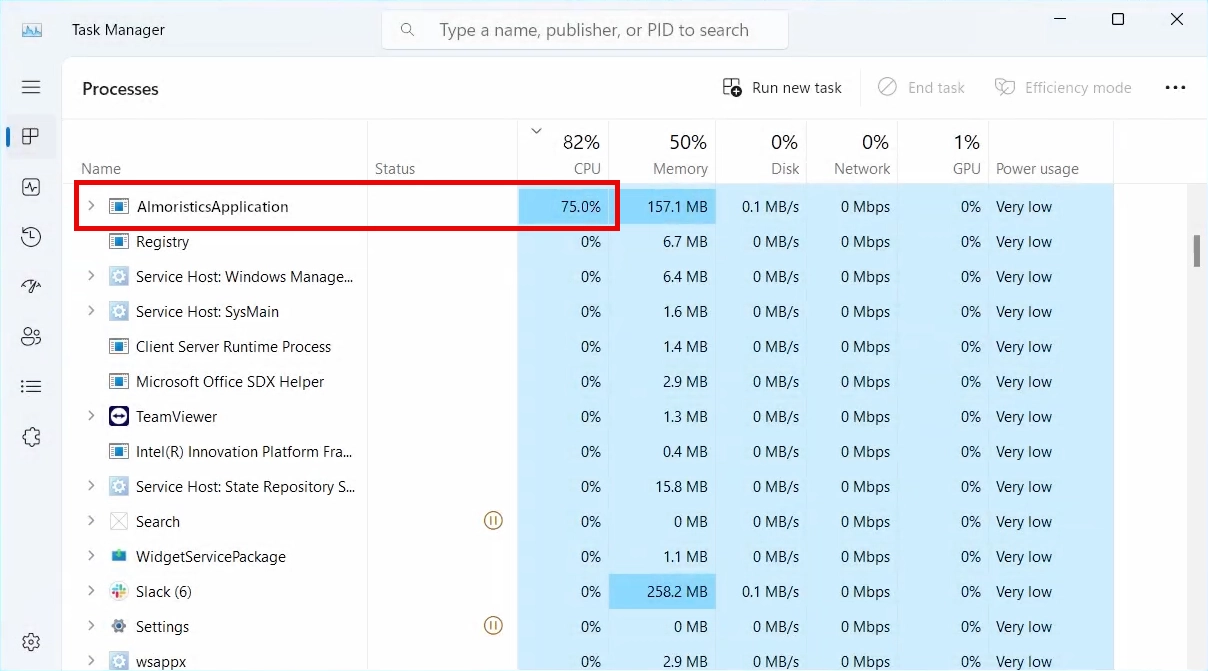
Your first clue that something’s wrong? Your CPU usage shoots through the roof, and your computer starts moving like it’s wading through molasses. The fan noise alone might make you think your laptop is planning to achieve liftoff. Meanwhile, your electricity bill climbs while this uninvited guest mines Monero or other cryptocurrencies for someone else’s wallet.
Technical Details
Almoristics Application is essentially the new kid on the block in a family of similar threats like Altruistics or Alrustiq App. These application hijack your computer’s processing power to mine cryptocurrencies like Monero or Zcash. The attackers pocket the profits while you’re left with the computing equivalent of a car running on fumes.
This malware typically sneaks in disguised within software from sketchy sources – that “free” version of expensive software from a dubious website probably wasn’t such a bargain after all. Once it makes itself at home, the cryptojacking begins, with CPU usage often spiking to a system-crippling 80%.
Beyond just mining, this virus might also modify system settings and create backdoors for even more unwelcome visitors. To avoid detection, it plays dress-up with various aliases like Alrisit, Altisik, or AltrsikApplication – making it trickier for your antivirus to catch.
How Did I Get Infected?
Let’s be honest – Almoristics doesn’t teleport onto your system by magic. The most common infection route is through bundled downloads – it hitchhikes alongside “free” software, game mods, or key generators from questionable websites. That moment when you rapidly clicked “Next” during installation without reading the fine print? That’s when you likely invited this resource vampire inside.
