If you’re seeing cryptocurrency mining malware detected by your antivirus, don’t panic. Your Windows 11 computer is running slow. The CPU fan won’t stop spinning. You see processes eating up your system resources.
This guide will help you remove these threats completely. Follow these step-by-step instructions to eliminate the threat. We’ll start with methods you can try right now.
Cryptocurrency mining malware hijacks your computer’s power to mine digital currencies. Criminals use your machine to make money. The good news? You can get rid of these threats and fix your computer’s performance.
| Detection Name | Cryptocurrency Mining Malware / Cryptojacking |
| Threat Type | Resource Hijacking Malware |
| Primary Function | Mines cryptocurrency using infected computer’s resources |
| Common Sources | Malicious websites, infected downloads, email attachments, cracked software |
| Risk Level | HIGH – Causes system damage, excessive power consumption, and hardware wear |
Understanding Cryptocurrency Mining Malware
Cryptocurrency mining malware is different from other threats. It doesn’t steal your data or show ads. Instead, it turns your computer into a money machine for criminals.
These programs usually target Monero (XMR) because it’s harder to trace than Bitcoin. Common mining malware includes XMRig, CoinMiner, and browser-based scripts. They often come bundled with unwanted programs or through malicious websites.
Signs Your System is Infected
Here’s how to tell if you have mining malware:
- Slow performance – Apps take forever to load
- High CPU usage – Task Manager shows 80-100% processor use
- Overheating – Your computer gets hot and fans run constantly
- System crashes – Blue screens or sudden shutdowns
- Higher electricity bills – More power consumption
- Slow internet – Network miners use your bandwidth
Manual Removal Steps
Manual removal takes time and attention. Follow these steps carefully. Save your work first. You’ll need to restart your computer several times.
Step 1: Boot into Safe Mode
Safe Mode stops most malware from running. Here’s how to get there:
- Press Windows key + R
- Type msconfig and press Enter
- Click the Boot tab
- Check Safe boot and select Network
- Click OK and restart
Alternative method: Hold Shift while clicking Restart from the Start menu. Go to Troubleshoot > Advanced options > Startup Settings > Restart. Choose Safe Mode with Networking.
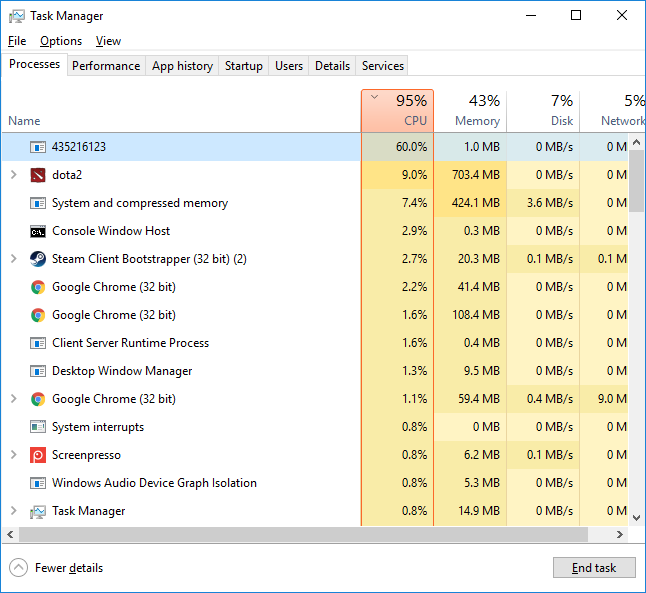
Step 2: Find Malicious Processes
Open Task Manager in Safe Mode. Look for processes using lots of CPU. Miners often use fake names but show high CPU usage.
- Press Ctrl + Shift + Esc
- Click the Processes tab
- Click CPU to sort by usage
- Look for these suspicious names:
- xmrig.exe or variations (xmr-stak.exe, xmrig-amd.exe)
- coinminer.exe or similar names
- Random characters (like “jhds8f9a.exe”)
- Processes with no description using lots of resources
- Multiple instances of the same process
Right-click suspicious processes and select “End task”. Write down the file locations. You’ll need them later.
Step 3: Delete Malicious Files
After finding malicious processes, delete their files. Check these common locations:
System Directories:
- C:\Windows\System32\
- C:\Windows\SysWOW64\
- C:\Windows\Temp\
- C:\ProgramData\
User Directories:
- C:\Users\[Your Username]\AppData\Local\
- C:\Users\[Your Username]\AppData\Roaming\
- C:\Users\[Your Username]\AppData\Local\Temp\
- C:\Users\[Your Username]\Documents\
Look for recently created files with suspicious names. Delete the files you found in Step 2. Be careful not to delete legitimate system files. When in doubt, research the file name online first.
Step 4: Clean Startup Programs
Mining malware often starts automatically with Windows. Remove them from startup:
Using Task Manager:
- Open Task Manager (Ctrl + Shift + Esc)
- Click Startup tab
- Look for suspicious entries
- Right-click and select Disable
- Note the file location
Using System Configuration:
- Press Windows key + R, type msconfig
- Click Startup tab
- Uncheck suspicious entries
- Click Apply and OK
Step 5: Registry Cleanup
Advanced users can clean the Windows Registry manually:
- Press Windows key + R, type regedit
- Go to these locations and look for suspicious entries:
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
Delete registry entries that reference the malicious files you found. Like other malware removal, registry cleaning needs careful attention.
Step 6: Check Scheduled Tasks
Some mining malware uses Windows Task Scheduler:
- Press Windows key + R, type taskschd.msc
- Expand Task Scheduler Library
- Look for recently created tasks with suspicious names
- Check the Actions tab to see what programs they run
- Delete tasks that reference your malicious files
Automatic Removal with GridinSoft Anti-Malware
Manual removal can be complex and time-consuming. For a faster, more reliable solution, GridinSoft Anti-Malware offers automatic detection and removal of cryptocurrency mining malware. Professional anti-malware software can find hidden components and registry changes that you might miss.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.

Browser-Based Mining Cleanup
Browser-based mining has gotten smarter. Some miners work entirely in your web browser without installing files. These need special cleanup steps.
How to Spot Browser-Based Miners
Look for these signs:
- Websites that immediately spike your CPU usage
- Browser tabs that stay active even when closed
- Background processes in browser task managers
- Ads that eat up system resources
Remove Malicious Browser Extensions
Google Chrome
- Launch the Chrome browser.
- Click on the icon "Configure and Manage Google Chrome" ⇢ Additional Tools ⇢ Extensions.
- Click "Remove" next to the extension.
If you have an extension button on the browser toolbar, right-click it and select Remove from Chrome.
Mozilla Firefox
- Click the menu button, select Add-ons and Themes, and then click Extensions.
- Scroll through the extensions.
- Click on the … (three dots) icon for the extension you want to delete and select Delete.
Microsoft Edge
- Launch the Microsoft Edge browser.
- Click the three dots (…) menu in the top right corner.
- Select Extensions.
- Find the extension you want to remove and click Remove.
- Click Remove again to confirm.
Alternatively, you can type edge://extensions/ in the address bar to access the extensions page directly.
Opera
- Launch the Opera browser.
- Click the Opera menu button in the top left corner.
- Select Extensions ⇢ Manage extensions.
- Find the extension you want to remove and click the X button next to it.
- Click Remove to confirm.
Alternatively, you can type opera://extensions/ in the address bar to access the extensions page directly.
Reset Your Browser
If you think you have browser-based mining malware, reset your browser completely:
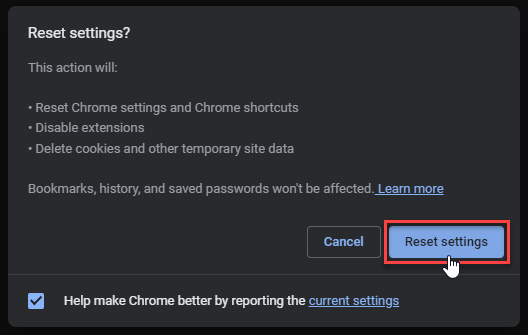
Google Chrome
- Tap on the three verticals … in the top right corner and Choose Settings.
- Choose Reset and Clean up and Restore settings to their original defaults.
- Tap Reset settings.
Mozilla Firefox
- In the upper right corner tap the three-line icon and Choose Help.