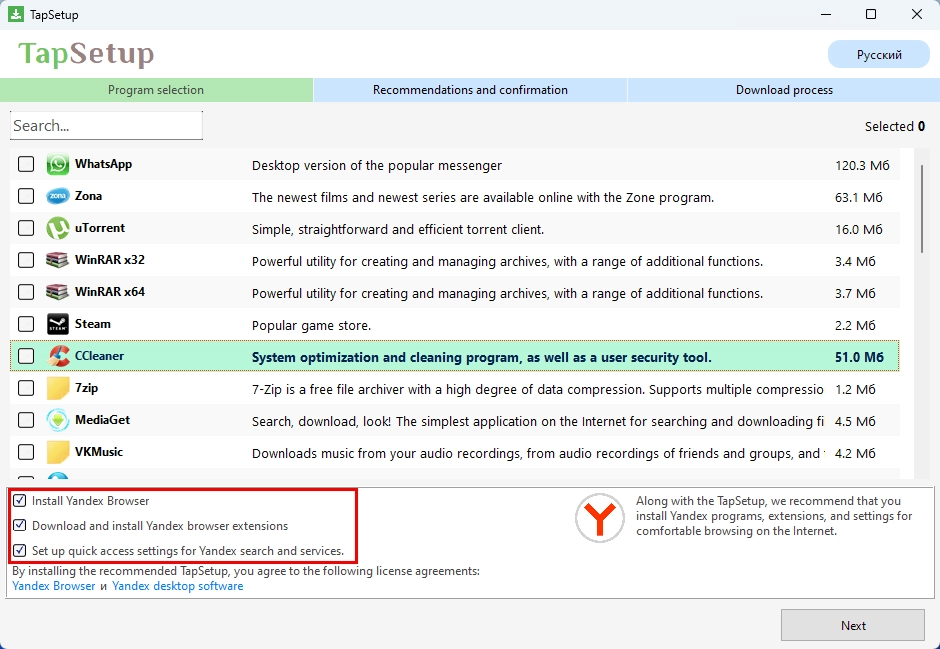
Other common infection vectors include spam emails with malicious attachments or deceptive links. Those suspicious “YOU WON’T BELIEVE WHAT HAPPENED NEXT” ads on sketchy websites can also trigger automatic downloads. Outdated software with unpatched vulnerabilities makes infection even easier, which is why Windows 7 and 8 users are particularly vulnerable targets.
How To Remove It?
Getting rid of Almoristics requires a systematic approach since it tends to dig in and resist casual removal attempts. First, boot into Safe Mode with Networking (check out how to get into safe mode here if you need guidance). This limits what processes can run, preventing the malware from overwhelming your system during the cleanup operation.
Next, run a full system scan with a reliable anti-malware program like GridinSoft Anti-Malware, which can detect and remove all the files, folders, and registry keys associated with this trojan virus. The cleanup might take some time if there are numerous infections, but patience pays off when you get your computer performance back.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.

Real-World Encounters with Almoristics
Reddit users have been sharing their battle stories with this crypto-mining invader, and it’s not pretty. One user reported that Almoristics was chewing through a staggering 95% of their CPU resources, turning their gaming PC into what they described as “an expensive space heater that can’t even run Notepad properly.” Several others noticed their GPUs were also being hijacked, making graphics-intensive tasks nearly impossible.
What makes Almoristics particularly sneaky is its persistence mechanisms. If you simply try to end the task in Task Manager, it’ll often respawn within seconds. Some Reddit users report that the malware creates scheduled tasks and registry autorun entries with random names, making manual removal a frustrating game of whack-a-mole. One technically-savvy user even discovered the malware injecting itself into legitimate Windows processes to avoid detection.
Interestingly, Almoristics seems to have some self-preservation instincts built in. Multiple users have observed that it can detect when Task Manager is opened and temporarily reduce its resource usage to avoid drawing attention. Once you close Task Manager, it ramps back up to full mining capacity. It’s like watching a cockroach play dead when the lights come on, only to scurry away when you turn your back.
This malware variant has also been linked to performance issues beyond mere slowdowns. Several Reddit users mentioned experiencing thermal throttling as their CPUs reached dangerous temperatures, and a few even reported system crashes when their cooling systems couldn’t keep up with the constant 100% load. One particularly unfortunate user claimed their relatively new laptop’s battery life plummeted from 6 hours to less than 45 minutes after infection.
After removal, you’ll notice an immediate performance improvement – your CPU usage will drop back to normal levels, your fans will stop screaming, and your computer will respond like it should. Think of it as evicting that cryptomining squatter who was draining your resources and electricity.
Want to stay protected from future infections? Keep your operating system and software updated, be cautious about what you download and from where, and maintain a healthy suspicion of “too good to be true” offers for free premium software. Remember, in the modern world as in life, if you’re not paying for the product, you might be the product – or in this case, your computer’s processing power might be.