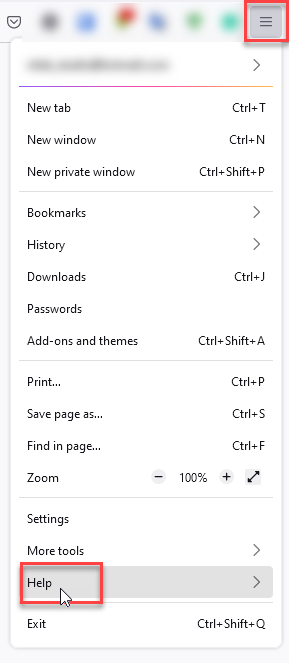
- Choose More Troubleshooting Information.
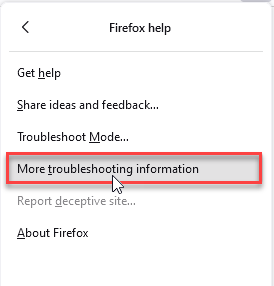
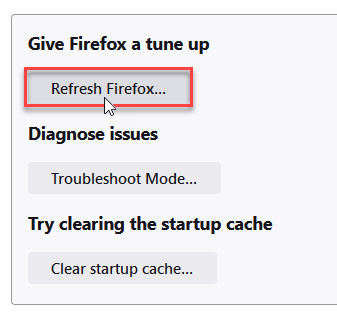
- Choose Refresh Firefox… then Refresh Firefox.
Microsoft Edge
- Tap the three verticals.
- Choose Settings.
- Tap Reset Settings, then Click Restore settings to their default values.
Opera
- Launch the Opera browser.
- Click the Opera menu button in the top left corner and select Settings.
- Scroll down to the Advanced section in the left sidebar and click Reset and clean up.
- Click Restore settings to their original defaults.
- Click Reset settings to confirm.
Alternatively, you can type opera://settings/reset in the address bar to access reset options directly.
After resetting, avoid the websites that infected you. Be careful with suspicious ads. Consider using ad-blocking software.
How to Prevent Mining Malware
Prevention is easier than removal. Follow these steps to protect your Windows 11 system:
System Security
- Update Windows – Install security patches quickly
- Use antivirus – Keep real-time protection on
- Enable Windows Defender – Keep Microsoft’s security features active
- Scan regularly – Run weekly full system scans
Safe Browsing
- Avoid suspicious websites – Be careful with sites offering free stuff
- Use ad blockers – Install good ad-blocking extensions
- Don’t click suspicious ads – Avoid popup advertisements
- Verify downloads – Only download from official sources
Email and Download Safety
Many miners come through email or downloads. Be careful with:
- Email attachments – Never open attachments from unknown senders
- Cracked software – Pirated software often contains malware
- Free software – Research unfamiliar apps before installing
- USB devices – Scan external devices before using
Network Security
- Secure WiFi – Use WPA3 encryption at home
- Avoid public WiFi – Don’t do sensitive work on public networks
- Update router – Keep firmware updated, change default passwords
- Use firewall – Enable Windows Firewall
Monitor Your System
Check your system regularly to catch mining malware early:
- Watch CPU usage – Check Task Manager for unusual activity
- Monitor temperature – Use tools to track hardware temperatures
- Check network activity – Look for unexpected bandwidth usage
- Notice power consumption – Watch for increases in electricity use
Frequently Asked Questions
What is cryptocurrency mining malware and why is it dangerous?
Cryptocurrency mining malware secretly uses your computer to mine digital currencies for criminals. It’s dangerous because it can damage your hardware through overheating, increase electricity bills, slow your system, and open doors for other malware. Unlike viruses that destroy data, miners focus on using resources, which can destroy hardware components.
How did mining malware get on my Windows 11 computer?
Mining malware usually arrives through email attachments, infected downloads (especially cracked software), malicious websites, bad browser extensions, infected USB drives, or bundled with software from untrusted sources. The malware often exploits browser vulnerabilities or tricks users into downloading infected files.
Can I remove mining malware manually?
Yes, manual removal is possible. This guide shows you how. But manual removal needs technical knowledge and careful attention. You’ll need to find malicious processes, delete files, clean registry entries, and remove startup programs. It works, but it takes time and might miss advanced threats.
Is it safe to delete high CPU processes in Task Manager?
Be very careful when ending processes in Task Manager. Only end processes you can identify as malicious. Some legitimate Windows processes use high CPU during normal operations (like updates or maintenance). Research unfamiliar process names online first. When in doubt, use anti-malware software.
How can I prevent mining malware?
Use multiple security layers: keep Windows 11 updated, use good antivirus with real-time protection, avoid untrusted software downloads, be careful with email attachments, use ad-blocking software, avoid suspicious ads, and monitor your system performance regularly. Most importantly, never download cracked software or visit suspicious websites.
What if manual removal doesn’t work?
If manual removal fails, use professional anti-malware software like GridinSoft Anti-Malware. Some mining malware uses advanced techniques like rootkits or distributed infections that are hard to remove manually. Professional tools have special detection engines for these threats. You might need to reinstall Windows in extreme cases.
Will removing mining malware damage my computer?
Proper removal shouldn’t damage your computer or delete personal files. However, some malware might have corrupted system files. Always backup important data before starting removal. If you’re unsure about any step, use automatic removal tools or ask a computer technician for help.
How do I know if my computer is completely clean?
After removal, watch your system for several days. CPU usage should be normal (under 20% when idle), system temperature should drop, fan noise should reduce, and performance should improve. Run multiple scans with different security tools. If you still have high CPU usage, heat, or slow performance, the malware might still be there.
Conclusion
Cryptocurrency mining malware is a serious threat to Windows 11 systems. It can damage your hardware and kill your computer’s performance. But with the removal techniques in this guide, you can eliminate these threats and get your computer back to normal.
Remember: prevention beats removal. Follow safe computing practices, keep your system updated, and use active security protection. You can avoid most mining malware this way. If you do get infected, the manual steps here will help you remove it. GridinSoft Anti-Malware offers automatic removal for complex infections.
Stay alert about your system’s performance. Take action if you notice signs of mining malware. The sooner you act, the less damage it can cause and the easier it is to remove. Regular monitoring and good security practices will keep your Windows 11 computer running smoothly.
For more protection against new threats, check out other malware protection strategies and stay informed about cybersecurity developments.
Quick Summary: Cryptocurrency Mining Malware Removal
- Manual removal: Boot into Safe Mode, identify malicious processes, delete files, clean startup programs, and edit registry
- Automatic removal: Use GridinSoft Anti-Malware for comprehensive detection and removal
- Browser cleanup: Remove malicious extensions and reset browser settings
- Prevention: Keep Windows updated, use antivirus, avoid suspicious downloads and websites
- Monitor system: Watch CPU usage, temperature, and network activity for early detection
Samples of Cryptocurrency Miners
- Risk.Win32.CoinMiner.dd!n: a44213af04ae1d80e167b0dce25e9fa8d1f93144196a1918db513d541767ffaa
- Trojan.Win64.CoinMiner.ca: 40cb10da51be47280083008184649a2505d40b01c066321f3c6973d5bd760929
- Worm.Win32.Miner.cld: 9194b57673209c8534888f61b0cdefa34f463ae50cd78f72ab2b3348220baaf9
- Trojan.Win32.CoinMiner.ns: 0dd4434fe34de41c317a14592a1b6a3dcc4eb7450125cfa6f843caddfb2337fa
- Trojan.Win64.CoinMiner.ca: 2b0146bc831b7c54b5527ea8c26a9153f410ec5efce19bb97499ffc9fd29d4b3
- Ransom.Win32.Miner.cld: 7a01de7e472fa80b6a50eac2c220dedf506dd2e33ef6ec3dc92a4395f4a8bd2b
- Trojan.Win32.CoinMiner.vb: 205c04a83a4294a06fb87d6037df1d0fbda876493269fbb58a8d697242b695cc
- Trojan.Win32.CoinMiner.ns: 27faca387d9a8e5c7e43366b3eb4e0e108c9bc1bbfade960a7a41eb134f0eae0
- Trojan.Win32.CoinMiner.vl!n: c3a9737d588c0787ea77bb7a967617ed8560fbacbf003880d74ffca10ea5607b
- Trojan.Win64.CoinMiner.cl: 445fdd57f58b973d5a583229b51d47da6dd99e510b44d96abb29932e994ba65a